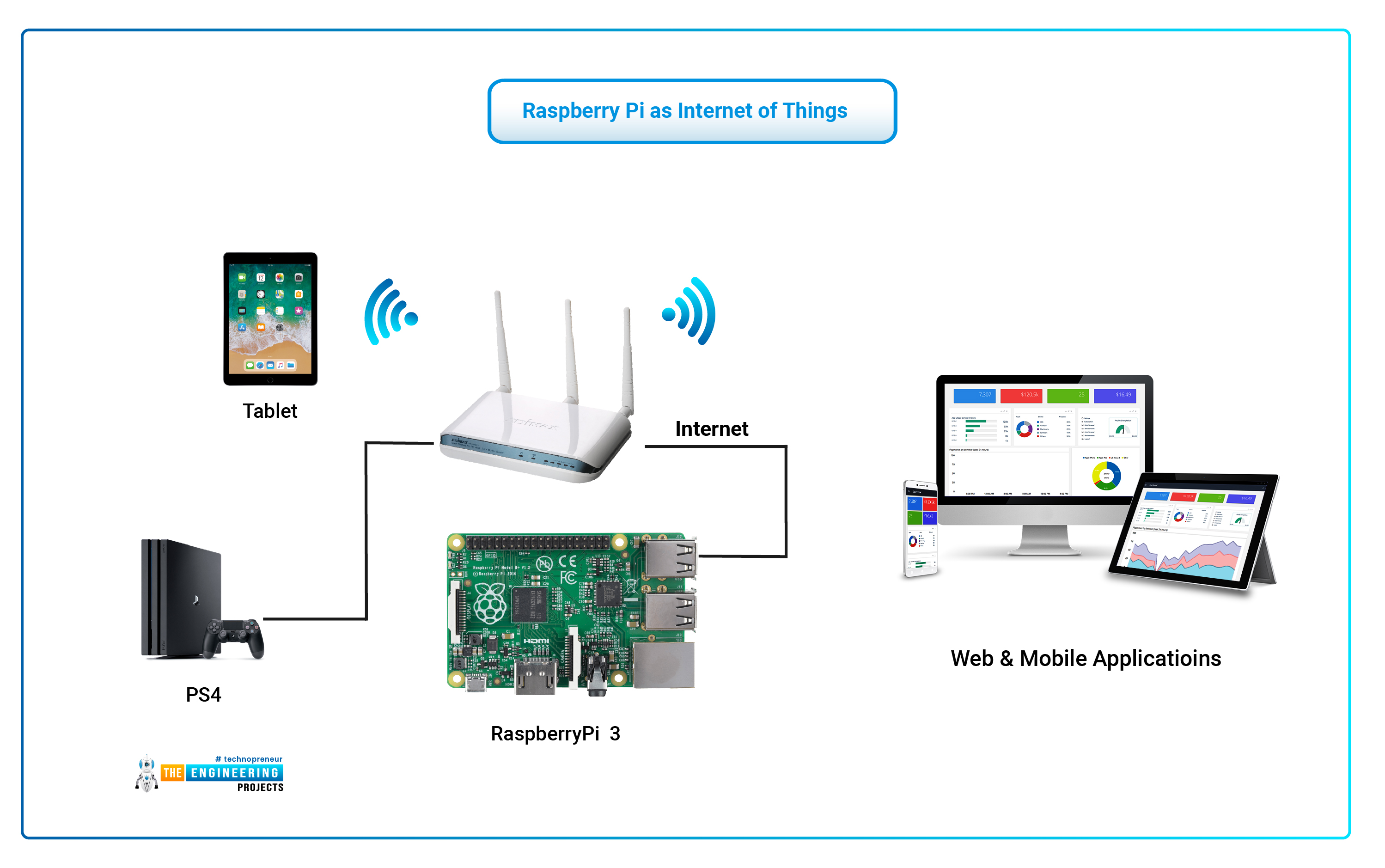
In today's interconnected world, the ability to access and control devices remotely is no longer a luxury but a necessity. For enthusiasts and professionals alike, setting up `remoteiot behind router raspberry pi` devices presents a unique blend of challenge and opportunity. While a Raspberry Pi offers incredible versatility for various Internet of Things (IoT) projects, the hurdle of accessing it from outside your local network, especially when it's tucked away behind a router, can seem daunting. This article will demystify the process, offering practical, secure, and reliable methods to ensure your IoT projects remain accessible, no matter where you are.
