In the ever-expanding universe of the Internet of Things (IoT), the ability to securely and efficiently manage devices from anywhere on the planet is no longer a luxury—it's a necessity. For tech enthusiasts, developers, and hobbyists alike, the Raspberry Pi has emerged as a cornerstone device for countless IoT projects. But how do you truly unleash its full potential when it's tucked away in a remote corner or deployed across a vast area? This is where the concept of a `remoteiot vpc review raspberry pi` becomes not just relevant, but absolutely critical.
If you're into remote access, IoT projects, or just want to geek out over Raspberry Pi setups, you're in the right place. Today, we’re diving deep into the innovative technology that bridges the gap between physical Raspberry Pi devices and seamless, secure remote control: the integration of RemoteIoT with a Virtual Private Cloud (VPC) and Secure Shell (SSH). This comprehensive `remoteiot vpc review focused on raspberry pi` aims to provide a detailed analysis of its functionality, setup process, and performance, ensuring you understand why this setup is a game-changer for your connected world.
Table of Contents
- The Core Concept: What is RemoteIoT VPC SSH on Raspberry Pi?
- Why Remote Access Matters for Your Raspberry Pi Projects
- Key Components of a RemoteIoT VPC Setup
- Setting Up Your RemoteIoT VPC SSH on Raspberry Pi: A Practical Guide
- Unpacking the Benefits: A Comprehensive RemoteIoT VPC Review
- Performance and Reliability in RemoteIoT VPC Environments
- Real-World Use Cases for RemoteIoT VPC with Raspberry Pi
- Overcoming Challenges and Best Practices
- Conclusion
The Core Concept: What is RemoteIoT VPC SSH on Raspberry Pi?
At its heart, `remoteiot vpc ssh raspberry pi` is essentially a setup that allows you to securely access and manage your Raspberry Pi devices remotely using SSH within a virtual private cloud. Think of it as creating a secure, private tunnel directly to your little computer, no matter where it is physically located. You’ve got a Raspberry Pi sitting on your desk, but you want to control it from anywhere in the world? That’s where RemoteIoT VPC SSH comes into play.
Let's break down the acronyms. "IoT" (Internet of Things) refers to the network of physical objects embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the internet. "Remote" simply means accessing something from a distance. "VPC" stands for Virtual Private Cloud, which is a private, isolated section of a public cloud where you can launch resources in a virtual network that you define. Finally, "SSH" (Secure Shell) is a cryptographic network protocol for operating network services securely over an unsecured network. It's the standard for secure remote login and command-line execution.
Combining these elements means you're not just connecting to your Raspberry Pi; you're doing so through a highly secure, configurable, and private network environment that protects your data and operations from the vulnerabilities of the public internet. This innovative technology bridges the gap between physical hardware and robust cloud infrastructure, offering unparalleled control and peace of mind.
Why Remote Access Matters for Your Raspberry Pi Projects
Getting your little computer, a Raspberry Pi, to do things when you're not right there with it, is a pretty cool idea. It's about being able to connect to it from a distance, maybe even from a different continent. The importance of remote access for Raspberry Pi in IoT projects cannot be overstated. Imagine deploying a network of environmental sensors powered by Raspberry Pis across a large agricultural field, or managing a smart home system while you're on vacation. Without remote access, every update, every troubleshooting step, and every data retrieval would require physical presence, which is often impractical, costly, and time-consuming.
- Lauren Cowling Twitter
- Alice Stewart Vaccine
- Flo Milli Twitter
- Jessica Black Twitter
- Russell Brand Twitter
Remote access empowers users to:
- Monitor and Control: Keep an eye on sensor data, control actuators, or simply check the status of your Pi from anywhere with an internet connection.
- Troubleshoot and Maintain: Diagnose issues, apply software updates, or restart services without needing to physically interact with the device. This is crucial for maintaining system uptime and reliability.
- Deploy and Scale: Easily set up and manage multiple Raspberry Pi devices across different locations, scaling your IoT infrastructure as needed without logistical nightmares.
- Develop and Iterate: Push new code, test applications, and iterate on your projects remotely, accelerating development cycles.
In essence, remote access transforms your Raspberry Pi from a desk-bound gadget into a truly distributed, powerful node in your IoT ecosystem. And when discussing IoT and remote VPC management, Raspberry Pi is the name that keeps popping up because it offers an accessible yet powerful platform for these advanced setups.
