When you have smart gadgets and devices spread out, perhaps in different spots, making sure they talk to each other and to you without any unwelcome listeners is a pretty big deal. Getting your devices connected to a central spot, like a RemoteIoT Platform, means thinking about how you keep those connections private and sound. It's like having a special, secret handshake for each of your little machines so only the right people can get in and tell them what to do, or listen to what they have to say, you know?
This idea of keeping things secure isn't just for big companies with lots of equipment; it's something anyone with connected devices needs to think about. Whether you're watching temperatures in a faraway greenhouse or managing lights across a building, the way you connect to those devices and the information they send back has to be protected. It's all about making sure your smart setup works just for you and nobody else, which, as a matter of fact, gives you a lot of peace of mind.
That's where something called an SSH key comes into play, especially when you're working with a RemoteIoT Platform. It’s a really smart way to make sure that only your authorized devices and systems can chat with each other, keeping everything locked down tight. We're going to talk a bit about what these keys are, why they matter for your connected things, and how they help keep your RemoteIoT Platform setup running smoothly and safely, which is actually quite simple once you get the hang of it.
Table of Contents
- Why Think About Security for Your IoT Devices?
- What Even Is an SSH Key, Really?
- Getting Your RemoteIoT Platform SSH Key Ready
- Keeping Your RemoteIoT Platform SSH Keys Safe - Any Tips?
- A Little About Key Types and How They Work with RemoteIoT Platform
- Common Questions About RemoteIoT Platform SSH Key Use
- Making RemoteIoT Platform Access Simple and Secure
- Troubleshooting Your RemoteIoT Platform SSH Key Connections
Why Think About Security for Your IoT Devices?
You know, having smart devices around the house or in your business can be incredibly handy. They can do all sorts of things, from turning on your lights when you get home to keeping an eye on machinery in a factory. But just like you wouldn't leave your front door wide open, you really don't want to leave your smart devices unprotected either. Think about it – these little gadgets are often connected to the internet, and that connection can sometimes be a way for unwanted visitors to sneak in. So, keeping them safe is pretty important, as a matter of fact.
If someone gets access to your devices, they might do things you don't want, like mess with your settings, steal information, or even use your devices for their own purposes without you knowing. This is why having strong ways to protect these connections is so vital. It’s about building a solid fence around your digital property, making sure that only authorized people or systems can get close. This is especially true when you're using a RemoteIoT Platform to manage many devices at once, since one weak link could affect everything.
The RemoteIoT Platform and Your Keys
A RemoteIoT Platform is a central spot where all your smart devices can connect, send data, and receive instructions. It's like the main control center for your entire smart setup. For this control center to work well and safely, you need a reliable way to confirm that the devices connecting are actually yours, and that the commands you send are truly coming from you. This is where special digital keys come in, specifically the RemoteIoT Platform SSH key. They act like a unique digital signature, making sure every interaction is legitimate and private. It’s kind of like having a very specific key that only fits your own lock, which is quite reassuring.
What Even Is an SSH Key, Really?
When we talk about an SSH key, we're not talking about a physical key you can hold in your hand. Instead, it's a pair of digital files that work together to create a very secure connection between two computers or devices. One part is called the "private key," and you keep that secret, like a personal password you never share. The other part is the "public key," and you can share that one freely. These two pieces are mathematically linked, so if something is encrypted with the public key, only the matching private key can unlock it, and vice versa. It’s a clever system, honestly.
Imagine you want to send a secret message to a friend. You could give your friend a special lock (the public key) and keep the only key to that lock yourself (the private key). Your friend puts their message in a box, locks it with your special lock, and sends you the box. Only you, with your private key, can open the box and read the message. This is a bit like how SSH keys work for logging into systems or sending data securely. It's a very simple way to think about it, anyway.