From smart home automation to environmental monitoring stations, a Raspberry Pi serves as an affordable and powerful brain for countless IoT applications. However, the default network configuration, where your router acts as a gatekeeper, often prevents direct external access. Understanding the underlying networking principles and employing the right techniques are crucial steps toward building truly robust and accessible remote IoT systems. We'll explore various strategies, from traditional port forwarding to advanced cloud-based solutions, ensuring you can choose the best approach for your specific needs while prioritizing security and performance.
Table of Contents
- The Challenge of Remote IoT Behind a Router
- Why Raspberry Pi is Ideal for Remote IoT
- Core Techniques for Remote Access
- Cloud-Based Solutions for Seamless Connectivity
- Reverse SSH Tunnels: A Stealthy Gateway
- Security Best Practices for Remote IoT
- Troubleshooting Common Remote Access Issues
- Future Trends and Advanced Remote IoT Architectures
The Challenge of Remote IoT Behind a Router
At the heart of the challenge of accessing `remoteiot behind router raspberry pi` lies Network Address Translation (NAT). Your home router acts as a translator, allowing multiple devices on your private local network (LAN) to share a single public IP address provided by your Internet Service Provider (ISP). When you try to connect to your Raspberry Pi from outside your home network, the incoming connection hits your router's public IP address. Without specific instructions, the router doesn't know which internal device (your Raspberry Pi) the incoming request is intended for, and thus, it drops the connection. This is a fundamental security feature, preventing unsolicited access to your internal network, but it also creates a barrier for legitimate remote access to your IoT devices.
Consider a typical home network: your laptop, smartphone, and Raspberry Pi all have private IP addresses (e.g., 192.168.1.10, 192.168.1.11, 192.168.1.12). Your router has one public IP address (e.g., 203.0.113.45). When your Raspberry Pi sends data to the internet, the router rewrites the source IP address to its public one. When data comes back, the router remembers which internal device initiated the outgoing connection and routes the response accordingly. However, for an *unsolicited* incoming connection, the router has no such mapping, making direct access impossible without configuration. Overcoming this requires techniques that either tell the router where to send incoming traffic or establish an outbound connection from the Raspberry Pi to an accessible intermediary.
Why Raspberry Pi is Ideal for Remote IoT
The Raspberry Pi has emerged as a cornerstone for remote IoT development for several compelling reasons. Its low cost makes it accessible to hobbyists and professionals alike, allowing for experimentation and deployment without significant financial outlay. Beyond cost, its compact size and low power consumption mean it can be deployed in a wide array of environments, from a sensor node in a remote garden to a smart home hub discreetly placed in a living room. The Pi's versatility is further enhanced by its GPIO (General Purpose Input/Output) pins, which enable direct interfacing with sensors, actuators, and other electronic components, making it a true physical computing platform.
Crucially, the Raspberry Pi benefits from an incredibly vibrant and supportive community. This ecosystem provides a wealth of resources, including detailed tutorials, pre-built software images, and active forums where solutions to common challenges, including how to manage `remoteiot behind router raspberry pi` setups, are readily available. The availability of various operating systems, predominantly different flavors of Linux (like Raspberry Pi OS), provides a robust and familiar environment for developers, offering powerful command-line tools and scripting capabilities essential for managing remote devices. This combination of hardware capability, software flexibility, and community support solidifies the Raspberry Pi's position as an ideal platform for remote IoT projects.
Core Techniques for Remote Access
To establish reliable access to your `remoteiot behind router raspberry pi`, several core networking techniques can be employed. Each method has its own set of advantages, disadvantages, and security implications, making the choice dependent on your specific project requirements and risk tolerance.