Key Components of a RemoteIoT VPC Setup
To truly appreciate the power of a `remoteiot vpc review raspberry pi`, it's essential to understand the individual components that make this robust system possible. Each element plays a crucial role in ensuring secure, flexible, and scalable remote access.
The Mighty Raspberry Pi: More Than Just a Tiny Computer
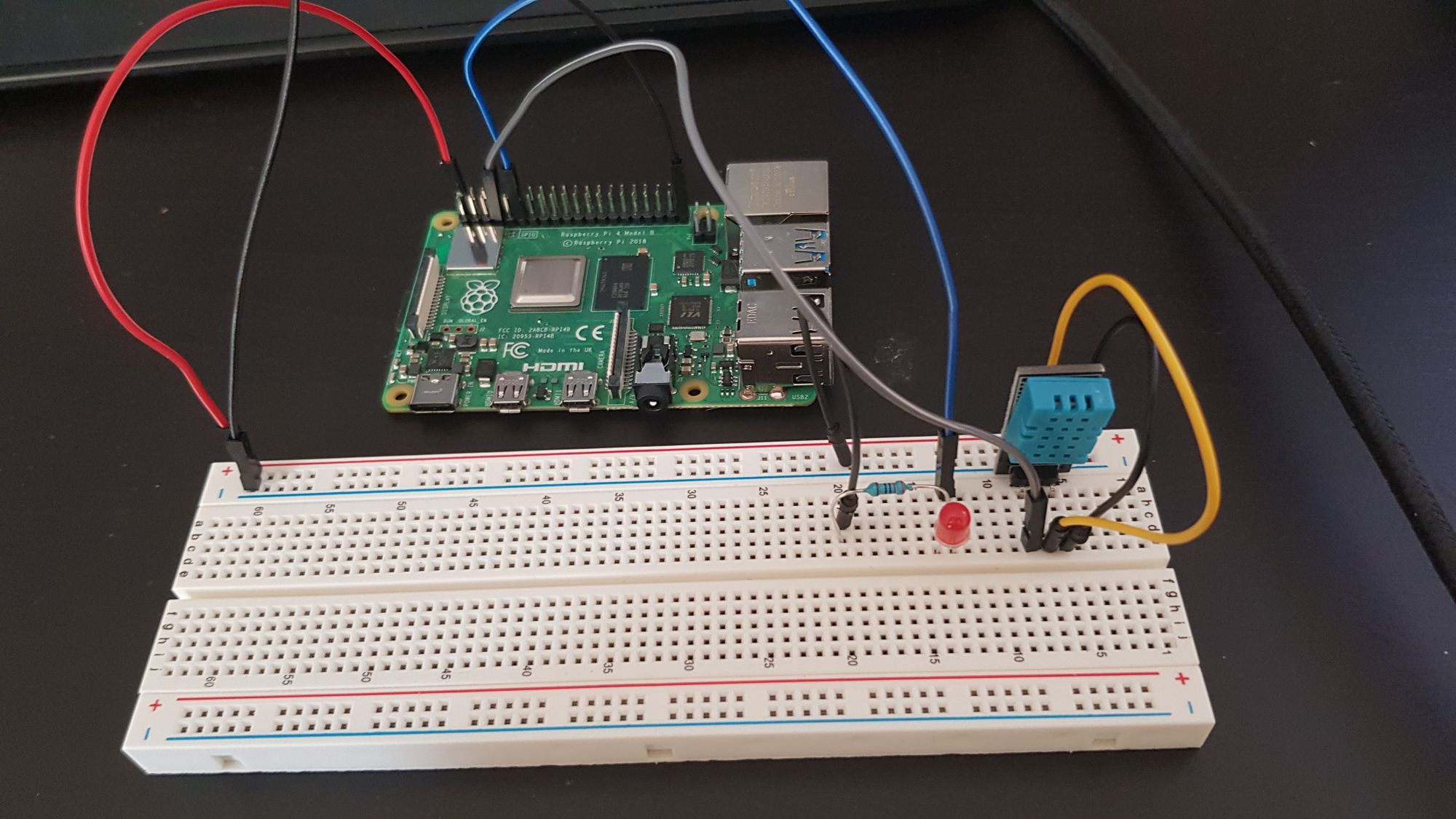
It’s not just a tiny device; it’s a powerhouse for tech enthusiasts who want to build, experiment, and deploy. The Raspberry Pi, despite its credit-card-sized form factor, boasts impressive processing power, versatile GPIO pins, and broad connectivity options (Wi-Fi, Bluetooth, Ethernet). This makes it an ideal candidate for a vast array of IoT applications, from simple home automation to complex industrial monitoring systems. Its low power consumption and affordability further cement its position as a go-to device for distributed computing tasks. For our `remoteiot vpc ssh raspberry pi` setup, it serves as the endpoint, the physical device that collects data, runs applications, and interacts with the real world.