How a RemoteIoT Platform Uses SSH Keys
For a RemoteIoT Platform, SSH keys are super useful because they provide a very strong way for your devices to connect without needing to type in a password every time. Passwords can be guessed or stolen, but SSH keys are much harder to compromise because they are long, complex, and work in pairs. When your device wants to talk to the platform, it uses its private key to prove its identity, and the platform uses the device's public key to verify it. This handshake happens automatically and very quickly.
This means your devices can securely send data, receive updates, or take commands from your RemoteIoT Platform without human intervention. It makes automation much safer and easier. For example, if you have a sensor out in a field, it can securely send its readings back to your platform using an SSH key, and you don't have to worry about someone else pretending to be your sensor or intercepting its data. It’s a very practical solution, you know?
Getting Your RemoteIoT Platform SSH Key Ready
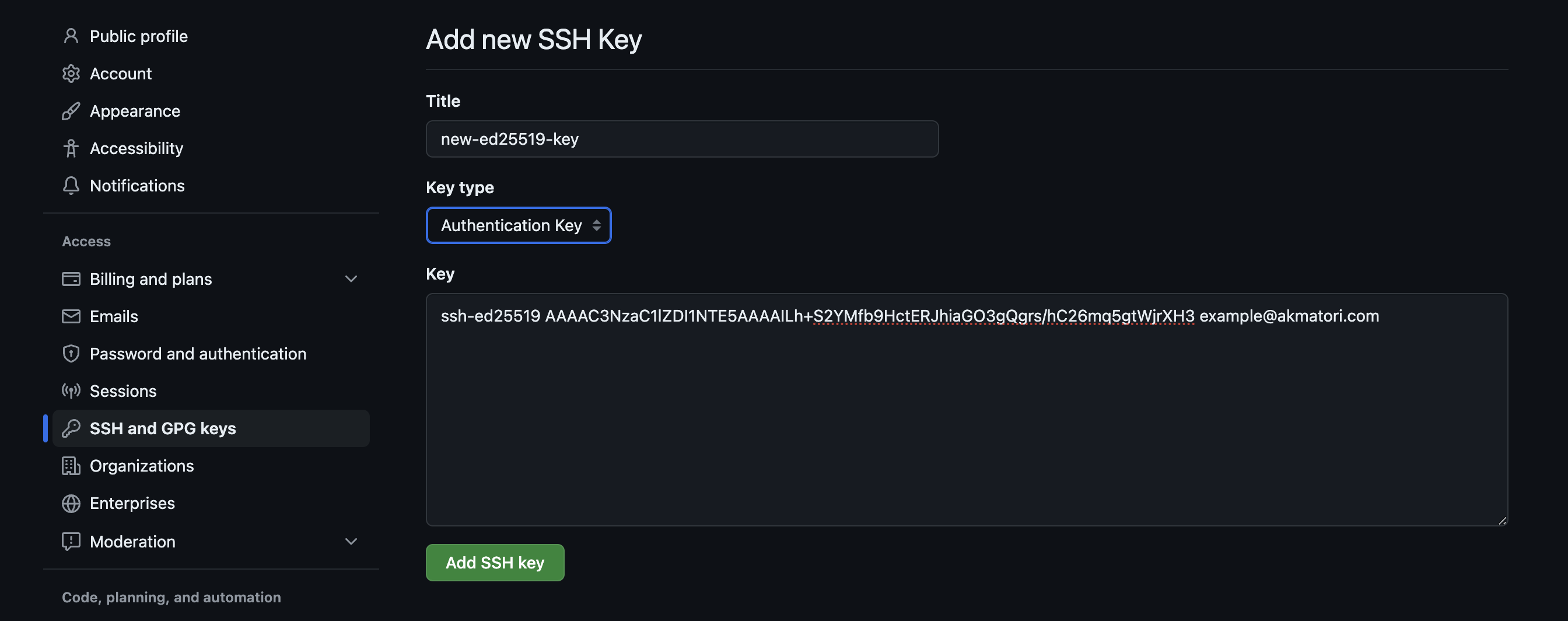
So, how do you actually get one of these SSH keys ready for your RemoteIoT Platform? It's usually a process that involves generating the key pair on your own computer. Most operating systems have built-in tools that can do this for you with just a few simple commands. You'll end up with two files: one for your private key (keep this very, very safe!) and one for your public key. The public key is the one you'll share with your RemoteIoT Platform so it knows to trust your connections.
