In an increasingly connected world, the ability to manage and secure Internet of Things (IoT) devices remotely has become not just a convenience, but a critical necessity. For hobbyists, innovators, and businesses alike, the challenge of deploying and maintaining Raspberry Pi devices in diverse, often distant, locations demands a robust and secure strategy. This is where the powerful combination of a Virtual Private Cloud (VPC), Secure Shell (SSH), and the versatile Raspberry Pi comes into its own, forming the backbone of a truly resilient remoteiot vpc ssh raspberry pi infrastructure.
Navigating the complexities of remote IoT deployments can be daunting. From ensuring data integrity to preventing unauthorized access, every aspect of your connected devices requires meticulous planning and execution. This comprehensive guide delves deep into how you can leverage these technologies to build a secure, scalable, and highly manageable remote IoT ecosystem, ensuring your Raspberry Pis operate flawlessly, no matter where they are located.
Before we dive into the core content, it's important to address the "Data Kalimat" provided. The information primarily discusses the concept of "refresh" (in the context of web pages and browsers) and instructions for downloading Google Chrome. While these are common digital concepts, they are not directly relevant to the technical implementation of "remoteiot vpc ssh raspberry pi" for secure device management. Therefore, this article will focus exclusively on the requested keywords and their practical application in building robust IoT solutions.
- Vanripper Twitter
- Aj Delgado Twitter
- Lady Anaconda Bbc
- Gay Farmer Twitter
- No Lady On Twitter Can Recreate This
Table of Contents
- The Evolving Landscape of Remote IoT Management
- Understanding the Core Components: Raspberry Pi, VPC, and SSH
- Why Combine Remote IoT, VPC, and SSH? The Synergy of Security and Control
- Designing Your Secure Remote IoT Architecture with VPC and SSH
- Implementing SSH Best Practices for Raspberry Pi in a VPC
- Advanced Considerations for Robust Remote IoT Deployments
- Real-World Applications and Use Cases
- Overcoming Common Challenges and Pitfalls
The Evolving Landscape of Remote IoT Management
The proliferation of Internet of Things devices has transformed industries and daily life. From smart homes and connected vehicles to industrial sensors and environmental monitoring stations, IoT devices are generating unprecedented amounts of data and enabling new levels of automation. However, managing these devices, especially when they are geographically dispersed, presents significant challenges. Traditional network management tools often fall short when dealing with the unique constraints of IoT, such as limited power, intermittent connectivity, and the sheer scale of deployments. One of the primary concerns for any remote IoT deployment is security. Devices connected to the internet are potential entry points for malicious actors. Without proper safeguards, a single compromised Raspberry Pi could become a gateway to an entire network, leading to data breaches, service disruptions, or even physical damage. Scalability is another hurdle; manually configuring and updating hundreds or thousands of devices is simply not feasible. This necessitates a strategic approach that integrates robust networking, secure access, and efficient device management, making the remoteiot vpc ssh raspberry pi paradigm increasingly relevant.Understanding the Core Components: Raspberry Pi, VPC, and SSH
To fully appreciate the power of combining these technologies, it's essential to understand each component individually and its role in a secure remote IoT ecosystem.The Versatile Raspberry Pi in IoT
The Raspberry Pi is a series of small, single-board computers developed by the Raspberry Pi Foundation. Its low cost, compact size, versatility, and extensive community support have made it an incredibly popular choice for a wide range of IoT projects. From simple home automation tasks to complex industrial monitoring systems, Raspberry Pis can act as sensors, data aggregators, edge computing devices, or even small servers. They run various Linux distributions, most commonly Raspberry Pi OS (formerly Raspbian), which provides a familiar environment for developers. However, the very accessibility and openness that make the Raspberry Pi so appealing also present security challenges. Out-of-the-box configurations often have default credentials or open ports that, if not secured, can be easily exploited. When these devices are deployed remotely, they become even more vulnerable without a strong security perimeter.Virtual Private Clouds (VPC): Your Private Corner in the Cloud
A Virtual Private Cloud (VPC) is a virtual network dedicated to your cloud account. It is logically isolated from other virtual networks in the cloud, providing you with a private, secure, and customizable environment to launch your cloud resources, including virtual machines, databases, and, crucially, your IoT infrastructure. Think of a VPC as your own private data center within a public cloud provider like AWS, Google Cloud, or Azure. Within a VPC, you have complete control over your network environment, including IP address ranges, subnets, route tables, and network gateways. This level of control allows you to define strict security boundaries using security groups (stateful firewalls at the instance level) and Network Access Control Lists (NACLs - stateless firewalls at the subnet level). For remote IoT deployments, a VPC offers unparalleled benefits:- Isolation: Your IoT devices and their traffic are isolated from the public internet and other cloud users.
