In an increasingly connected world, the ability to remotely manage and interact with Internet of Things (IoT) devices is not just a convenience, but a critical necessity. From smart factories to agricultural sensors spread across vast fields, devices often operate in environments where direct physical access is impractical, costly, or even dangerous. This is where the powerful combination of remote IoT management, SSH (Secure Shell), and Amazon Web Services (AWS) comes into play, forming the backbone of what we refer to as "remoteiot ssh aws". This robust framework empowers organizations to maintain control, troubleshoot issues, and deploy updates to their distributed fleet of devices with unparalleled efficiency and security.
The convergence of IoT, cloud computing, and secure remote access protocols like SSH represents a paradigm shift in how we interact with the physical world through digital means. AWS, as a leading cloud provider, offers a comprehensive suite of services that are perfectly tailored for building scalable, secure, and resilient IoT solutions. Understanding how to leverage these services, particularly for establishing secure SSH connections to remote IoT devices, is paramount for anyone looking to deploy or manage an effective IoT ecosystem. This article will delve deep into the intricacies of "remoteiot ssh aws", exploring its fundamental components, architectural considerations, security best practices, and the immense value it brings to modern enterprises.
Table of Contents
- The Dawn of Remote IoT Management
- Understanding "remoteiot ssh aws" Fundamentals
- Why Secure Remote Access is Non-Negotiable for IoT
- Architecting a Robust "remoteiot ssh aws" Solution
- Practical Applications and Use Cases
- Fortifying Your "remoteiot ssh aws" Security Posture
- Overcoming Common Challenges
- The Future Landscape of Remote IoT
The Dawn of Remote IoT Management
The proliferation of IoT devices has transformed industries, offering unprecedented insights and automation capabilities. However, with millions, and soon billions, of devices deployed globally, the sheer scale of management becomes a formidable challenge. Imagine a smart city with thousands of interconnected streetlights, environmental sensors, and traffic cameras. How do you update their firmware, diagnose a faulty sensor, or retrieve logs without dispatching a technician to each individual location? This is precisely the problem that robust remote IoT management solutions aim to solve. Traditionally, remote access to devices might involve complex VPN setups or proprietary protocols, often lacking the flexibility and scalability required for a true IoT deployment. The demand for a standardized, secure, and highly scalable method for interacting with these devices led to the adoption of cloud-based solutions. AWS, with its extensive global infrastructure and specialized IoT services, emerged as a natural fit. By integrating SSH, a time-tested protocol for secure remote access, with AWS's IoT ecosystem, organizations can achieve granular control over their device fleet, ensuring operational continuity and minimizing downtime. This synergy is what defines the power of "remoteiot ssh aws".Understanding "remoteiot ssh aws" Fundamentals
At its core, "remoteiot ssh aws" is about creating a secure, on-demand communication channel between an operator or an automated system and a remote IoT device, facilitated by AWS services. It leverages the strengths of each component to build a comprehensive solution.AWS IoT Core: The Central Nervous System
AWS IoT Core acts as the central hub for connecting and managing billions of IoT devices. It provides secure, bi-directional communication between devices and the AWS Cloud. Devices can publish data to IoT Core, and applications can subscribe to that data. Crucially for "remoteiot ssh aws", IoT Core also enables applications to send commands to devices. Key features include:- **Device Gateway:** Allows devices to connect to AWS IoT Core using MQTT, HTTP, or WebSockets.
- **Message Broker:** Facilitates secure communication between devices and applications.
- **Registry:** Manages device identities and metadata.
- **Device Shadow:** Maintains a virtual representation (shadow) of each device's state, allowing applications to interact with devices even when they are offline. This is vital for sending SSH connection requests or commands.
- **Rules Engine:** Processes incoming device data, routing it to other AWS services like Lambda, S3, or DynamoDB for storage, analysis, or further action.
SSH: Your Secure Gateway
SSH, or Secure Shell, is a cryptographic network protocol for operating network services securely over an unsecured network. Its primary use is for remote command-line login and remote command execution. For IoT devices, SSH provides a robust and widely understood method for:- **Remote access to the device's operating system:** Allowing technicians to run commands, inspect logs, and manage files.
