In an increasingly interconnected world, the Internet of Things (IoT) is transforming industries and daily life. From smart homes to industrial sensors, these devices often operate in remote locations, demanding secure and efficient management. For Mac users, the challenge lies in finding reliable tools to interact with these distant devices. This is where the power of a remoteiot platform ssh download free mac solution becomes not just a convenience, but a critical necessity. Establishing a secure shell (SSH) connection is the gold standard for accessing, configuring, and maintaining your IoT infrastructure from the comfort of your macOS environment.
The ability to securely access and manage remote IoT devices is paramount for developers, system administrators, and enthusiasts alike. SSH provides an encrypted channel over an unsecured network, ensuring that all communications – commands, file transfers, and data – remain confidential and protected from eavesdropping or tampering. This comprehensive guide will delve into the intricacies of leveraging SSH for your remote IoT endeavors on a Mac, exploring everything from built-in tools to advanced techniques, ensuring you have the knowledge to maintain a robust and secure IoT ecosystem.
Table of Contents
- The Indispensable Role of SSH in Remote IoT Management
- Demystifying Remote IoT Platform SSH for Mac Users
- Finding Your Free SSH Client for Mac
- Navigating Secure File Transfers and Data Handling
- Advanced SSH Techniques for Robust IoT Operations
- Troubleshooting Common SSH Connection Issues
- Optimizing Your Remote IoT Workflow on Mac
- The Future of Remote IoT: Security, Accessibility, and Innovation
- Lildedjanet Leaked Twitter
- Westland Football
- Adrian Martinez Twitter
- Grace Charis Leaked Twitter
- Aaron Ehasz Twitter
The Indispensable Role of SSH in Remote IoT Management
The proliferation of IoT devices brings with it the challenge of managing them effectively and securely. Whether you're deploying a fleet of sensors in a remote agricultural field or managing smart devices within a smart city infrastructure, direct physical access is often impractical or impossible. This is where remote access protocols become indispensable, and among them, SSH stands out as the most trusted and widely adopted.
Why SSH is the Backbone of IoT Security
Security is not an afterthought in IoT; it's a foundational requirement. IoT devices, often resource-constrained and deployed in potentially vulnerable environments, are prime targets for cyberattacks. SSH, or Secure Shell, provides a cryptographic network protocol that enables secure data communication, remote command-line login, and other secure network services between two networked computers. Its robust encryption capabilities protect data in transit from eavesdropping, connection hijacking, and other malicious activities. This is crucial when you're sending sensitive configuration commands or retrieving proprietary data from your IoT devices.
Without SSH, managing remote IoT devices would typically involve insecure protocols, leaving your entire system vulnerable. Imagine sending a command to update firmware on a critical industrial IoT sensor over an unencrypted channel – any attacker could intercept that command, modify it, or even inject malicious code. SSH prevents such scenarios by creating a secure tunnel, making it the de facto standard for remote administration in the IoT landscape.
Bridging the Gap: Mac and Remote Devices
For Mac users, connecting to diverse IoT devices – which might run on Linux, embedded operating systems, or even custom firmware – requires a versatile and powerful client. macOS, being a Unix-based operating system, comes with a robust built-in SSH client, making it an ideal platform for remote IoT management. This native integration simplifies the process of establishing secure connections, transferring files, and executing commands on your remote devices. The ease of use combined with the inherent security of SSH makes a remoteiot platform ssh download free mac setup a seamless experience, allowing developers and administrators to focus on their IoT solutions rather than wrestling with connectivity issues.
Demystifying Remote IoT Platform SSH for Mac Users
Before diving into the practicalities, understanding the fundamental concepts behind SSH and how it integrates with a remote IoT platform is essential. This knowledge forms the bedrock for effective and secure remote management.
Understanding the Core Concepts
At its core, SSH operates on a client-server model. Your Mac acts as the SSH client, initiating a connection to the SSH server running on your remote IoT device. This connection is secured through public-key cryptography. When you connect, the server presents its public key, which your client verifies. If it's the first connection, you'll be prompted to accept the server's fingerprint. Once trust is established, authentication typically proceeds using either passwords or, more securely, SSH keys (a pair of cryptographic keys: a private key on your Mac and a public key on the IoT device).
