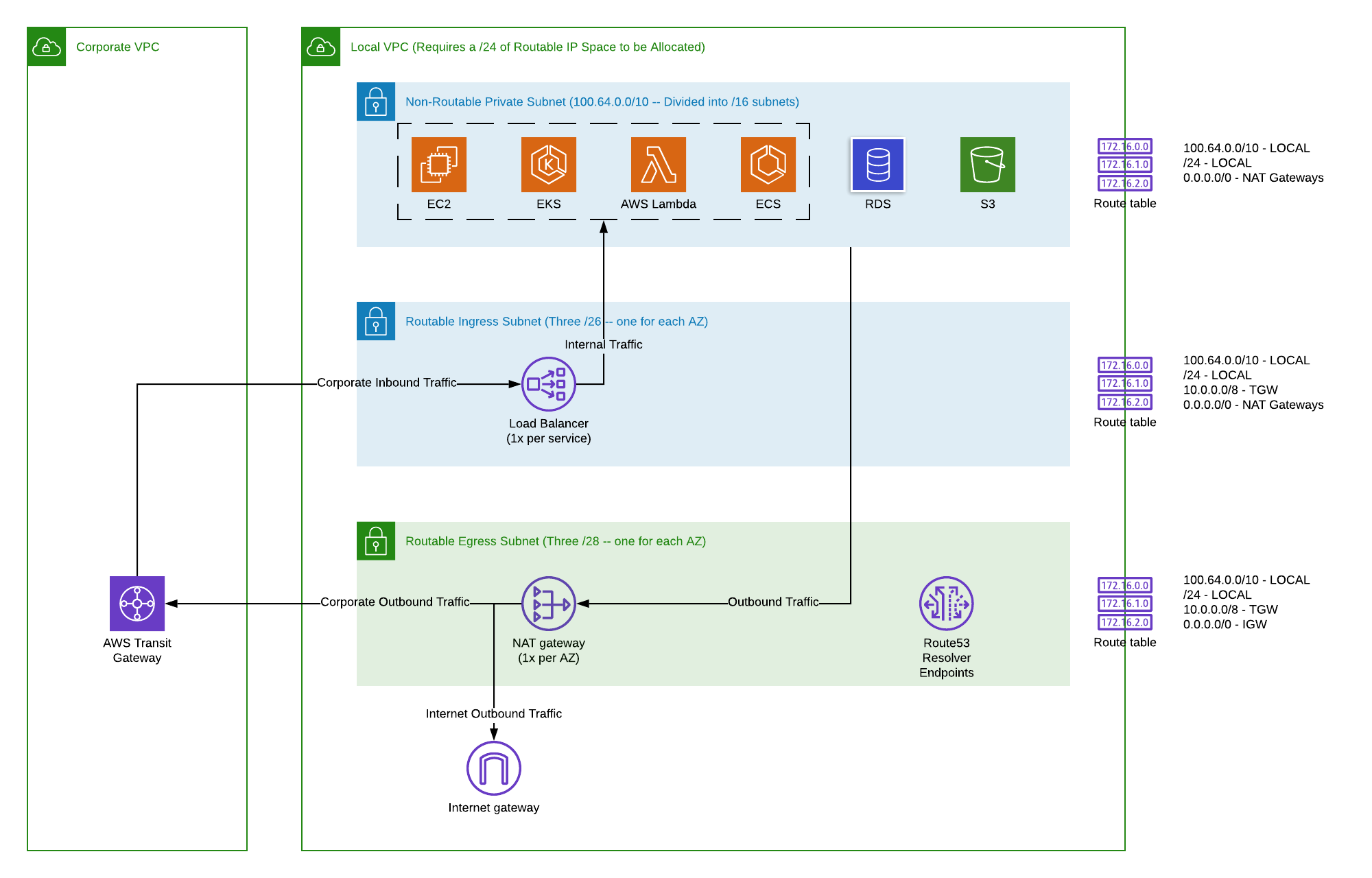
# Securing Remote IoT with AWS VPC Networks **In today's rapidly evolving digital landscape, the proliferation of Internet of Things (IoT) devices has opened up unprecedented opportunities for innovation across countless industries. From smart cities and industrial automation to remote healthcare monitoring and precision agriculture, IoT is transforming how we interact with the physical world. However, the very nature of remote IoT deployments – often geographically dispersed and operating in challenging environments – introduces significant security and connectivity challenges. This is where a robust and well-architected network solution becomes not just beneficial, but absolutely critical. Building a secure and scalable **remoteiot vpc network aws** is the cornerstone of any successful and resilient IoT strategy.** The journey into the world of remote IoT is exciting, but it demands meticulous planning, especially concerning network infrastructure. Without a dedicated, secure, and highly controlled environment, your IoT devices risk exposure to myriad vulnerabilities, leading to potential data breaches, operational disruptions, and significant financial losses. Leveraging Amazon Web Services (AWS) Virtual Private Cloud (VPC) provides the foundational security and flexibility needed to manage these complex, distributed systems effectively. *** ### Table of Contents * [The Imperative of a Dedicated Network for Remote IoT](#the-imperative-of-a-dedicated-network-for-remote-iot) * [Understanding AWS VPC: Your Private Cloud Canvas](#understanding-aws-vpc-your-private-cloud-canvas) * [Designing a Secure Remote IoT VPC Architecture](#designing-a-secure-remote-iot-vpc-architecture) * [Isolating IoT Endpoints for Enhanced Security](#isolating-iot-endpoints-for-enhanced-security) * [Leveraging AWS IoT Core and VPC Endpoints](#leveraging-aws-iot-core-and-vpc-endpoints) * [Connectivity Strategies for Remote IoT Devices](#connectivity-strategies-for-remote-iot-devices) * [Implementing Robust Security Measures within Your VPC](#implementing-robust-security-measures-within-your-vpc) * [Monitoring and Troubleshooting Your Remote IoT VPC Network](#monitoring-and-troubleshooting-your-remote-iot-vpc-network) * [Visualizing Network Flow with VPC Flow Logs](#visualizing-network-flow-with-vpc-flow-logs) * [Responding to Network Incidents and Optimizing Performance](#responding-to-network-incidents-and-optimizing-performance) * [Scalability and Future-Proofing Your IoT Infrastructure](#scalability-and-future-proofing-your-iot-infrastructure) * [The E-E-A-T and YMYL Principles in IoT Networking](#the-e-e-a-t-and-ymyl-principles-in-iot-networking) *** ### The Imperative of a Dedicated Network for Remote IoT In the realm of remote IoT, devices often operate in diverse and sometimes hostile environments, from remote oil rigs to agricultural fields, smart city sensors, or even in-home medical devices. These devices collect and transmit sensitive data, making their connectivity and security paramount. Traditional network setups, often designed for human-centric interactions or centralized data centers, simply fall short when it comes to the unique demands of IoT. They may lack the granular control, isolation, and scalability required to manage thousands or even millions of devices securely. Imagine trying to understand the full "big picture" of a complex system without proper diagnostic tools. Just as 3D imaging helps medical professionals visualize the intricate network of an artery, including the location of smaller branch arteries and how well a stent is apposed, a dedicated network architecture provides a comprehensive "big picture" of your IoT ecosystem. It allows you to see the location of every device, how well its connectivity is established, and identify any potential points of failure or vulnerability. Without this clear visibility and control, managing a distributed IoT fleet becomes a high-risk endeavor. The imperative is clear: you need a network that provides isolation, control, and visibility, specifically tailored for the unique characteristics of remote