- **Secure file transfer:** Copying configuration files or firmware updates to the device.
- **Port forwarding/tunneling:** Creating secure tunnels for other services.
Why Secure Remote Access is Non-Negotiable for IoT
The importance of secure remote access in IoT cannot be overstated. Without it, organizations face significant operational hurdles and security risks.- **Operational Efficiency:** Manual intervention for device maintenance is resource-intensive and time-consuming. Remote access allows for rapid diagnostics, configuration changes, and software updates, minimizing operational costs and maximizing uptime.
- **Scalability:** As IoT deployments grow from dozens to millions of devices, manual management becomes impossible. Automated, secure remote access through platforms like AWS enables organizations to scale their operations without proportional increases in human resources.
- **Reduced Downtime:** When a device malfunctions, quick remote diagnosis and resolution can prevent prolonged service interruptions, which can have significant financial implications, especially in industrial or critical infrastructure settings.
- **Enhanced Security Posture:** Directly exposing IoT devices to the public internet for remote access is a massive security risk. "remoteiot ssh aws" architectures mitigate this by using secure, authenticated, and often ephemeral connections initiated through a cloud broker, rather than persistent open ports. This significantly reduces the attack surface.
- **Compliance and Auditing:** Many industries have strict regulatory requirements for device access and data handling. Secure remote access mechanisms provide audit trails and control over who accesses devices and when, aiding in compliance efforts.
- **Firmware Over-The-Air (FOTA) Updates:** Secure remote access is fundamental for reliably pushing firmware updates to devices, patching vulnerabilities, adding new features, and improving performance across the fleet.
Architecting a Robust "remoteiot ssh aws" Solution
Building a secure and efficient "remoteiot ssh aws" solution involves careful consideration of both the device side and the AWS cloud integration.Device-Side Considerations
The IoT device itself needs to be capable of establishing and managing SSH connections, but not necessarily initiating them from the outside.- **SSH Server:** The device must run an SSH server (e.g., OpenSSH) configured to accept connections.
- **Connectivity:** Devices need reliable internet connectivity (Wi-Fi, cellular, Ethernet) to communicate with AWS IoT Core.
- **AWS IoT Device SDK:** Devices should integrate the AWS IoT Device SDK to securely connect to IoT Core, publish messages, and subscribe to topics. This is crucial for receiving commands to initiate SSH tunnels.
- **Resource Constraints:** For very constrained devices, a full SSH server might be too heavy. In such cases, alternative lightweight remote execution agents or custom protocols might be considered, though SSH offers the most robust and widely supported solution for general-purpose remote access.
- **Ephemeral SSH Tunnels:** A common and highly secure pattern is for the device to *initiate* an outbound connection (e.g., an SSH reverse tunnel) to a bastion host or a secure proxy within AWS, only when a remote access request is received via AWS IoT Core. This avoids opening inbound ports on the device.
AWS Cloud Integration
On the AWS side, several services work in concert to facilitate "remoteiot ssh aws":- **AWS IoT Core:** As discussed, it's the central message broker.
- **MQTT Topics:** Define specific MQTT topics for sending SSH connection requests to devices (e.g., `iot/device/<device-id>/ssh/connect`) and for devices to report their status (e.g., `iot/device/<device-id>/ssh/status`).
- **Device Shadow:** Update the device shadow to indicate a pending SSH connection request or to store temporary credentials.
- **AWS Lambda:** A serverless compute service used to process messages from IoT Core and orchestrate the SSH connection.
- When an operator requests an SSH session, a Lambda function can be triggered via an API Gateway endpoint or directly from a web application.
- This Lambda function can then publish an MQTT message to the target device via IoT Core, instructing it to initiate an SSH tunnel.
- Alternatively, Lambda can generate temporary SSH credentials or pre-signed URLs for a secure tunnel.