Port Forwarding: The Direct Approach
Port forwarding is arguably the most straightforward method for allowing external access to a device on your local network. It involves configuring your router to direct incoming traffic on a specific public port to a specific private IP address and port on your Raspberry Pi. For instance, if you want to access your Pi's SSH server (which typically runs on port 22), you would configure your router to forward incoming traffic on a chosen public port (e.g., 2222) to your Raspberry Pi's private IP address (e.g., 192.168.1.10) on port 22. This effectively punches a hole through your router's NAT, making your Raspberry Pi directly accessible from the internet.
While simple to set up, port forwarding carries significant security risks. By exposing a service directly to the internet, you make your Raspberry Pi a potential target for malicious actors. It's crucial to ensure that any service exposed is fully secured with strong passwords, SSH key authentication, and up-to-date software. Furthermore, if your ISP uses Carrier-Grade NAT (CGNAT), you might not have a unique public IP address, rendering traditional port forwarding ineffective. To set up port forwarding, you typically log into your router's administration interface (usually via a web browser), navigate to the "Port Forwarding" or "NAT" section, and create a new rule specifying the external port, internal IP, and internal port.
VPNs: Secure Remote Access
Virtual Private Networks (VPNs) offer a much more secure and flexible solution for accessing your `remoteiot behind router raspberry pi`. Instead of exposing individual services, a VPN creates an encrypted tunnel between your remote device (e.g., your laptop) and your home network. Once connected to the VPN, your remote device essentially becomes part of your home network, allowing you to access all your local devices, including your Raspberry Pi, as if you were physically at home. This eliminates the need for port forwarding individual services and provides an additional layer of encryption for all traffic.
Setting up a VPN server on your Raspberry Pi using solutions like OpenVPN or WireGuard is a popular and highly recommended approach. OpenVPN is robust and widely supported, while WireGuard offers a more modern, lightweight, and faster alternative. Both require some command-line configuration on the Raspberry Pi. Once the VPN server is running, you configure a VPN client on your remote device. When you connect, all your traffic to your home network is securely tunneled, allowing you to SSH into your Pi, access web servers, or interact with any other service as if you were on the local network. While setting up a VPN requires a bit more technical expertise than simple port forwarding, the security benefits and flexibility it provides are well worth the effort, especially for sensitive IoT applications.
Cloud-Based Solutions for Seamless Connectivity
For those seeking a highly scalable, robust, and often simpler way to manage `remoteiot behind router raspberry pi` deployments, cloud-based IoT platforms present an excellent alternative. These platforms abstract away the complexities of direct network access by relying on an "always-on" outbound connection from your Raspberry Pi to a cloud broker. Instead of initiating connections *to* your Pi, you interact with your Pi through the cloud service, which acts as a secure intermediary.
MQTT (Message Queuing Telemetry Transport) is a lightweight messaging protocol widely used in IoT, making it ideal for communication between your Raspberry Pi and a cloud platform. Your Raspberry Pi can publish sensor data to an MQTT broker hosted in the cloud, and it can subscribe to topics to receive commands from a remote application or dashboard. Major cloud providers like AWS IoT Core, Azure IoT Hub, and Google Cloud IoT Core offer comprehensive services that include MQTT brokers, device management, data analytics, and integration with other cloud services. These platforms handle the network complexities, security, and scalability, allowing you to focus on your IoT application logic. While they typically involve a recurring cost, the benefits of managed services, built-in security features, and global accessibility often outweigh the expense for professional or large-scale deployments. They are particularly effective when your Raspberry Pi is behind a router that you cannot configure (e.g., in a public Wi-Fi network or a managed building network) or when dealing with dynamic IP addresses.
Reverse SSH Tunnels: A Stealthy Gateway
Reverse SSH tunnels offer an ingenious method to access your `remoteiot behind router raspberry pi` when direct incoming connections (like those used in port forwarding) are not possible or desired. This technique involves your Raspberry Pi initiating an *outbound* SSH connection to a publicly accessible intermediate server (often a cheap VPS or another machine you control with a public IP). This outbound connection then creates a "tunnel" that can be used to forward incoming connections from the intermediate server back to your Raspberry Pi.