IoT. ### Understanding AWS VPC: Your Private Cloud Canvas At the heart of building a secure **remoteiot vpc network aws** lies the Amazon Virtual Private Cloud (VPC). Think of an AWS VPC as your own isolated, private section of the AWS cloud, where you can launch AWS resources in a virtual network that you define. This gives you complete control over your virtual networking environment, including your own IP address ranges, subnets, route tables, network gateways, and security settings. This level of control is akin to having a detailed, interactive map of a city, like Riverside, CA, at your fingertips. Just as an open street map of Riverside features a full detailed scheme of streets and roads, allowing you to use plus/minus buttons to zoom in or out, an AWS VPC provides a comprehensive overview of your network. You can define specific "streets" (subnets) for different types of traffic or devices, set "traffic rules" (route tables), and establish "checkpoints" (Network ACLs and Security Groups) to control who and what can enter or leave your network segments. This granular control is essential for creating a highly secure and manageable environment for your remote IoT devices. It's your private canvas, ready for you to paint the ideal network architecture. ### Designing a Secure Remote IoT VPC Architecture Designing a secure **remoteiot vpc network aws** architecture begins with the principle of least privilege and robust segmentation. For IoT, this often means separating devices, control planes, data processing, and user access into distinct network segments. This approach limits the blast radius in case of a security incident, ensuring that a compromise in one area does not automatically jeopardize the entire system. Best practices dictate using a multi-tiered architecture with public and private subnets. Public subnets might host services that need internet accessibility (e.g., a load balancer for a public API), while private subnets are reserved for sensitive resources like IoT devices, databases, and backend processing applications. #### Isolating IoT Endpoints for Enhanced Security A core tenet of secure IoT networking is to keep your devices as isolated as possible from the public internet. This is where private subnets become invaluable. By deploying your remote IoT devices within private subnets, they cannot be directly accessed from the internet, significantly reducing their attack surface. Communication with these devices is then routed through controlled gateways or services, such as AWS IoT Core, which acts as a secure intermediary. This strategy is much like how doctors can look inside a person’s heart without opening their chest, using advanced imaging techniques like MRI. Similarly, with a well-designed VPC, you gain deep visibility and control over your IoT endpoints without exposing them directly to the dangers of the open internet. You can monitor their health, traffic, and status, and tailor their "treatment" (security policies and configurations) to keep them "healthier longer," all from a secure, remote vantage point. This isolation is a critical layer of defense, ensuring that only authorized and necessary communication paths exist. #### Leveraging AWS IoT Core and VPC Endpoints AWS IoT Core is a managed cloud platform that lets connected devices easily and securely interact with cloud applications and other devices. When integrating IoT Core with your VPC, the use of VPC Endpoints becomes a game-changer. A VPC Endpoint allows you to privately connect your VPC to supported AWS services (like IoT Core) without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. This means your IoT devices can communicate with AWS IoT Core entirely within the AWS network, never traversing the public internet. This private connectivity enhances security and reduces latency, making your **remoteiot vpc network aws** more robust and efficient. It's about creating direct, secure highways within your private cloud, ensuring that sensitive IoT data travels along protected routes. By using VPC Endpoints for IoT Core, you establish a highly secure and performant communication