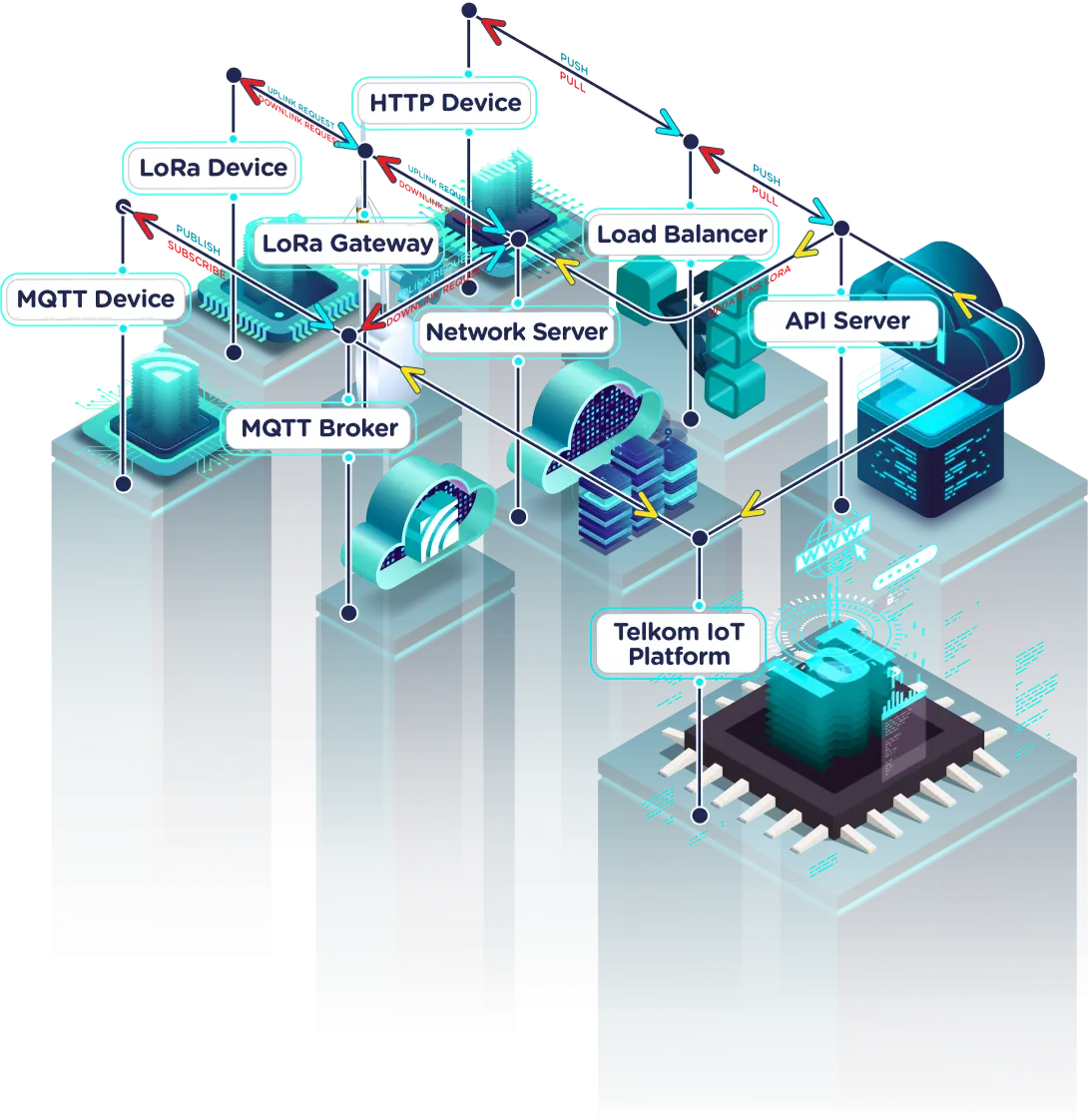
Connecting small devices to a central spot can feel a bit like setting up a new neighborhood watch. You want to make sure everyone who belongs can get in, and those who don't are kept out. When we talk about bringing together various internet-connected gadgets, often called the Internet of Things, or IoT, and keeping their communications safe, a particular method stands out. It's about using a familiar way to connect, a method that helps keep things private and protected, especially when these devices are out in the open or far away.
This approach helps people manage their smart home items, industrial sensors, or even little computers tucked away in different places. It provides a way to talk to these things as if you were sitting right in front of them, even when you are miles away. It’s about making sure the messages sent back and forth are not easily seen by just anyone, and that the devices themselves are who they say they are. In some respects, it’s like having a secret handshake for all your gadgets.