Here's how it works: Your Raspberry Pi (the client) connects to the intermediate server (the host) and requests that a specific port on the *host* be forwarded to a specific port on the *client*. For example, the Pi might execute `ssh -R 8080:localhost:22 user@your_vps_ip`. This command tells the VPS to listen on port 8080 and forward any connections it receives on that port back through the SSH tunnel to port 22 (SSH) on the Raspberry Pi. Now, when you want to access your Pi, you simply SSH into your VPS on port 8080 (e.g., `ssh -p 8080 user@your_vps_ip`), and your connection is seamlessly routed to your Raspberry Pi. This method is particularly useful because the Raspberry Pi initiates the connection, which is usually allowed by routers, even those with strict firewall rules. It's a powerful technique for reaching devices behind NAT without router configuration, making it a favorite among developers for quick, secure remote access to `remoteiot behind router raspberry pi` instances.
Security Best Practices for Remote IoT
When you enable remote access to your `remoteiot behind router raspberry pi`, you are inherently increasing its exposure to potential threats. Neglecting security can lead to unauthorized access, data breaches, or even the compromise of your entire home network. Implementing robust security measures is not optional; it's absolutely critical for any remotely accessible IoT device.
Strong Authentication and Encryption
The first line of defense is strong authentication. For SSH access, disable password-based login and exclusively use SSH key-based authentication. Generate strong, unique SSH keys, store your private key securely, and ensure your public key is correctly installed on the Raspberry Pi. Consider implementing two-factor authentication (2FA) for an additional layer of security, especially if your Raspberry Pi hosts sensitive data or controls critical systems. Regularly rotate your SSH keys, particularly if you suspect they might have been compromised.
Encryption is equally vital for protecting data in transit. For web services, always use HTTPS (TLS/SSL) to encrypt communication between your browser and the Raspberry Pi. Tools like Let's Encrypt can provide free SSL certificates. For MQTT, ensure you're using MQTT over TLS (MQTTS). VPNs inherently provide encryption for all tunneled traffic. Always ensure that the protocols and services you use support and enforce strong encryption standards to prevent eavesdropping and tampering.
Firewall Rules and Network Segmentation
Even with secure authentication, limiting the attack surface is paramount. Implement firewall rules on your Raspberry Pi using `iptables` or `ufw` (Uncomplicated Firewall) to restrict incoming connections only to necessary ports and, if possible, to specific trusted IP addresses. For example, if you only need SSH access, block all other incoming ports. If you know the specific IP address you'll be connecting from, you can configure your firewall to only allow SSH connections from that IP, significantly reducing exposure.
Network segmentation, though more advanced, offers an excellent way to contain potential breaches. If your router supports VLANs (Virtual Local Area Networks), consider placing your IoT devices on a separate VLAN, isolated from your main home network. This way, even if an IoT device is compromised, the attacker's access is limited to that specific segment, preventing them from easily pivoting to your computers or other sensitive devices. Regularly update your Raspberry Pi's operating system and all installed software to patch known vulnerabilities. Unused services should be disabled to minimize potential entry points for attackers. A proactive approach to security is the best defense for your `remoteiot behind router raspberry pi` deployments.
Troubleshooting Common Remote Access Issues
Despite careful planning, you might encounter issues when trying to access your `remoteiot behind router raspberry pi` remotely. Troubleshooting is a systematic process of elimination. Start by verifying the most common culprits.
First, confirm your Raspberry Pi has a stable internet connection and is reachable within your local network. Can you ping it from another device on your LAN? Can it access external websites? Next, verify that the service you're trying to access (e.g., SSH server) is actually running on the Pi and listening on the correct port. Use `sudo systemctl status ssh` for SSH or `sudo netstat -tulnp` to see all listening ports.
If you're using port forwarding, double-check your router's configuration. Is the correct internal IP address for your Raspberry Pi specified? Is the internal port mapped correctly to the external port? Remember that your router's public IP address might change if your ISP assigns dynamic IPs; consider using a Dynamic DNS (DDNS) service to keep your hostname updated. If you suspect your ISP is using CGNAT, traditional port forwarding won't work, and you'll need to pivot to VPNs, reverse SSH, or cloud solutions.
Firewall rules, both on your router and on the Raspberry Pi itself, are frequent sources of connection problems. Temporarily disable the firewall on your Raspberry Pi (`sudo ufw disable` or flush `iptables` rules) to see if that resolves the issue (re-enable immediately after testing!). Check your router's firewall settings as well. Lastly, ensure that there are no conflicts with other services or devices on your network. Patience and methodical testing are key to resolving remote access challenges.