Understanding Virtual Private Clouds (VPCs) for IoT
A Virtual Private Cloud (VPC) provides an isolated, private network environment within a public cloud infrastructure. Imagine a large apartment building (the public cloud) where you rent a specific apartment (your VPC). You have full control over who enters your apartment, how its rooms are arranged, and what services you set up inside, completely separate from other tenants. For IoT, a VPC offers:
- Network Isolation: Your Raspberry Pis and associated services operate in their own private network space, shielded from other users' traffic on the public cloud.
- Enhanced Security: You can define custom IP address ranges, subnets, route tables, and network gateways. This granular control allows you to implement strict security policies, such as inbound and outbound firewall rules (security groups and Network Access Control Lists - NACLs), to restrict access only to authorized sources.
- Scalability and Flexibility: As your IoT deployment grows, you can easily add more Raspberry Pis or other cloud resources within your VPC, scaling your network infrastructure without reconfiguring your entire setup.
- Hybrid Connectivity: VPCs can be seamlessly connected to your on-premises networks via VPN or direct connect, creating a truly hybrid environment for complex IoT solutions.
This isolation ensures that your data remains private and your devices are protected from external threats, embodying the principles of secure, flexible, and scalable remote access that will remain critical as IoT continues to expand its reach and complexity.
SSH: The Secure Gateway to Your Pi
Secure Shell (SSH) is the backbone of secure remote access to your Raspberry Pi within the VPC. It provides an encrypted connection between your client machine (e.g., your laptop) and your Raspberry Pi. This encryption ensures that all data transmitted, including commands, file transfers, and credentials, is protected from eavesdropping and tampering. Key features of SSH include:
- Strong Authentication: SSH supports various authentication methods, most commonly password-based authentication and public-key authentication. For enhanced security, public-key authentication is highly recommended, as it eliminates the need to transmit passwords over the network.
- Data Encryption: All communication over an SSH tunnel is encrypted, making it extremely difficult for unauthorized parties to intercept and read your data.
- Port Forwarding and Tunnelling: SSH can be used to securely tunnel other network services (like VNC, HTTP, or custom application ports) over the encrypted connection, allowing you to access graphical interfaces or web services running on your Pi securely.
Together, the Raspberry Pi, a carefully configured VPC, and the robust SSH protocol form a powerful triumvirate for a secure and efficient remote IoT management system. This `remoteiot vpc review raspberry pi` highlights how these components synergize to deliver a truly modern solution.
Setting Up Your RemoteIoT VPC SSH on Raspberry Pi: A Practical Guide
Embarking on the journey to set up `remoteiot vpc ssh raspberry pi` might seem daunting at first, but with a structured approach, it's a manageable and incredibly rewarding endeavor. The exact steps can vary slightly depending on your chosen cloud provider (e.g., AWS, Azure, Google Cloud), but the fundamental principles remain consistent. This guide provides a general overview of the process.
- Prepare Your Raspberry Pi:
- Install an OS: Start with a fresh installation of Raspberry Pi OS (formerly Raspbian).
- Enable SSH: SSH is disabled by default on newer Raspberry Pi OS versions. You can enable it via `raspi-config` or by creating an empty file named `ssh` in the boot partition of the SD card.
- Update and Upgrade: Run `sudo apt update && sudo apt upgrade` to ensure all software is up-to-date.
- Configure Network: Ensure your Raspberry Pi has a stable internet connection.
- Set Up Your Virtual Private Cloud (VPC):
- Choose a Cloud Provider: Select a cloud service (e.g., AWS VPC, Azure Virtual Network, Google Cloud VPC).
- Create a VPC: Define your VPC with a suitable CIDR block (e.g., 10.0.0.0/16).
- Create Subnets: Within your VPC, create one or more subnets. For your Raspberry Pi, you'll likely need a public subnet if it directly connects to the internet, or a private subnet with a NAT Gateway if you want to restrict its outbound internet access while allowing inbound SSH.