A "remote IoT platform" in this context refers to the combination of your IoT devices (e.g., Raspberry Pis, ESP32s, industrial gateways) and any cloud services or local networks that facilitate their connectivity. SSH provides the direct, secure channel to the individual devices within this platform, allowing you to bypass web interfaces for deeper control, debugging, and system-level operations. This direct access is invaluable for tasks that require command-line interaction, such as installing packages, configuring network settings, or checking system logs.
Setting Up SSH on macOS: A Step-by-Step Guide
The beauty of macOS is that the SSH client is pre-installed and ready to use. You don't need to perform a separate remoteiot platform ssh download free mac operation for the client itself. Here's how to get started:
- Open Terminal: Navigate to Applications > Utilities > Terminal, or simply search for "Terminal" using Spotlight (Cmd + Space).
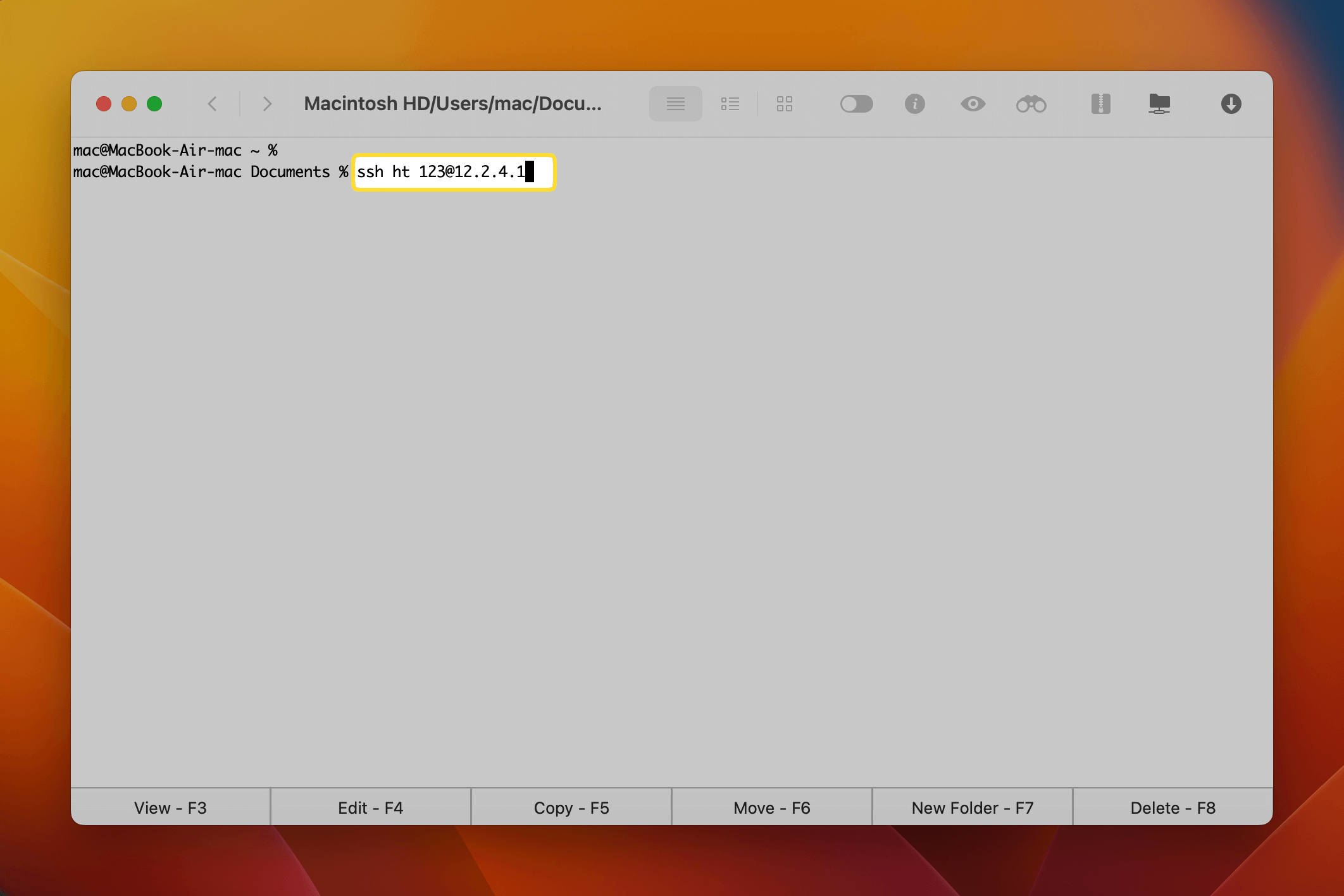
- Basic Connection Syntax: The fundamental command to connect is:
Replacessh username@remote_hostusernamewith the username on your IoT device (e.g.,pifor a Raspberry Pi) andremote_hostwith its IP address or hostname. For example:ssh pi@192.168.1.100 - First Connection & Fingerprint: The first time you connect to a new host, you'll see a message like:
TypeThe authenticity of host '192.168.1.100 (192.168.1.100)' can't be established. ECDSA key fingerprint is SHA256:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx. Are you sure you want to continue connecting (yes/no/[fingerprint])?yesand press Enter. This adds the host's fingerprint to your~/.ssh/known_hostsfile, preventing future warnings unless the host's key changes (which could indicate a security risk). - Password Authentication: If you're using password authentication, you'll be prompted to enter the password for the specified username on the remote device. Type it carefully (it won't show on screen) and press Enter.
- Success! If all goes well, you'll be logged into the command line of your remote IoT device.
Finding Your Free SSH Client for Mac
As established, macOS comes with a powerful, free, and pre-installed SSH client. However, depending on your workflow and specific needs, you might consider alternatives or enhancements.
Built-in Solutions: Terminal's Power