Future Trends and Advanced Remote IoT Architectures
The landscape of `remoteiot behind router raspberry pi` is continually evolving, driven by advancements in technology and a growing demand for more intelligent and efficient systems. Future trends point towards increasingly sophisticated architectures that enhance performance, security, and scalability. Edge computing, for instance, is gaining significant traction. Instead of sending all raw sensor data to the cloud for processing, edge computing involves performing computation and analysis directly on the Raspberry Pi or other edge devices. This reduces latency, conserves bandwidth, and enhances privacy by processing sensitive data locally before sending only aggregated or necessary information to the cloud. Raspberry Pi's increasing processing power makes it an excellent candidate for edge AI and machine learning applications.
Another emerging trend is the adoption of mesh networks and decentralized IoT architectures. Technologies like Thread and Zigbee allow IoT devices to form self-healing, self-organizing networks, extending coverage and improving reliability without relying solely on a central hub or a single Wi-Fi connection. While these are often local networks, their integration with remote access solutions (like a Raspberry Pi acting as a gateway to the internet) will become more seamless. Furthermore, the emphasis on robust cybersecurity will only intensify, with a greater focus on hardware-level security, secure boot processes, and zero-trust network models for IoT deployments. As the capabilities of the Raspberry Pi continue to expand, so too will the possibilities for complex, secure, and highly functional remote IoT systems, pushing the boundaries of what's achievable from behind your router.
Conclusion
Navigating the complexities of establishing `remoteiot behind router raspberry pi` access can initially seem daunting, but as we've explored, a variety of robust and secure methods are available. From the directness of port forwarding to the fortified tunnels of VPNs and reverse SSH, and the scalable convenience of cloud-based platforms, each approach offers a unique set of advantages tailored to different project needs. The Raspberry Pi's versatility, affordability, and strong community support make it an unparalleled platform for these endeavors.
Crucially, regardless of the method chosen, prioritizing security is non-negotiable. Strong authentication, robust encryption, and meticulous firewall configurations are the bedrock of any reliable remote IoT deployment. As you embark on your own remote IoT projects, remember that experimentation is key. Don't hesitate to try different techniques to find what best suits your specific use case. We encourage you to share your experiences, challenges, and successes in the comments below, or explore other articles on our site for more in-depth guides on optimizing your Raspberry Pi and IoT setups. The journey to a truly connected world begins with mastering remote access, and your Raspberry Pi is the perfect companion for this adventure.
Related Resources:


Detail Author:
- Name : Martine Zulauf Sr.
- Username : littel.juston
- Email : rohan.faye@gmail.com
- Birthdate : 1995-02-15
- Address : 299 Eloisa Lake Apt. 705 Cassieshire, HI 93218
- Phone : 1-920-392-1903
- Company : Kozey, Glover and Kassulke
- Job : Computer Systems Analyst
- Bio : Nihil voluptatem non est ex voluptatum. Explicabo ex ea et quam itaque optio. Tempora quod omnis sit pariatur tempore.
Socials
twitter:
- url : https://twitter.com/maida1136
- username : maida1136
- bio : Aut ullam commodi cum. Impedit distinctio et voluptatem. Quam officia eligendi optio a quia sapiente.
- followers : 2533
- following : 2054
facebook:
- url : https://facebook.com/maida.carroll
- username : maida.carroll
- bio : Consequatur in rem possimus dolorum sed.
- followers : 746
- following : 85
instagram:
- url : https://instagram.com/maida_carroll
- username : maida_carroll
- bio : Voluptatibus vero tempore occaecati perferendis. Quo ipsam modi culpa enim corrupti.
- followers : 2457
- following : 625
tiktok:
- url : https://tiktok.com/@mcarroll
- username : mcarroll
- bio : Sunt quasi aut accusamus voluptatem tempora ut qui.
- followers : 5345
- following : 583
linkedin:
- url : https://linkedin.com/in/mcarroll
- username : mcarroll
- bio : Dolorem sed unde quidem.
- followers : 3467
- following : 1881