- Security: Granular control over inbound and outbound traffic, allowing only necessary communication.
- Scalability: Easily expand your network as your IoT fleet grows without reconfiguring physical infrastructure.
- Compliance: Helps meet regulatory compliance requirements by providing a controlled network environment.
Secure Shell (SSH): The Backbone of Remote Access
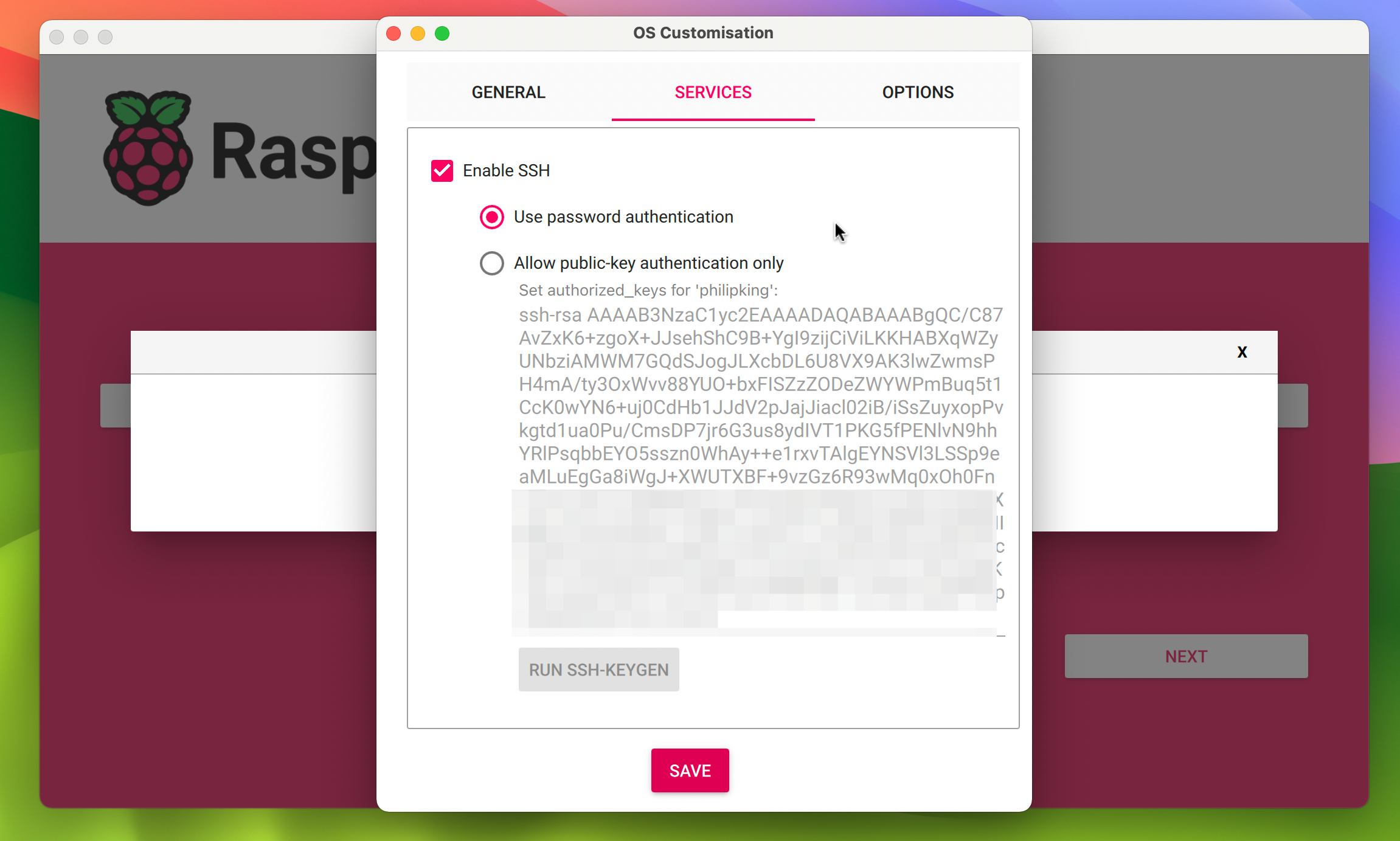
Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most common application is remote command-line login, but it also supports secure tunneling, TCP port forwarding, and file transfers. SSH provides strong authentication and encrypted communication between two network devices, making it the industry standard for secure remote access to Linux-based systems, including the Raspberry Pi. Unlike insecure protocols like Telnet, SSH encrypts all data exchanged between the client and the server, preventing eavesdropping, connection hijacking, and other network attacks. Key-based authentication, using public/private key pairs, offers a much more secure alternative to password-based authentication, which is vulnerable to brute-force attacks. For managing remote IoT devices, SSH is indispensable for:- Executing commands and scripts.
- Transferring configuration files and software updates.
- Troubleshooting and diagnostics.
- Monitoring device health and performance.
Why Combine Remote IoT, VPC, and SSH? The Synergy of Security and Control