The Terminal application on your Mac is your primary gateway to SSH. It's a robust command-line interface that provides direct access to the underlying Unix system, including the ssh command. For most users and standard IoT management tasks, the built-in Terminal is more than sufficient. It's lightweight, fast, and integrates seamlessly with other macOS features. You can open multiple tabs or windows to manage different IoT devices simultaneously, and its capabilities extend to complex scripting and automation, which we'll touch upon later.
The fact that you don't need a separate remoteiot platform ssh download free mac download for the client itself simplifies the setup significantly, allowing you to focus immediately on connecting to your devices.
Third-Party Alternatives: When to Look Further
While the native Terminal is excellent, some users might prefer third-party SSH clients or terminal emulators for enhanced features, better user interfaces, or specific integrations. These often offer:
- Tab Management & Split Panes: More advanced ways to organize multiple connections.
- Session Management: Saving connection details, auto-login, and quick access to frequently used hosts.
- Visual SSH Key Management: Graphical interfaces for generating and managing SSH keys.
- Integrated SFTP/SCP Clients: Built-in file transfer capabilities within the same application window.
- Theming & Customization: Aesthetic enhancements and personalized workflows.
Popular options include iTerm2 (a highly customizable terminal emulator that replaces the default Terminal), Termius (a cross-platform SSH client with a strong focus on cloud integration and team collaboration), and Royal TSX (a comprehensive remote connection manager). While these might involve a download, many offer free versions or trials that provide significant utility for a remoteiot platform ssh download free mac user base looking for more features.
Navigating Secure File Transfers and Data Handling
Beyond executing commands, transferring files to and from your IoT devices is a common and critical task. SSH provides secure mechanisms for this, ensuring your data remains protected.
SCP and SFTP: Securely Moving Your IoT Data
SSH offers two primary protocols for secure file transfers:
- SCP (Secure Copy Protocol): A simple command-line utility for copying files between hosts over an SSH connection. It's ideal for quick, straightforward file transfers.