channel, minimizing exposure and bolstering the overall integrity of your IoT solution. ### Connectivity Strategies for Remote IoT Devices Connecting remote IoT devices to your AWS VPC requires careful consideration of various connectivity strategies, depending on device location, data volume, and latency requirements. For devices in fixed locations with high bandwidth needs, AWS Direct Connect offers a dedicated network connection from your premises to AWS, bypassing the public internet. For more distributed or temporary deployments, AWS Site-to-Site VPN provides a secure, encrypted tunnel over the internet. These options allow your remote IoT devices to seamlessly integrate into your VPC as if they were physically present in your data center. For edge devices that require low-latency processing or operate with intermittent connectivity, AWS IoT Greengrass extends AWS cloud capabilities to local devices. This allows devices to perform local compute, messaging, data caching, sync, and machine learning inference. Greengrass-enabled devices can then securely communicate with the AWS cloud and other Greengrass devices. This holistic approach to connectivity is like getting directions, maps, and traffic reports for your entire network. Whether your devices are in Palm Springs, Corona, Moreno Valley, or Indian Wells, or any other remote location, you can map their connectivity, understand traffic flow, and ensure reliable communication pathways, much like navigating a detailed map of a county with various junctions and campuses. ### Implementing Robust Security Measures within Your VPC Security is not a feature; it's a fundamental requirement, especially for a **remoteiot vpc network aws**. Beyond network isolation, implementing robust security measures within your VPC is paramount. AWS provides a comprehensive suite of tools to enforce security at multiple layers: * **Security Groups:** Act as virtual firewalls at the instance level, controlling inbound and outbound traffic for individual EC2 instances or network interfaces. They are stateful, meaning if you allow inbound traffic, the outbound response is automatically allowed. * **Network ACLs (NACLs):** Operate at the subnet level, providing a stateless firewall that controls traffic entering and leaving the subnet. They offer an additional layer of defense, allowing you to explicitly permit or deny traffic based on IP addresses, ports, and protocols. * **IAM Policies:** AWS Identity and Access Management (IAM) allows you to securely control who (or what) can access your AWS resources. For IoT, this means defining fine-grained permissions for devices, applications, and users interacting with your IoT Core, data stores, and other AWS services. * **Encryption:** Data encryption is critical both in transit and at rest. AWS services automatically integrate with AWS Key Management Service (KMS) to encrypt data stored in services like S3, DynamoDB, and RDS. For data in transit, TLS/SSL encryption is standard for communication between devices and AWS IoT Core. These measures collectively ensure that your network is resilient against unauthorized access and data breaches. It's about "tailoring treatment" for your network to keep it "healthier longer," preventing "diseases" (vulnerabilities) before they can take hold. By meticulously configuring these security layers, you create a fortress around your remote IoT operations. ### Monitoring and Troubleshooting Your Remote IoT VPC Network Even the most meticulously designed network requires continuous monitoring and a robust troubleshooting framework. For a **remoteiot vpc network aws**, this involves leveraging AWS's native monitoring tools to gain deep insights into network performance, traffic patterns, and potential security threats. * **AWS CloudWatch:** Provides comprehensive monitoring for AWS resources and applications. You can collect and track metrics, create custom dashboards, and set alarms to notify you of operational issues or abnormal behavior within your VPC. * **VPC Flow Logs:** Capture information about the IP traffic going to and from network interfaces in your VPC. These logs are