The true power emerges when these three components are integrated into a cohesive architecture. By placing your Raspberry Pi IoT devices within a VPC and securing remote access via SSH, you create a robust, resilient, and highly secure system. Imagine your Raspberry Pis are deployed in various remote locations – perhaps monitoring environmental conditions in a forest, managing smart agricultural systems, or collecting data from industrial machinery. Without a VPC, each device would need to be directly exposed to the public internet to allow remote access, significantly increasing its attack surface. This exposure makes them prime targets for cyberattacks. By leveraging a VPC, your Raspberry Pis reside in a private network, inaccessible from the public internet by default. SSH then becomes the secure tunnel through which you can reach these devices. Here’s how the synergy works:- Enhanced Security: The VPC acts as a strong perimeter defense, preventing unauthorized access to your IoT devices. Only specific, controlled entry points (e.g., a bastion host within the VPC) are exposed to the internet, and even those are protected by strict security group rules. SSH provides encrypted, authenticated communication for legitimate users.
- Controlled Access: You dictate exactly who can access your devices and from where. Security groups can restrict SSH access to only specific IP addresses or subnets.
- Scalability: As your IoT fleet grows, adding new Raspberry Pis to your VPC is straightforward. Network configurations can be standardized and automated, simplifying deployment at scale.
- Simplified Management: A centralized VPC allows for easier network monitoring, logging, and management of all your connected devices.
- Reduced Attack Surface: By keeping your Raspberry Pis off the public internet, you drastically reduce the number of potential attack vectors.