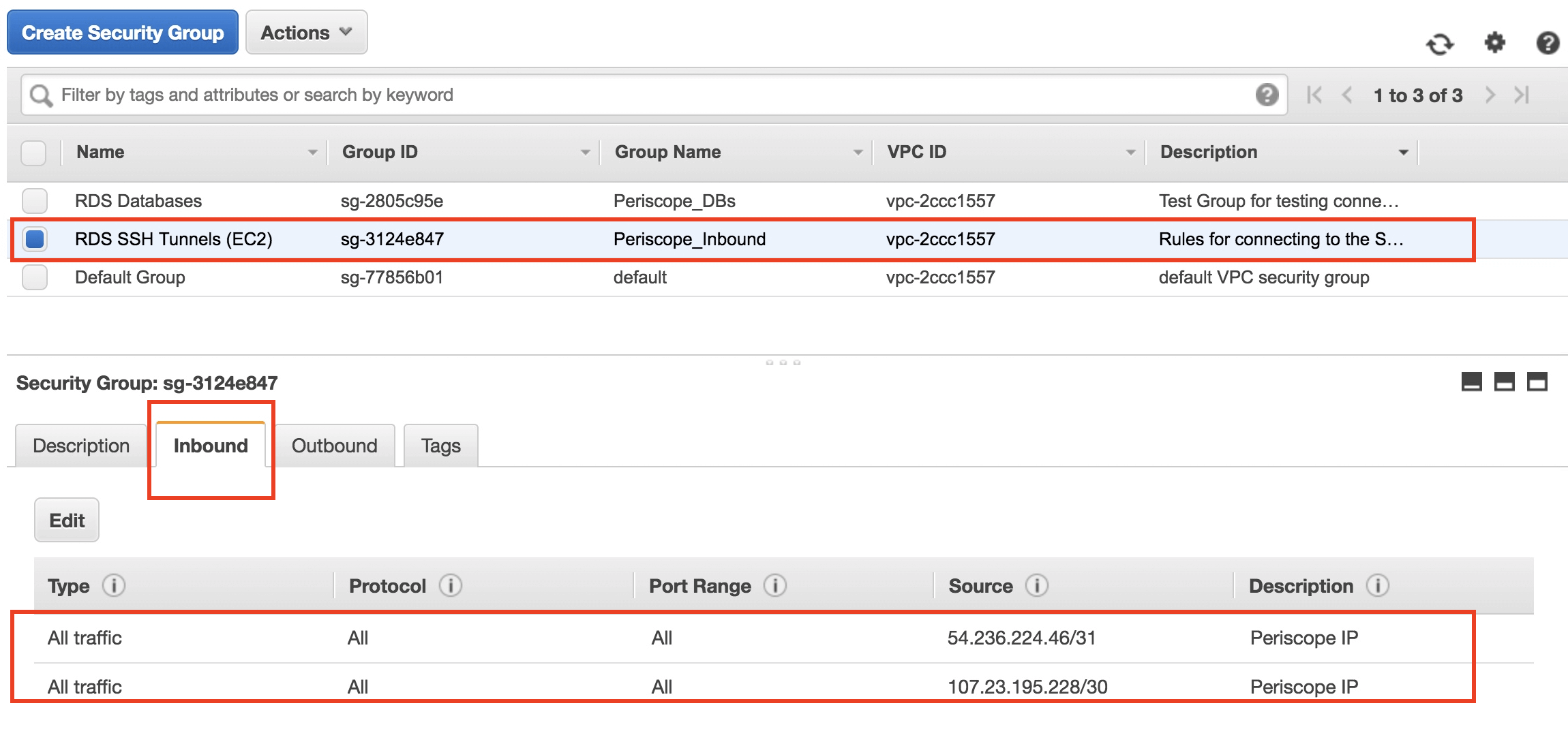
- **Amazon EC2 (Bastion Host):** A virtual server instance often used as a jump server or bastion host.
- For reverse SSH tunnels, devices can connect outbound to an EC2 instance, creating a secure channel. Operators then SSH into this EC2 instance, and from there, jump to the IoT device via the established tunnel.