invaluable for troubleshooting connectivity issues, analyzing traffic patterns, and detecting unauthorized access attempts. * **AWS Network Firewall:** A managed service that makes it easier to deploy essential network protections for all your VPCs. It provides intrusion prevention, deep packet inspection, and filtering capabilities at scale. #### Visualizing Network Flow with VPC Flow Logs VPC Flow Logs are perhaps one of the most powerful tools for understanding what's happening within your **remoteiot vpc network aws**. They provide a detailed record of network traffic, including source and destination IP addresses, ports, protocols, and the number of bytes transferred. This is analogous to a "Map my county" reporting tool, which aids users in obtaining both mapping and reporting of over 80 layers that the county hosts or maintains. Just as you can analyze GIS layers to understand geographical data, Flow Logs allow you to analyze network layers to understand traffic flow. By analyzing Flow Logs, you can visualize who is talking to whom, identify unexpected traffic patterns, detect port scans, or pinpoint devices attempting to communicate with unauthorized destinations. This granular visibility is crucial for proactive security and efficient troubleshooting. It helps you understand the "traffic report" of your network, identifying "outages" or bottlenecks before they escalate. #### Responding to Network Incidents and Optimizing Performance Effective monitoring isn't just about collecting data; it's about acting on it. When anomalies are detected, a well-defined incident response plan is essential. This might involve automated responses triggered by CloudWatch alarms (e.g., isolating a compromised device using Lambda functions) or manual intervention by network engineers. Beyond incident response, continuous optimization of your **remoteiot vpc network aws** is vital for maintaining performance and cost-efficiency. This requires a certain "intuition," a method of feeling one’s way intellectually into the inner heart of a thing to locate the root cause of issues or identify areas for improvement. Just as doctors at Mayo Clinic use MRIs to look inside the heart to find disease and tailor treatment, network engineers use advanced analytics and their expertise to diagnose network "diseases" and "tailor treatment" (e.g., optimize routing, adjust security policies, scale resources) to keep the network running smoothly and efficiently. This proactive approach ensures your IoT infrastructure remains robust and adaptable. ### Scalability and Future-Proofing Your IoT Infrastructure The nature of IoT is inherently scalable. What starts as a pilot project with a few hundred devices can quickly grow to tens of thousands or even millions. Your **remoteiot vpc network aws** must be designed with this growth in mind. AWS's elastic infrastructure allows you to scale resources up or down dynamically, ensuring your network can handle fluctuating traffic loads without performance degradation. This scalability is fundamental, much like the seven main functions of the heart, which include pumping blood throughout the body, delivering oxygen to tissues, and removing waste. A scalable network ensures continuous data flow, efficient resource delivery to devices, and effective removal of unnecessary traffic. Leveraging serverless architectures like AWS Lambda for backend processing and AWS Fargate for containerized applications can further enhance scalability by abstracting away server management, allowing you to focus purely on your application logic. Furthermore, AWS's global network of regions and Availability Zones provides inherent redundancy and allows you to deploy your IoT infrastructure closer to your devices, reducing latency and improving resilience. By designing for growth from the outset, you future-proof your investment in remote IoT. ### The E-E-A-T and YMYL Principles in IoT Networking When discussing a **remoteiot vpc network aws**, the principles of E-E-A-T (Expertise, Authoritativeness, Trustworthiness) and YMYL (Your Money or Your Life) are not just SEO buzzwords; they are foundational to