Designing Your Secure Remote IoT Architecture with VPC and SSH
Building a secure remote IoT infrastructure with VPC and SSH requires careful planning. Here’s a conceptual framework for designing such an architecture: 1. **VPC Creation:** Start by creating a new VPC in your chosen cloud provider (AWS, GCP, Azure). Define a suitable IP address range (e.g., 10.0.0.0/16) that won't conflict with your on-premises networks. 2. **Subnetting:** Divide your VPC into multiple subnets. A common practice is to have: * **Public Subnet:** For resources that need direct internet access (e.g., a NAT Gateway for outbound traffic from private subnets, or a bastion host for SSH access). * **Private Subnets:** Where your Raspberry Pi IoT devices will reside. These subnets have no direct internet access. 3. **Internet Gateway (IGW) & NAT Gateway (NAT GW):** * An IGW allows resources in public subnets to communicate with the internet. * A NAT GW in a public subnet allows resources in private subnets to initiate outbound connections to the internet (e.g., for software updates, sending data to cloud services) without being directly accessible from the internet. 4. **Route Tables:** Configure route tables to direct traffic appropriately between subnets and to the IGW/NAT GW. 5. **Security Groups & Network ACLs:** These are your primary firewall mechanisms. * **Security Groups:** Attach to individual Raspberry Pi instances. Allow only necessary inbound traffic (e.g., SSH from your bastion host) and outbound traffic (e.g., to IoT platforms, update servers). * **Network ACLs:** Act as a stateless firewall at the subnet level, providing an additional layer of defense. 6. **Bastion Host (Jump Box):** This is a critical component for secure SSH access. * A small virtual machine placed in a public subnet within your VPC. * It's the *only* entry point from the internet for SSH access to your private IoT devices. * Its security group should be highly restrictive, allowing SSH only from known, trusted IP addresses (e.g., your office IP). 7. **Connecting Raspberry Pis to the VPC:** * **VPN (Site-to-Site or Client VPN):** For a more robust and secure connection, you can establish a VPN tunnel from each remote Raspberry Pi location back to your VPC. This creates a secure, encrypted tunnel over the public internet, making the Raspberry Pi effectively part of your VPC. This is often the preferred method for production deployments. * **Direct Connect/Interconnect (for large enterprises):** For very large-scale or high-bandwidth needs, dedicated private connections can be established between your on-premises network and the cloud provider. * **IoT Core/Device Gateway:** Cloud providers offer IoT services (like AWS IoT Core, Azure IoT Hub) that can act as secure gateways for devices to connect and send data. While not directly part of the VPC/SSH access *to* the device, they are crucial for device-to-cloud communication. You would still use VPC and SSH for management *of* the device. 8. **SSH Key Management:** Generate and securely store SSH key pairs. The public key is placed on the Raspberry Pis, and the private key is used by your bastion host or local machine to initiate connections. This architecture ensures that your Raspberry Pis are not directly exposed to the internet, and all management traffic flows through a secure, controlled channel, solidifying your remoteiot vpc ssh raspberry pi setup.Implementing SSH Best Practices for Raspberry Pi in a VPC
Even with a secure VPC, the SSH connection itself needs to be hardened. Neglecting SSH security can undermine your entire remoteiot vpc ssh raspberry pi strategy. 1. **Disable Password Authentication:** This is perhaps the most critical step. Passwords are vulnerable to brute-force attacks. Always use SSH key-based authentication. * `sudo nano /etc/ssh/sshd_config` * Find `PasswordAuthentication yes` and change it to `PasswordAuthentication no`. * Restart SSH service: `sudo systemctl restart ssh` 2. **Use Strong SSH Keys:** Generate RSA keys with at least 2048-bit encryption (preferably 4096-bit) or use ED25519 keys for even stronger security. Protect your private key with a strong passphrase. 3. **Change Default SSH Port (Optional but Recommended):** While not a security measure in itself (it's "security by obscurity"), changing the default SSH port (22) can reduce the volume of automated scanning attempts against your bastion host. Remember to update your security group rules accordingly. * `sudo nano /etc/ssh/sshd_config` * Find `Port 22` and change it to a non-standard port (e.g., 2222). * Restart SSH service. 4. **Implement Fail2Ban:** This intrusion prevention framework scans log files (e.g., SSH access logs) for malicious activity (like repeated failed login attempts) and automatically bans the offending IP addresses using firewall rules. * `sudo apt update && sudo apt install fail2ban` * Configure it to monitor SSH logs and ban IPs after a few failed attempts. 