- This EC2 instance should be hardened, placed in a private subnet, and only accessible via strict security group rules.
- **AWS Systems Manager (SSM) Session Manager:** While not strictly SSH, SSM Session Manager offers a highly secure and auditable alternative for remote shell access to EC2 instances, and increasingly, to edge devices. It eliminates the need to manage SSH keys or open inbound ports. For compatible devices, this can be a superior alternative to traditional SSH for "remoteiot ssh aws" scenarios.
- **AWS IAM (Identity and Access Management):** Crucial for defining who can access what.
- Grant least privilege access to Lambda functions, IoT policies, and EC2 instances.
- Define granular permissions for users or roles that are allowed to initiate remote SSH sessions.
- **AWS VPC (Virtual Private Cloud):** Network isolation is key.
- Place your EC2 bastion hosts in private subnets.
- Use Security Groups and Network ACLs to control inbound and outbound traffic rigorously.
Practical Applications and Use Cases
The capabilities offered by "remoteiot ssh aws" are transformative across various sectors:- **Industrial IoT (IIoT):** Remotely diagnose and troubleshoot PLCs, industrial robots, and sensors in factories or remote sites. Push firmware updates to machinery without interrupting production lines.
- **Smart Cities:** Manage traffic light controllers, environmental monitoring stations, and public safety cameras. Perform maintenance, update software, and collect diagnostic data from devices distributed across a city.
- **Agriculture:** Access and configure smart irrigation systems, crop monitoring sensors, and automated farming equipment located in remote fields.
- **Healthcare:** Securely access medical devices in clinics or patient homes for diagnostics, software updates, and compliance checks, ensuring patient safety and data privacy.
- **Retail:** Remotely manage point-of-sale systems, digital signage, and inventory sensors across numerous store locations.
- **Energy Management:** Monitor and control smart meters, grid sensors, and renewable energy infrastructure from a central location, enabling proactive maintenance and efficient resource allocation.
Fortifying Your "remoteiot ssh aws" Security Posture
Security is paramount in any IoT deployment, especially when remote access is involved. A breach can have severe consequences, from data theft to physical damage. Here are key best practices for "remoteiot ssh aws":- **Least Privilege Principle:** Grant only the minimum necessary permissions to users, roles, and devices. For instance, an IoT device should only have permissions to publish to its own topics and subscribe to command topics, not to other devices' topics or sensitive AWS services.
- **Strong Authentication:**
- For devices: Use X.509 certificates managed by AWS IoT Core for device authentication.
- For operators: Implement multi-factor authentication (MFA) for all AWS console and SSH access. Use IAM roles and temporary credentials instead of long-lived access keys.
- For SSH: Always use key-based authentication (SSH keys) instead of passwords. Rotate SSH keys regularly.
- **Network Segmentation:** Isolate your IoT devices and bastion hosts within private subnets in your VPC. Use strict Security Group and Network ACL rules to control traffic flow, allowing only necessary ports and protocols.
- **Ephemeral Connections:** Design your system so that SSH tunnels are established only when needed and are torn down immediately after the session ends. This minimizes the window of opportunity for attackers.
- **Auditing and Logging:** Enable AWS CloudTrail and CloudWatch Logs to capture all API calls, SSH connection attempts, and device activities. Regularly review these logs for suspicious patterns. Integrate with security information and event management (SIEM) systems.
- **Device Hardening:**
- Disable unnecessary services and ports on the IoT device.
- Keep the device's operating system and all software up to date with the latest security patches.
- Implement secure boot mechanisms if supported by the hardware.
- **Data Encryption:** Encrypt data in transit (TLS/SSL for MQTT, SSH for shell access) and at rest (e.g., if storing device logs in S3).
- **Vulnerability Management:** Regularly scan your device firmware and AWS infrastructure for vulnerabilities. Conduct penetration testing to identify weaknesses before attackers do.
Overcoming Common Challenges
While "remoteiot ssh aws" offers immense benefits, deployments can encounter challenges:- **Connectivity Issues:** IoT devices often operate in environments with intermittent or poor network connectivity. Solutions include designing devices to handle offline operations, leveraging AWS IoT Greengrass for edge processing, and implementing robust retry mechanisms for communication.