- Configure Internet Gateway (IGW) & Route Tables: For public subnets, attach an Internet Gateway to your VPC and configure route tables to direct internet-bound traffic through the IGW.
- Set Up Security Groups/Network ACLs: This is crucial. Create a security group that allows inbound SSH traffic (port 22) only from your trusted IP addresses or specific ranges. This ensures that only authorized connections can reach your Pi.
- Establish SSH Connectivity:
- Generate SSH Key Pair: On your local machine, generate an SSH key pair (private and public key). Use `ssh-keygen`.
- Copy Public Key to Raspberry Pi: Use `ssh-copy-id` or manually copy your public key (`id_rsa.pub`) to the Raspberry Pi's `~/.ssh/authorized_keys` file. This allows you to log in without a password.
- Configure SSH Client: On your local machine, you might want to configure your SSH client (`~/.ssh/config`) for easier access.
- Assign Public IP (if applicable): If your Pi is in a public subnet, assign it a public IP address or use a dynamic DNS service if its IP changes. For private subnets, you'll need to set up a bastion host or VPN to access it.
- Test Your Connection:
- From your local machine, try to SSH into your Raspberry Pi using its public IP address (or through your bastion host/VPN).
- `ssh pi@your_pi_ip_address`
This process, while involving several steps, lays the foundation for a highly secure and manageable remote IoT environment. The initial investment in understanding and setting up this architecture pays dividends in terms of operational efficiency and robust security.
Unpacking the Benefits: A Comprehensive RemoteIoT VPC Review
A comprehensive `remoteiot vpc review focused on raspberry pi` wouldn't be complete without a deep dive into the tangible benefits this powerful combination offers. Beyond mere convenience, this setup delivers significant advantages in terms of security, flexibility, and scalability, addressing critical concerns for any serious IoT deployment.
Enhanced Security and Data Integrity
In the realm of IoT, where devices often handle sensitive data or control physical systems, security is paramount. The `remoteiot vpc ssh raspberry pi` configuration significantly elevates your security posture:
- Network Isolation: By operating within a VPC, your Raspberry Pi devices are isolated from the public internet by default. This dramatically reduces the attack surface, as your devices are not directly exposed to general internet traffic.
- Granular Access Control: VPC security groups and Network ACLs allow you to define precise rules for inbound and outbound traffic. You can restrict SSH access to only specific IP addresses (e.g., your office network or home IP), preventing unauthorized access attempts from elsewhere. This ensures that your data remains protected.
- Encrypted Communication (SSH): All data exchanged between your client and the Raspberry Pi via SSH is encrypted. This prevents eavesdropping and tampering, safeguarding sensitive commands, configuration files, and collected data from malicious actors.
- Reduced Risk of DDoS Attacks: While not entirely immune, devices within a well-configured VPC are less susceptible to direct Distributed Denial of Service (DDoS) attacks compared to devices directly exposed on the public internet.
- Centralized Security Management: Cloud providers offer centralized tools for managing security policies across your VPC, making it easier to maintain a consistent security posture across all your Raspberry Pi deployments. This is especially important for YMYL (Your Money or Your Life) applications where data integrity and system reliability are non-negotiable.
Flexibility and Scalability for Growing IoT Deployments
The dynamic nature of IoT projects demands a solution that can grow and adapt. The VPC model, when paired with Raspberry Pi, offers unparalleled flexibility and scalability:
- Effortless Scaling: As your project expands, adding more Raspberry Pis to your VPC is straightforward. You can provision new instances, integrate them into your existing network, and apply consistent security policies with minimal effort. This is a massive advantage over managing individual devices on disparate networks.
- Global Reach: Cloud providers have data centers worldwide. By leveraging VPCs, you can deploy Raspberry Pis in various geographical locations, all managed centrally within your cloud environment, extending the reach of your IoT solution.
- Resource Optimization: VPCs allow you to logically group and manage your resources. You can allocate specific subnets for different types of Raspberry Pi deployments (e.g., development, testing, production) or for different IoT functions (e.g., data collection, processing, actuation).
- Hybrid Cloud Capabilities: VPCs can be seamlessly integrated with your on-premises infrastructure using VPNs or dedicated connections. This enables hybrid cloud architectures where some IoT components run locally on Raspberry Pis while others leverage cloud services within the VPC.