This allows you to push files to your IoT device (e.g., firmware updates, configuration files) or pull data logs back to your Mac for analysis.scp /local/path/to/file.txt username@remote_host:/remote/path/ scp username@remote_host:/remote/path/file.txt /local/path/ - SFTP (SSH File Transfer Protocol): A more feature-rich protocol that operates over SSH. It offers a more interactive file transfer experience, similar to FTP but with SSH's security. You can navigate directories, list files, and perform more complex file operations. Many graphical SFTP clients (like Cyberduck or Transmit) are available for Mac, providing a drag-and-drop interface for ease of use.
Both SCP and SFTP ensure that your file transfers are encrypted, preventing unauthorized access to your IoT data as it moves across the network. When dealing with large datasets or sensitive information from your IoT sensors, using these secure methods is non-negotiable.
Understanding Line Endings: \n, \r, and \r\n in Remote Files
When transferring text files between different operating systems (like macOS/Linux and Windows) via SSH, a subtle but significant detail can cause issues: line endings. This relates to the "What is difference in a string between \r\n, \r and \n, How is a string affected by each" query from the provided data.
\n(Newline): The standard line ending on Unix-like systems (including macOS and Linux, which most IoT devices run). It signifies a "line feed" – moving the cursor to the next line.\r(Carriage Return): Used primarily on very old Mac OS versions (pre-OS X). It signifies moving the cursor to the beginning of the current line. While rare as a standalone line ending today, it's crucial in the context of\r\n.\r\n(Carriage Return + Newline): The standard line ending on Windows systems. It signifies moving the cursor to the beginning of the next line.
The practical difference arises when a file created on one system is processed on another. For example, if you transfer a script from Windows (with \r\n) to a Linux-based IoT device, the shell might interpret the \r as part of the command, leading to "command not found" errors or unexpected behavior. Conversely, a file from an IoT device (with \n) opened on Windows might appear as one long line in Notepad. This is why tools like `dos2unix` (or `unix2dos`) are essential for converting line endings. When using `scp` or `sftp`, it's important to be aware of the source and destination operating systems and convert files if necessary, especially for scripts or configuration files. Python, for instance, on Windows makes a distinction between text and binary files, which can influence how line endings are handled during file operations. Using binary mode (e.g., `rb`, `wb`) explicitly can prevent automatic line ending conversions if you need to preserve the exact byte content.
Advanced SSH Techniques for Robust IoT Operations
Once you're comfortable with basic SSH connections, you can explore more advanced features that enhance security, convenience, and functionality for your remoteiot platform ssh download free mac setup.
SSH Key Management: The Gold Standard for Security
Relying solely on passwords for SSH authentication is less secure and less convenient than using SSH keys. SSH keys provide a much stronger form of authentication, eliminating the risk of brute-force password attacks and allowing for automated logins. Here's how to use them:
- Generate SSH Keys on Mac:
This command generates a pair of keys: a private key (e.g.,ssh-keygen -t rsa -b 4096id_rsa) stored securely on your Mac in~/.ssh/and a public key (e.g.,id_rsa.pub). Protect your private key with a strong passphrase. - Copy Public Key to IoT Device:
This command securely copies your public key to the remote IoT device'sssh-copy-id username@remote_host~/.ssh/authorized_keysfile. Ifssh-copy-idisn't available, you can manually copy the content of yourid_rsa.pubfile and paste it into theauthorized_keysfile on the remote device. - Log In Without Password: After the public key is on the remote device, you can simply use
ssh username@remote_host, and you'll be logged in without needing a password (or only needing your private key's passphrase if you set one).
This method significantly boosts the security of your remoteiot platform ssh download free mac connections.
Port Forwarding and Tunnelling: Beyond Direct Access
SSH can do more than just provide a shell. Port forwarding (or SSH tunnelling) allows you to securely tunnel network connections through an SSH connection. This is incredibly useful for IoT scenarios:
- Local Port Forwarding: Access a service running on your remote IoT device from your local Mac, even if the service's port isn't publicly exposed.