- **Device Resource Constraints:** Small, low-power devices may not have the computational resources for a full SSH server or complex encryption. This requires careful selection of hardware or opting for lighter remote management protocols where SSH is truly overkill.
- **Latency:** For real-time control, the round-trip latency through the cloud can be an issue. Edge computing (AWS IoT Greengrass) can process data and execute commands locally, reducing latency for critical operations while still leveraging the cloud for higher-level management.
- **Cost Management:** Running EC2 bastion hosts 24/7 can incur costs. Utilizing serverless functions (Lambda) for orchestration and designing ephemeral SSH tunnels can help optimize expenses. AWS Systems Manager Session Manager also offers a cost-effective alternative for remote access without dedicated EC2 instances.
- **Scalability of SSH Key Management:** Managing SSH keys for thousands or millions of devices can be cumbersome. Automating key rotation and distribution, potentially leveraging AWS Secrets Manager, becomes essential.
The Future Landscape of Remote IoT
The evolution of "remoteiot ssh aws" and remote IoT management is closely tied to advancements in edge computing, artificial intelligence, and new communication technologies. We can expect to see:- **Deeper Integration with Edge AI/ML:** Remote access will increasingly be used to deploy and manage AI/ML models directly on edge devices, enabling intelligent decision-making closer to the data source.
- **Enhanced Predictive Maintenance:** With more sophisticated remote diagnostics and data collection, predictive maintenance capabilities will improve, allowing for proactive intervention before failures occur.
- **5G and Beyond:** The rollout of 5G networks will provide lower latency and higher bandwidth, further enabling real-time remote control and massive IoT deployments.
- **Standardization and Interoperability:** Efforts to standardize IoT communication and management protocols will make it easier to integrate devices from various manufacturers into a unified "remoteiot ssh aws" framework.
- **Serverless Remote Access:** More services like AWS Systems Manager Session Manager will evolve to provide serverless, agent-based remote access solutions, reducing operational overhead and enhancing security by eliminating the need for traditional SSH bastion hosts.
The ability to securely and efficiently manage IoT devices remotely is no longer a luxury but a fundamental requirement for successful deployments. The "remoteiot ssh aws" paradigm, leveraging AWS IoT Core, SSH, and a suite of complementary AWS services, provides a robust, scalable, and secure framework for achieving this. By understanding the core components, adhering to stringent security best practices, and anticipating future trends, organizations can unlock the full potential of their IoT investments.
We hope this deep dive into "remoteiot ssh aws" has provided you with valuable insights. What are your biggest challenges in managing remote IoT devices? Share your thoughts and experiences in the comments below! If you found this article helpful, consider sharing it with your network or exploring our other guides on cloud computing and IoT security.
Related Resources:


Detail Author:
- Name : Jennie McGlynn
- Username : giovanny.lind
- Email : henriette77@gmail.com
- Birthdate : 1994-07-31
- Address : 968 Muller Viaduct New Julien, OR 87332
- Phone : 323.468.4492
- Company : Hessel Inc
- Job : Electrical and Electronic Inspector and Tester
- Bio : Corporis est facere rem qui qui nesciunt. Nostrum voluptate et explicabo similique reprehenderit necessitatibus ut. Quae ut eum error repellat optio labore. Tempora corrupti dicta fuga libero.
Socials
linkedin:
- url : https://linkedin.com/in/elisabeth_collins
- username : elisabeth_collins
- bio : Sint dolorem pariatur et nisi consequatur dolore.
- followers : 6369
- following : 2401
tiktok:
- url : https://tiktok.com/@elisabeth_official
- username : elisabeth_official
- bio : Numquam ullam saepe est.
- followers : 6802
- following : 1419
instagram:
- url : https://instagram.com/collins1999
- username : collins1999
- bio : Nesciunt nisi quis officia omnis. Qui quas ut natus enim nihil.
- followers : 6091
- following : 445