- Remote Updates and Maintenance: The ability to securely access your Raspberry Pis remotely means you can push software updates, apply patches, and perform maintenance tasks without physical intervention, significantly reducing operational costs and downtime. This flexibility ensures your IoT ecosystem remains current and robust.
This comprehensive `remoteiot vpc review raspberry pi` clearly demonstrates that this architecture isn't just about connecting devices; it's about building a resilient, secure, and future-proof foundation for your IoT ambitions.
Performance and Reliability in RemoteIoT VPC Environments
When discussing a `remoteiot vpc review raspberry pi`, it's vital to consider not just security and flexibility, but also the practical aspects of performance and reliability. How well does this setup actually perform, and can you count on it when it matters most?
The performance of your `remoteiot vpc ssh raspberry pi` setup largely depends on several factors:
- Internet Connection Speed: Both at the Raspberry Pi's location and your client's location. A stable and fast connection is fundamental for responsive remote access.
- Cloud Provider's Network Latency: The geographical distance between your client, the cloud region where your VPC is hosted, and the physical location of your Raspberry Pi can introduce latency. Choosing a cloud region closer to your Pi's deployment can minimize this.
- Raspberry Pi's Resources: The Pi's CPU, RAM, and storage speed can affect how quickly it processes commands and responds to SSH requests, especially if it's running resource-intensive applications.
- VPC Configuration: An optimized VPC setup, with efficient routing and minimal network hops, contributes to better performance. Overly complex security group rules or unnecessary network appliances can sometimes introduce minor delays.
In terms of reliability, the VPC model offers significant advantages. Cloud providers are designed for high availability and redundancy. While your individual Raspberry Pi might experience hardware failure or power outages, the network infrastructure (the VPC itself) is inherently more reliable than a typical home or small office network. This means your secure tunnel to the Pi is less likely to be interrupted by external network issues. Furthermore, the ability to remotely diagnose and troubleshoot issues via SSH significantly enhances the overall reliability of your IoT deployment by allowing quick intervention. Monitoring tools provided by cloud platforms can also give insights into network performance and connectivity, helping you proactively address potential issues.
Real-World Use Cases for RemoteIoT VPC with Raspberry Pi
The versatility of a `remoteiot vpc review raspberry pi` setup truly shines when we look at its practical applications. This powerful combination unlocks a myriad of possibilities for various industries and personal projects:
- Smart Home Automation: Control lights, thermostats, security cameras, and other smart devices connected to a Raspberry Pi hub from anywhere in the world. Imagine adjusting your home's climate or checking your security feed while on vacation, all securely routed through your VPC.
- Environmental Monitoring: Deploy Raspberry Pis with sensors in remote locations (e.g., agricultural fields, forests, industrial sites) to monitor temperature, humidity, air quality, or soil conditions. Data can be securely transmitted back to a central cloud platform within the VPC for analysis, and the Pis can be maintained remotely.
- Remote Robotics and Drones: For hobbyists and researchers, controlling a robot or drone powered by a Raspberry Pi over long distances for surveillance, exploration, or data collection becomes feasible and secure.
- Edge Computing for Industrial IoT (IIoT): In factories or large facilities, Raspberry Pis can act as edge devices, collecting data from machinery, performing local processing, and then securely sending aggregated data to the cloud via the VPC. This reduces bandwidth needs and enhances real-time decision-making.
- Educational and Research Projects: Students and researchers can collaborate on projects involving remote hardware, allowing multiple users to access and control a shared Raspberry Pi setup from different locations without compromising security.
- Remote Server Hosting/Web Servers: While a Raspberry Pi isn't a high-performance server, it can host small websites or personal applications. Using a VPC ensures this server is isolated and protected, allowing secure remote management and updates.
These examples illustrate how `remoteiot vpc ssh raspberry pi` transforms the tiny computer into a robust, globally accessible, and secure component of complex distributed systems.
Overcoming Challenges and Best Practices
While the `remoteiot vpc review raspberry pi` highlights numerous benefits, it's also important to acknowledge potential challenges and adopt best practices to ensure a smooth and secure experience.
Common Challenges:
- Initial Setup Complexity: For newcomers to cloud networking, configuring VPCs, subnets, routing, and security groups can have a learning curve.
- Network Connectivity Issues: The Raspberry Pi's physical location might have unreliable internet, leading to intermittent disconnections.
- Resource Management: Raspberry Pi's limited resources (CPU, RAM) can be strained by demanding applications or too many concurrent SSH sessions.