the integrity and reliability of your IoT solution. * **Expertise:** Building and maintaining a secure IoT network on AWS requires deep technical expertise in cloud networking, security, and IoT protocols. It's not a task for the uninitiated. Leveraging AWS best practices and certified professionals ensures that your network is designed and operated by those with proven knowledge. * **Authoritativeness:** The architecture you choose and the configurations you implement must be based on authoritative sources, primarily AWS documentation, security whitepapers, and industry standards. Relying on unverified information can lead to critical vulnerabilities. * **Trustworthiness:** Ultimately, your IoT solution must be trustworthy. This means ensuring data privacy, device integrity, and continuous availability. Users and stakeholders must trust that their data is secure and that the system will perform as expected. The YMYL criteria are particularly relevant in many IoT applications. For instance, in remote healthcare monitoring, a network failure could literally impact someone's life. In industrial automation, a security breach could lead to significant financial loss, environmental damage, or even physical harm. When "your money" or "your life" is on the line, the network underpinning your IoT solution must be beyond reproach. It's about recognizing that "everything that you want, you already are" capable of achieving with the right architecture and expertise, but the responsibility to implement it correctly is paramount. This makes the robust, secure, and well-managed **remoteiot vpc network aws** not just a technical choice, but a critical business and ethical imperative. ### Conclusion Building a secure and scalable **remoteiot vpc network aws** is an essential undertaking for any organization venturing into the world of connected devices. As we've explored, AWS VPC provides the isolated, controllable, and flexible environment needed to manage the unique challenges of remote IoT deployments. From segmenting your network and leveraging private endpoints to implementing robust security measures and continuously monitoring traffic, a well-architected VPC ensures the confidentiality, integrity, and availability of your IoT data and devices. The journey to a successful IoT deployment is complex, but by focusing on a strong network foundation within AWS, you empower your devices to operate securely and efficiently, no matter how remote. This strategic approach mitigates risks, enhances performance, and sets the stage for future innovation. We encourage you to delve deeper into AWS's extensive documentation on VPC and IoT services, and consider consulting with AWS certified experts to tailor a solution that perfectly fits your unique operational needs. Share your experiences or questions in the comments below – let's continue to build a more secure and connected world, one robust network at a time.
Related Resources:


Detail Author:
- Name : Mr. Murl Wehner
- Username : gjohnston
- Email : clarissa.haley@willms.com
- Birthdate : 1970-12-14
- Address : 84075 Kessler Valleys New Jackyport, ME 25115-2241
- Phone : 424.578.6003
- Company : Bernier and Sons
- Job : Hazardous Materials Removal Worker
- Bio : Laborum autem autem delectus recusandae et. Quod et eum qui veniam. Animi non deleniti veritatis ut magnam harum.
Socials
twitter:
- url : https://twitter.com/elzaprohaska
- username : elzaprohaska
- bio : Ab quaerat eligendi eos explicabo sint aut. Dignissimos enim aut et harum animi hic.
- followers : 2029
- following : 2344
tiktok:
- url : https://tiktok.com/@prohaska1986
- username : prohaska1986
- bio : Rerum voluptatem provident enim esse. Excepturi et quis ducimus.
- followers : 5285
- following : 823
instagram:
- url : https://instagram.com/elza_prohaska
- username : elza_prohaska
- bio : Et inventore et voluptas dolorum libero facere. Sit dolor veniam numquam repudiandae quas.
- followers : 3849
- following : 1665
linkedin:
- url : https://linkedin.com/in/elzaprohaska
- username : elzaprohaska
- bio : Sapiente eaque voluptatem cumque officiis id et.
- followers : 2312
- following : 910