5. **Regularly Update OS and Software:** Keep your Raspberry Pi's operating system (Raspberry Pi OS) and all installed software up to date. Security patches frequently address vulnerabilities that attackers could exploit. * `sudo apt update && sudo apt full-upgrade` 6. **Principle of Least Privilege:** Create separate user accounts for different administrative tasks on your Raspberry Pis. Grant only the necessary permissions to each user. Avoid using the default 'pi' user for all operations, and certainly don't use 'root' directly. 7. **SSH Agent Forwarding:** For convenience and security when connecting from your local machine through a bastion host to your Raspberry Pi, use SSH agent forwarding. This allows you to use your local SSH private key without storing it on the bastion host. Adhering to these best practices significantly hardens your remote access, making your remoteiot vpc ssh raspberry pi deployment far more resilient against cyber threats.Advanced Considerations for Robust Remote IoT Deployments
Beyond the foundational remoteiot vpc ssh raspberry pi setup, several advanced considerations can further enhance the robustness and manageability of your IoT fleet. 1. **Monitoring and Logging:** Implement comprehensive monitoring and logging solutions. Cloud providers offer services like AWS CloudWatch, Google Cloud Logging, or Azure Monitor to collect logs from your VPC, bastion host, and even your Raspberry Pis. Centralized logging helps detect anomalies, troubleshoot issues, and provides an audit trail for security incidents. 2. **Automated Provisioning and Configuration Management:** Manually configuring each Raspberry Pi is not scalable. Utilize tools like Ansible, Puppet, or cloud-specific services (e.g., AWS IoT Greengrass, Azure IoT Edge) for automated provisioning, configuration management, and software deployment. This ensures consistency across your fleet and reduces human error. 3. **Device Identity and Certificate Management:** For true end-to-end security, each Raspberry Pi should have a unique identity, often managed through X.509 certificates. These certificates can be used for mutual authentication when connecting to cloud services or other devices, ensuring that only trusted devices can communicate. 4. **Over-the-Air (OTA) Updates:** Securely delivering software and firmware updates to remote devices is critical. Design an OTA update mechanism that verifies the integrity and authenticity of updates before applying them, preventing malicious code injection. 5. **Disaster Recovery and Redundancy:** Plan for scenarios where devices might fail or become unreachable. Implement strategies for device replacement, automated re-provisioning, and data redundancy to minimize downtime and data loss. 6. **Network Performance Optimization:** For bandwidth-constrained or latency-sensitive applications, consider optimizing your network configuration within the VPC. This might involve choosing specific instance types for your bastion host or optimizing routing. By incorporating these advanced considerations, you move beyond basic remote access to a truly enterprise-grade remoteiot vpc ssh raspberry pi solution.Real-World Applications and Use Cases
The secure remoteiot vpc ssh raspberry pi architecture finds applications across a myriad of industries, solving real-world challenges where remote management and security are paramount. * **Smart Agriculture:** Raspberry Pis deployed in fields can monitor soil moisture, temperature, and nutrient levels. Farmers can securely access these devices via SSH in a VPC to adjust irrigation systems, deploy new sensor algorithms, or troubleshoot connectivity issues without physically visiting each sensor node. * **Industrial Automation:** In factories or remote industrial sites, Raspberry Pis can act as edge gateways, collecting data from PLCs and machinery. Secure SSH access allows engineers to remotely diagnose equipment, update control logic, or retrieve performance data, minimizing downtime and travel costs. * **Environmental Monitoring:** Weather stations, air quality sensors, or water level monitors powered by Raspberry Pis can be deployed in harsh, remote environments. The VPC and SSH setup ensures reliable data transmission and enables researchers to maintain and calibrate these devices from a central lab. * **Smart City Infrastructure:** Traffic light management, public safety cameras, or smart street lighting systems can utilize Raspberry Pis. Secure remote access is vital for maintaining these critical urban services, allowing for rapid response to issues and efficient infrastructure upgrades. * **Remote Surveillance and Security:** For temporary or permanent surveillance setups in isolated areas, a Raspberry Pi with a camera can stream data to a secure VPC. SSH provides a secure channel to configure camera settings, retrieve footage, or update the surveillance software. In each of these scenarios, the ability to securely and reliably interact with remote Raspberry Pi devices through a private cloud network is not just an advantage, but a fundamental requirement for operational success and data integrity.Overcoming Common Challenges and Pitfalls