- Security Misconfigurations: Incorrectly configured security groups or weak SSH practices can undermine the entire secure setup.
Best Practices:
- Automate Setup: Use infrastructure-as-code tools (e.g., Terraform, CloudFormation) to define and deploy your VPC and associated resources. This ensures consistency and reduces manual errors.
- Strong SSH Security: Always use public-key authentication instead of passwords. Disable password authentication for SSH on your Raspberry Pi. Regularly rotate SSH keys.
- Least Privilege Principle: Configure security groups and Network ACLs to allow only the absolute minimum necessary inbound and outbound traffic. For SSH, restrict access to only known, trusted IP addresses.
- Monitor Connectivity: Implement monitoring solutions (e.g., cloud monitoring services, simple ping checks) to track your Raspberry Pi's online status and network performance.
- Resource Optimization: Keep your Raspberry Pi OS lean. Only install necessary services. Monitor CPU and memory usage to prevent overloads.
- Regular Updates: Keep your Raspberry Pi OS and all installed software updated to patch security vulnerabilities.
- Use a VPN or Bastion Host for Private Subnets: If your Raspberry Pi is in a private subnet for maximum security, access it via a VPN connection to your VPC or through a hardened bastion host (a jump server) in a public subnet.
- Implement Logging: Configure logging on your Raspberry Pi and potentially send logs to a centralized log management service within your VPC for easier troubleshooting and security auditing.
By adhering to these best practices, you can mitigate common challenges and maximize the security, reliability, and efficiency of your `remoteiot vpc review raspberry pi` deployment.
Conclusion
In the dynamic world of IoT, the ability to securely, flexibly, and scalably manage your devices from anywhere is paramount. As this comprehensive `remoteiot vpc review focused on raspberry pi` has shown, the combination of a Raspberry Pi, a Virtual Private Cloud (VPC), and Secure Shell (SSH) provides an incredibly robust and powerful solution. It transforms the humble Raspberry Pi from a local hobbyist device into a globally accessible, enterprise-grade component of your connected ecosystem.
We've explored how `remoteiot vpc ssh raspberry pi` creates a secure tunnel, protecting your data and operations with network isolation and strong encryption. We've delved into the unparalleled flexibility and scalability offered by VPCs, allowing your IoT projects to grow and adapt with ease. From smart home automation to industrial edge computing, the real-world applications are vast and impactful. While challenges exist, adopting best practices ensures a resilient and efficient deployment.
This setup embodies the principles of secure, flexible, and scalable remote access that will remain critical as IoT continues to expand its reach and complexity. If you're looking to elevate your Raspberry Pi projects, enhance security, and gain unparalleled remote control, diving into RemoteIoT VPC management is your next logical step. We encourage you to start experimenting, share your experiences in the comments below, or explore other articles on our site for more insights into securing and optimizing your IoT deployments. The future of connected devices is remote, secure, and ready for your innovation.
Related Resources:


Detail Author:
- Name : Prof. Gilberto Funk PhD
- Username : emmerich.foster
- Email : korbin58@olson.com
- Birthdate : 1985-06-03
- Address : 196 Greyson Spur Apt. 637 Sydneyborough, KS 19973
- Phone : (283) 838-4776
- Company : Goodwin Ltd
- Job : Grinding Machine Operator
- Bio : Occaecati omnis quia perspiciatis placeat occaecati quo. Animi sunt ipsam natus molestias ipsam molestiae illo iste. Vel et unde saepe impedit voluptas occaecati. Iure provident rerum ullam incidunt.
Socials
twitter:
- url : https://twitter.com/cbergstrom
- username : cbergstrom
- bio : Quibusdam nobis in exercitationem possimus enim quisquam. Voluptatem laudantium pariatur qui pariatur unde.
- followers : 889
- following : 2755
linkedin:
- url : https://linkedin.com/in/bergstrom1987
- username : bergstrom1987
- bio : Enim tenetur quo non minima qui.
- followers : 937
- following : 1222
tiktok:
- url : https://tiktok.com/@claudie_bergstrom
- username : claudie_bergstrom
- bio : Qui natus dolores voluptatem maxime. Omnis dolores earum non officia.
- followers : 3782
- following : 906
facebook:
- url : https://facebook.com/claudie_bergstrom
- username : claudie_bergstrom
- bio : Necessitatibus voluptatem quia totam vel quaerat.
- followers : 2469
- following : 2930