Once you have your public key file, you'll typically copy its contents and paste them into a specific section within your RemoteIoT Platform's settings. The platform will then store this public key, essentially adding it to a list of "approved" keys. This tells the platform, "If a device tries to connect using the private key that matches this public key, let it in!" It’s a pretty straightforward setup, actually, and most platforms make it easy to do.
Putting Your RemoteIoT Platform SSH Key on Devices
After your RemoteIoT Platform has your public key, the next step is to make sure your actual devices have the corresponding private key. This is the part where your devices learn how to "authenticate" themselves to the platform. Depending on the type of device you have – whether it's a small sensor, a Raspberry Pi, or something else – the way you put the private key on it might vary a little. Sometimes you can upload it directly, or you might need to use a command line interface to place the file in the right spot.
It's super important that the private key stays only on the device it's meant for and that it's protected from unauthorized access. If someone gets hold of your private key, they could potentially pretend to be your device and gain access to your RemoteIoT Platform. So, making sure those private keys are secure on your devices is a big part of keeping your whole system safe. It's a bit like giving each device its own secret identity card, you know?
Keeping Your RemoteIoT Platform SSH Keys Safe - Any Tips?
Keeping your SSH keys safe is a lot like keeping your house keys safe – you wouldn't just leave them lying around for anyone to pick up. For your private SSH keys, this means making sure they are stored in a protected place on your computer or device. Many people use a "passphrase" to encrypt their private key, which adds another layer of protection. Even if someone gets the file, they still need the passphrase to use it. This is a very good habit to get into, basically.
Another good idea is to create different SSH key pairs for different purposes. So, you might have one key for your personal access to the RemoteIoT Platform, and separate keys for each of your devices. This way, if one key ever gets compromised, you only need to replace that one specific key, not your entire system's access. It helps keep things tidy and more secure, as a matter of fact, and less of a headache if something goes wrong.
What Happens If a RemoteIoT Platform SSH Key Goes Missing?
If you ever suspect that one of your RemoteIoT Platform SSH keys might have fallen into the wrong hands, or if a device that held a private key is lost or stolen, it's really important to act quickly. The first thing you should do is remove the corresponding public key from your RemoteIoT Platform. This tells the platform, "Don't trust any connections coming from a device using this key anymore." It's like changing the locks on your digital door.
After you've removed the old key, you'll need to generate a brand new SSH key pair and add the new public key to your RemoteIoT Platform. Then, any devices that need to connect will need to be updated with the new private key. It might sound like a bit of work, but it's a very important step to keep your system safe and sound. It’s just like getting new keys made after you lose your old ones, you know?
A Little About Key Types and How They Work with RemoteIoT Platform
When you generate an SSH key, you might notice there are different types, like RSA or ED25519. These names refer to the different mathematical ways the keys are created and how they work. While they all serve the same basic purpose of secure authentication, some types are considered more modern and offer stronger protection with shorter key lengths. Most RemoteIoT Platforms will support a few common types, so you usually have options.
For everyday use with your RemoteIoT Platform, any of the commonly recommended types will likely do a good job. The important thing is that you're using SSH keys at all, rather than relying on less secure methods like simple passwords. The specific type you pick is often less critical than how well you keep your private key a secret and how often you consider changing them out. It’s kind of like picking a sturdy lock for your door; the brand might differ, but the goal is the same, you know?
Common Questions About RemoteIoT Platform SSH Key Use
People often wonder if they need a separate SSH key for every single device connected to their RemoteIoT Platform. While it's certainly a good practice for maximum security, especially for devices that might be more exposed or critical, it's not always strictly necessary for every tiny sensor. For many setups, a single key pair might be used for a group of similar devices that share the same security needs. It really depends on your specific setup and how much risk you're comfortable with, you know?