While the remoteiot vpc ssh raspberry pi approach offers significant benefits, it's important to be aware of potential challenges and how to mitigate them. 1. **Network Latency and Bandwidth:** Remote IoT devices, especially those using cellular or satellite connections, might experience high latency or limited bandwidth. Design your applications to be resilient to these conditions, minimizing data transfer where possible and using efficient protocols. 2. **Power Management:** Raspberry Pis require a stable power source. For truly remote deployments, consider solar power, battery backups, or low-power modes to ensure continuous operation. SSH access is useless if the device is offline due to power issues. 3. **Initial Provisioning:** Getting the Raspberry Pi connected to the internet and then securely into your VPC can be a "chicken-and-egg" problem. Solutions include pre-configuring devices before deployment, using a temporary Wi-Fi hotspot for initial setup, or leveraging cloud-provider specific device provisioning services that can bootstrap devices into your VPC. 4. **Scalability Issues from Poor Planning:** Without proper subnetting, IP address management, and automation, a rapidly growing IoT fleet can quickly become unmanageable. Plan for scale from day one, using infrastructure as code (IaC) tools like Terraform or CloudFormation to define your VPC and device configurations. 5. **Security Vulnerabilities from Misconfigurations:** The most common cause of security breaches is human error. Double-check your security group rules, NACLs, SSH key permissions, and user accounts. Regularly audit your configurations to ensure they adhere to the principle of least privilege. 6. **Physical Security of the Device:** While VPC and SSH secure the network access, the physical security of the Raspberry Pi itself is also crucial. If an attacker gains physical access, they could potentially bypass network security. Consider tamper-proof enclosures and secure mounting for devices in vulnerable locations. Addressing these challenges proactively ensures a more robust and reliable remoteiot vpc ssh raspberry pi deployment.Conclusion
The journey to effectively manage and secure remote IoT devices, particularly those powered by the versatile Raspberry Pi, is a complex yet rewarding one. By strategically integrating a Virtual Private Cloud (VPC) for network isolation, and Secure Shell (SSH) for encrypted remote access, you build a foundation that is not only robust and scalable but, most importantly, secure. The remoteiot vpc ssh raspberry pi paradigm is more than just a technical setup; it's a commitment to best practices in network security and device management that safeguards your data, ensures operational continuity, and unlocks the full potential of your connected world. Embracing this architecture allows you to deploy and maintain your Raspberry Pi devices with confidence, knowing that they are protected from the myriad of threats lurking on the public internet. It empowers you to innovate, expand, and troubleshoot your IoT solutions from anywhere, transforming challenges into opportunities. We encourage you to explore these concepts further, experiment with your own setups, and share your experiences in the comments below. What unique challenges have you faced in your remote IoT deployments, and how have you overcome them? Your insights can help others on their journey to building a more secure and efficient connected future.Related Resources:


Detail Author:
- Name : Jaylen Connelly
- Username : santos.schuppe
- Email : vivian.eichmann@turcotte.com
- Birthdate : 2006-06-27
- Address : 15641 Greenfelder Alley Apt. 389 North Winnifred, AZ 50358
- Phone : +1 (215) 579-4104
- Company : Gulgowski-Gorczany
- Job : Electronics Engineer
- Bio : Provident quis velit cumque et. Nemo molestiae voluptate autem aut repudiandae est voluptas eos.
Socials
twitter:
- url : https://twitter.com/isaac_schulist
- username : isaac_schulist
- bio : Odit dolorum eum maxime vitae. Corrupti nisi qui corporis dolores fugit consequatur. Voluptate occaecati aliquid dolorem voluptatem temporibus iure at earum.
- followers : 1694
- following : 953
instagram:
- url : https://instagram.com/isaac3196
- username : isaac3196
- bio : Quas cumque rerum est. Explicabo non eius quia accusamus non dolor.
- followers : 4674
- following : 1492
linkedin:
- url : https://linkedin.com/in/isaac_real
- username : isaac_real
- bio : Sed sint fuga iusto praesentium ullam.
- followers : 1166
- following : 679
facebook:
- url : https://facebook.com/ischulist
- username : ischulist
- bio : Doloribus delectus earum voluptatem et provident.
- followers : 6475
- following : 863
tiktok:
- url : https://tiktok.com/@isaac_real
- username : isaac_real
- bio : Blanditiis deserunt iure eos quae sunt dolorem non.
- followers : 4683
- following : 393