The goal is to create a dependable link, a kind of secure bridge, between you and your remote devices. This is important for checking on things, making changes, or getting updates without having to physically visit each item. It means you can stay in touch with your small electronics, making sure they are doing what they should, and that their information stays private. So, it's pretty helpful for keeping everything running smoothly.
- Adrian Martinez Twitter
- Red Hotwife Rose
- Ash Trevino Flash Santos Twitter
- Fit Kitty Twitter
- Iwdominate Twitter
Table of Contents
- Looking for the Right Setting in Your SSH IoT Platform?
- Password or Key - What's the Best Way to Get Into an SSH IoT Platform?
- Understanding the Connection Handshake for an SSH IoT Platform
- Why Do SSH IoT Platform Connections Sometimes Use Different Ports?
- Identifying Your Remote Devices in an SSH IoT Platform
- Dealing with Disconnecting SSH IoT Platform Sessions
- Keeping Your SSH IoT Platform Link Alive
- Scripting Automated Interactions with Your SSH IoT Platform
Looking for the Right Setting in Your SSH IoT Platform?
Sometimes, when you are trying to set up how your small devices talk to a central system, you look for a specific option. You might find a description of something that sounds just like what you need, a particular variable or setting that seems to fit the bill. Yet, you discover that this exact setting isn't quite right, or perhaps it is not even there at all in the system you are using. This can be a little frustrating, as a matter of fact.
It's like trying to find a specific tool in a toolbox, and you see a picture of it, but the actual tool isn't quite the same, or it's missing. This happens when you are trying to make things work in a certain way for your ssh iot platform. You might read about a feature, thinking it will solve a particular problem, only to find it behaves differently or is absent. This can mean you have to look for other ways to get the job done, which is pretty common.
The original idea for a variable might have been promising, suggesting it would give you the exact control you wanted. But then, when you check the actual system, you realize it doesn't quite match up. It's almost like the name suggests one thing, but its true purpose or availability is different. This can lead to a bit of a puzzle, trying to figure out how to achieve your goal without that particular piece of the puzzle.
This situation often comes up when you are dealing with different versions of software or slightly varied setups for your ssh iot platform. What works in one place might not be present in another. You might have to adjust your plans, finding a different path to reach the same outcome. It’s a common experience when you are working with these kinds of connections, trying to make everything fit together just right.
So, the search for that perfect setting can sometimes lead to a dead end, or at least a detour. It means you have to be ready to explore other options and be a little flexible in your approach. You might need to try a few different things before you find the one that truly works for your specific needs. This is just part of working with these kinds of systems, you know.
The hope was that a certain line or piece of information would make everything clear, providing the precise solution. However, it turned out that this piece of information, while interesting, didn't quite offer the direct answer or the exact functionality that was being sought. This can make the process of configuring an ssh iot platform a bit more involved than initially thought. It calls for a bit of detective work.
It suggests that while a particular concept or idea might be floating around, its practical application or explicit definition within the system might be lacking. This means you can't just point to a specific instruction and expect it to work. You might need to dig a little deeper or look for alternative methods to get your ssh iot platform to behave as you wish. That, in itself, can be a learning experience.
Finding that a variable you thought was key isn't quite what you expected, or isn't even set up, can change your approach. It means you might need to rethink how you are trying to manage your remote connections. Instead of relying on that one specific setting, you might need to combine other settings or use a different method entirely. This is often the case with these kinds of systems, as a matter of fact.
This challenge highlights the need for clear instructions and complete information when dealing with an ssh iot platform. When the documentation isn't entirely clear on how to use a particular feature, or if a variable isn't defined as expected, it adds extra steps to the process. It makes you wonder if there is a simpler way to do things, you know.
Ultimately, the search for that ideal variable shows that sometimes, what seems like a straightforward solution can turn out to be a bit more complicated. It requires patience and a willingness to explore different avenues to get your ssh iot platform to connect and operate exactly as you intend. It’s a common part of the process for many people.
Password or Key - What's the Best Way to Get Into an SSH IoT Platform?
When you want to get into a remote device, like one in your ssh iot platform, you usually have a couple of main ways to prove who you are. One way is to use a password, which is something many people are used to for logging into accounts. For some situations, just having a password might be perfectly fine, providing enough security for what you need to do. It's a simple, direct method, basically.
However, there's another common method, which involves using a pair of special digital files: a public key and a private key. The public key is like a lock that sits on the remote device, and the private key is the only key that can open it. People often prefer this method because it's considered very secure. But sometimes, it seems like the system might prevent you from adding your public key without some extra steps. This can make setting up key-based access a bit tricky, you know.