Another common question is about how often you should change your SSH keys. There's no hard and fast rule, but many security experts suggest doing it periodically, perhaps once a year or so, especially for important keys. If you ever suspect a key might be compromised, or if a device is retired, that's definitely the time to replace or remove its key from your RemoteIoT Platform. It's just a good habit to keep things fresh, you know, like changing the oil in your car.
Making RemoteIoT Platform Access Simple and Secure
The whole point of using SSH keys with your RemoteIoT Platform is to make connecting to your devices both simple and very secure. Once you've set them up, the process of your devices talking to the platform becomes automatic and seamless. You don't have to manually log in to each device or worry about passwords getting exposed. This frees you up to focus on what your devices are actually doing, like collecting data or performing tasks, rather than constantly worrying about their security.
It's a foundational piece of keeping your entire smart device system running smoothly and safely. By taking the time to set up your RemoteIoT Platform SSH key pairs correctly and managing them with a little care, you're building a strong, reliable connection for all your devices. This allows your smart setup to do its job without unnecessary interruptions or security scares, which is pretty much what everyone wants, right?
Troubleshooting Your RemoteIoT Platform SSH Key Connections
Sometimes, even with the best intentions, things don't quite work as planned when setting up your RemoteIoT Platform SSH key connections. If your device isn't connecting, a common first step is to double-check that the public key on your RemoteIoT Platform exactly matches the one generated from your private key. Even a tiny typo can stop things from working. Also, make sure the private key file on your device has the right permissions, meaning only the device itself can read it. If the permissions are too open, the system might refuse to use it for security reasons.
Another thing to look at is the connection itself. Is your device online? Can it reach the RemoteIoT Platform's address? Sometimes the issue isn't with the key, but with the network path. Most platforms have logs that can give you hints about why a connection failed, so checking those can be very helpful. It's often just a small detail that needs adjusting, and once you find it, everything usually clicks into place. It’s a bit like finding a loose wire, you know?
This article has gone over the idea of SSH keys and how they fit into using a RemoteIoT Platform, talking about what they are, why they're important for keeping your smart devices safe, and how you go about getting them ready and putting them on your devices. We've also touched on keeping these keys safe, what to do if one goes missing, and some common questions people have about using them. The aim was to show how using a RemoteIoT Platform SSH key helps make your connected setup both simple to use and very secure, with a few tips on what to do if you run into connection issues.
Related Resources:

Detail Author:
- Name : Prof. Gilberto Funk PhD
- Username : emmerich.foster
- Email : korbin58@olson.com
- Birthdate : 1985-06-03
- Address : 196 Greyson Spur Apt. 637 Sydneyborough, KS 19973
- Phone : (283) 838-4776
- Company : Goodwin Ltd
- Job : Grinding Machine Operator
- Bio : Occaecati omnis quia perspiciatis placeat occaecati quo. Animi sunt ipsam natus molestias ipsam molestiae illo iste. Vel et unde saepe impedit voluptas occaecati. Iure provident rerum ullam incidunt.
Socials
twitter:
- url : https://twitter.com/cbergstrom
- username : cbergstrom
- bio : Quibusdam nobis in exercitationem possimus enim quisquam. Voluptatem laudantium pariatur qui pariatur unde.
- followers : 889
- following : 2755
linkedin:
- url : https://linkedin.com/in/bergstrom1987
- username : bergstrom1987
- bio : Enim tenetur quo non minima qui.
- followers : 937
- following : 1222
tiktok:
- url : https://tiktok.com/@claudie_bergstrom
- username : claudie_bergstrom
- bio : Qui natus dolores voluptatem maxime. Omnis dolores earum non officia.
- followers : 3782
- following : 906
facebook:
- url : https://facebook.com/claudie_bergstrom
- username : claudie_bergstrom
- bio : Necessitatibus voluptatem quia totam vel quaerat.
- followers : 2469
- following : 2930