The instructions for how to use only that key, and nothing else, are not always easy to find or understand. It can feel a bit like trying to follow a recipe where some steps are missing. This lack of clear guidance can make it hard to set up your ssh iot platform connections exactly as you want them, especially if you prefer to rely solely on key pairs for access. It makes you wonder if there's a simpler explanation.
There are times when you might need to log into a device using a password, even if you usually use keys. This can happen if you are working with a new setup or if the key method isn't working for some reason. You might think it would be a simple switch, but sometimes, the system just doesn't want to use anything but a key. It's almost like it's stubborn about it, you know.
This preference for keys can be a good thing for security, but it can also be a little inconvenient when you are trying to do something quickly with a password. It means you might have to spend extra time figuring out why the system is insisting on a key when you just want to use a password for a quick check. This is a common point of confusion for many people dealing with an ssh iot platform.
So, while a password might seem like a straightforward option for your ssh iot platform, the system often nudges you towards using keys. This can be a bit of a hurdle if you are not used to managing key pairs or if the setup isn't clear. It's a trade-off between ease of use and a higher level of security, basically.
It's worth remembering that the system's behavior, like refusing passwords in favor of keys, is usually for a good reason, often related to keeping things safer. But that doesn't make it any less challenging when you are just trying to get something done. It requires a bit of patience to figure out the system's preferences, you know.
The idea that a simple password would be enough in some cases highlights a desire for straightforward access. However, the system's design, perhaps to keep things more secure, might put up barriers to using just a password, especially when key-based access is the default or preferred method. This can lead to a bit of a back-and-forth in trying to connect to your ssh iot platform.
When the instructions don't clearly show how to use only a specific key, it leaves room for guesswork. This means you might spend time trying different commands or settings to make sure your ssh iot platform connects using the key you intend, and only that key. It's a common area where people look for more explicit guidance.
The puzzle of why ssh might refuse a password when a key is present is a common one. It points to the system's built-in security features, which often prioritize the stronger key-based authentication. This means you often have to work within those parameters, even if it feels a little less flexible at times for your ssh iot platform connections.
Understanding the Connection Handshake for an SSH IoT Platform
When your computer or device tries to talk to another device, like a sensor in your ssh iot platform, they go through a kind of secret conversation. This conversation decides how they will protect their messages. It involves picking out specific ways to encrypt information, to check if messages have been changed, and to set up the initial secret codes for the chat. You might want to know exactly what methods your connection is using, you know.
It would be very helpful if you could just ask your connection tool, "Hey, what security methods are you supporting right now?" This way, you wouldn't have to look through complicated rule books or programming codes to find the answer. You'd want to find this information out dynamically, meaning on the fly, as you are trying to connect. This would make things a lot simpler, basically.
Knowing what encryption types, message integrity checks, and key exchange methods are being used is important for making sure your ssh iot platform connections are as secure as you need them to be. It helps you understand the strength of the protective bubble around your data. Without an easy way to see this, it can feel a bit like guessing what kind of lock is on the door.
The desire to see this information without digging through the system's inner workings suggests a need for more transparent tools. It would be great if the connection software could just tell you, "Here are the specific ways I'm able to secure this chat." This would save a lot of time and effort for anyone managing an ssh iot platform.
This ability to dynamically check what security features are in use would help in troubleshooting too. If a connection isn't working, knowing which security methods are being offered by both sides could quickly point to a mismatch. It’s a very practical thing to want, you know.
It’s about having a clear picture of the communication rules being established. When you connect to an ssh iot platform, these rules dictate how secure and private your interaction will be. Being able to see them instantly would offer a lot of peace of mind and control. It makes the process less of a mystery.
So, the idea is to have the connection software tell you directly about its capabilities. This means you wouldn't have to guess or look up old information. You would get the current details about what the ssh iot platform connection supports, right when you need it. That would be a truly helpful feature.
It’s like asking a translator what languages they speak, rather than having to read their entire resume. You just want the quick answer. This applies to the security protocols in an ssh iot platform connection too. You just want to know what it can do without a lot of extra effort.
The current situation often means you have to rely on external resources or deep system knowledge to figure out these details. Having the system itself provide this output would streamline the process significantly. It would make managing your ssh iot platform much more straightforward, you know.
Ultimately, the goal is to make the security handshake more visible and understandable. This would empower users to confirm the level of protection for their ssh iot platform connections without unnecessary fuss. It's about transparency in how the digital conversation is being secured, basically.
Why Do SSH IoT Platform Connections Sometimes Use Different Ports?
When you try to connect to a remote device, like a server that is part of your ssh iot platform, it usually has a special program running that listens for incoming connections. This program is often called 'sshd'. It waits for people to try to connect, and it listens on a specific number, which is called a port. The standard number for this kind of connection is 22, but it doesn't always have to be that one, you know.
Many people who manage these kinds of devices choose to move this listening number to something different, often a much higher number. They do this to reduce the amount of unwanted attention their device gets. Think of it like moving your front door to a less obvious spot on your house; fewer casual visitors might stumble upon it. This is a common practice for an ssh iot platform.
By changing the port from the usual 22 to something else, say 2222 or 22222, it makes it less likely for automated scanning tools to find the connection point. These tools often just check the standard port numbers first. So, if your ssh iot platform device isn't on the usual spot, it might get fewer attempts from those just looking for easy targets. It's a simple way to add a layer of obscurity.
This doesn't mean the connection is hidden from everyone, just that it's not as easily discovered by automated scans. Anyone who knows the specific port number can still try to connect. But for those just broadly looking, it cuts down on the noise. This can be a helpful strategy for keeping your ssh iot platform a bit quieter and less prone to constant probes. It's a bit like a secret knock.
The host, which is the remote device you are connecting to, will have its 'sshd' program running and ready to accept connections on whatever port it has been told to use. So, if you try to connect to the usual port 22 and it doesn't work, it might just mean the device is listening somewhere else. You'd need to know that different number to get in, you know.
This practice is fairly common in setups where security by obscurity is part of the plan. It's not the only security measure, of course, but it helps reduce the sheer volume of connection attempts. For an ssh iot platform, where devices might be numerous and spread out, this can be a practical way to manage traffic and reduce potential threats. It's a small but helpful step.
So, if you ever find yourself unable to connect to an ssh iot platform device on port 22, the first thing to consider is that it might be listening on a different, higher port. This is a deliberate choice by the server administrator to make it a little less obvious to unwanted visitors. It's a simple adjustment that can make a difference, you know.
It's a way of saying, "We're open for business, but only if you know our special entrance." This reduces the number of general knocks on the door. For devices in an ssh iot platform, which might not have a lot of processing power to deal with constant unwanted connection attempts, this can be quite beneficial. It helps them focus on their real tasks.
The choice to move the port is a proactive step to manage how much attention a server gets from the outside. It's not foolproof security, but it's a good initial filter. It's something to keep in mind when you are setting up or troubleshooting connections to your remote devices. That, in fact, can save you some time.
Ultimately, the goal is to make your ssh iot platform devices less of a target for casual scanning. By changing the default connection point, you're making it a little bit harder for automated systems to find them, which can lead to a more peaceful existence for your remote hardware. It's a simple trick, but it works for many people.
Identifying Your Remote Devices in an SSH IoT Platform
When you connect to a remote device, like one in your ssh iot platform, there's a way to make sure it's the device you intend to talk to and not some imposter. This is done using something called a "fingerprint." This fingerprint is a unique short code that comes from the device's public key. Think of it like a digital ID card for the device itself, you know.
This public key is usually found in a specific file on the device, often something like `/etc/ssh/ssh_host_rsa_key.pub`. This file holds the unique identity of that particular device. The fingerprint is just a shorter, easier-to-read version of that long key. It's created from that key, making it a dependable way to tell one device from another. It's pretty handy
Related Resources:
Detail Author:
- Name : Prof. Alexis Oberbrunner
- Username : tessie79
- Email : sandra68@gmail.com
- Birthdate : 1979-02-18
- Address : 760 Kling Radial Kileyside, MT 62858
- Phone : 740.495.6211
- Company : Gutmann PLC
- Job : Medical Laboratory Technologist
- Bio : Nemo molestiae eum natus adipisci et dolor maxime. Totam aut quos accusantium libero. Dolor doloremque veniam illum ipsum occaecati. Amet natus quisquam dolores ducimus veniam.
Socials
linkedin:
- url : https://linkedin.com/in/beulah.boehm
- username : beulah.boehm
- bio : Corporis qui quibusdam adipisci.
- followers : 5713
- following : 460
twitter:
- url : https://twitter.com/boehmb
- username : boehmb
- bio : Debitis earum tempore et eum dolor. Delectus consequatur ratione quae quis rem tenetur aliquid et. Nam non non ipsam beatae facere ipsum qui.
- followers : 1486
- following : 544
tiktok:
- url : https://tiktok.com/@boehmb
- username : boehmb
- bio : Aliquid eius sit illum amet velit iste.
- followers : 2160
- following : 156
facebook:
- url : https://facebook.com/beulah_boehm
- username : beulah_boehm
- bio : Animi qui omnis totam culpa sed similique. Saepe omnis est nesciunt quae quod.
- followers : 6477
- following : 375
instagram:
- url : https://instagram.com/beulahboehm
- username : beulahboehm
- bio : Rerum laudantium iusto odio nemo. Quod dolor et minima maxime. Veniam sunt id eum.
- followers : 616
- following : 2786