This command forwards local port 8888 on your Mac to port 80 on the remote host. Now, openingssh -L 8888:localhost:80 username@remote_hosthttp://localhost:8888in your Mac's browser will show the web server running on your IoT device. This is perfect for accessing a device's web interface or a local API securely. - Remote Port Forwarding: Allow a remote IoT device to access a service on your Mac (or another device on your local network) through the SSH tunnel. This is less common but useful for specific reverse proxy scenarios.
- Dynamic Port Forwarding (SOCKS Proxy): Turn your SSH connection into a SOCKS proxy, allowing you to route all your network traffic (e.g., web browsing) through the remote IoT device or a server it has access to. This can be useful for bypassing network restrictions or anonymizing traffic.
Then configure your browser or applications to usessh -D 8080 username@remote_hostlocalhost:8080as a SOCKS proxy.
These advanced techniques transform SSH into a versatile networking tool, providing secure access to various services within your IoT ecosystem.
Troubleshooting Common SSH Connection Issues
Even with a robust remoteiot platform ssh download free mac setup, you might encounter issues. Knowing how to diagnose and resolve them is crucial for maintaining uptime and productivity.
Diagnosing "No Return in Console" Scenarios
One common problem, as highlighted in the provided data, is when you run a command via SSH, and "there's no return in the console. I mean it does run the code, but does not return any output." This can be frustrating, but several factors can cause it:
- Output Redirection: The command might be redirecting its output to a file or
/dev/null. Check the script or command for `>` or `>>` operators. - Background Processes: The command might be designed to run in the background (e.g., using `nohup` or `&` at the end of the command). These processes detach from the console and won't produce output directly to your SSH session.
- Buffering: Sometimes, output is buffered and only flushed when a certain amount of data accumulates or the program exits. Try adding `unbuffer` (from `expect` package) or `stdbuf -oL` before your command if you need real-time output.
- Environment Variables: The remote environment might be missing necessary paths or libraries for the command to execute correctly or produce output.
- Permissions: The user running the command might not have permissions to write to a log file or access certain resources, causing silent failures.
- Network Latency/Timeouts: While less likely to cause *no* output, very high latency or dropped packets could make it seem like nothing is happening.
- Command Completion: The command might have completed successfully, but simply had no standard output. For example, a file copy command might not print anything on success.
To debug, try adding `echo` statements within scripts, checking log files on the remote device, or running the command with `strace` (if available) to see system calls and potential errors.
Permissions and Configuration Pitfalls
Many SSH issues stem from incorrect file permissions or misconfigurations:
- SSH Key Permissions: Your private key file on your Mac (`~/.ssh/id_rsa`) must have strict permissions (read-only for the owner: `chmod 400 ~/.ssh/id_rsa`). If permissions are too open, SSH will refuse to use the key.
- Remote
.sshDirectory Permissions: On the IoT device, the `~/.ssh` directory should be `700` (`drwx------`) and the `authorized_keys` file inside it should be `600` (`-rw-------`). - SSH Server Configuration: The `sshd_config` file on your IoT device (usually `/etc/ssh/sshd_config`) might have settings preventing connections (e.g., `PermitRootLogin no`, `PasswordAuthentication no`). Ensure the server is configured to allow your desired authentication method.
- Firewall Rules: Both on your Mac and the IoT device (and
Related Resources:
Detail Author:
- Name : Prof. Alexis Oberbrunner
- Username : tessie79
- Email : sandra68@gmail.com
- Birthdate : 1979-02-18
- Address : 760 Kling Radial Kileyside, MT 62858
- Phone : 740.495.6211
- Company : Gutmann PLC
- Job : Medical Laboratory Technologist
- Bio : Nemo molestiae eum natus adipisci et dolor maxime. Totam aut quos accusantium libero. Dolor doloremque veniam illum ipsum occaecati. Amet natus quisquam dolores ducimus veniam.
Socials
linkedin:
- url : https://linkedin.com/in/beulah.boehm
- username : beulah.boehm
- bio : Corporis qui quibusdam adipisci.
- followers : 5713
- following : 460
twitter:
- url : https://twitter.com/boehmb
- username : boehmb
- bio : Debitis earum tempore et eum dolor. Delectus consequatur ratione quae quis rem tenetur aliquid et. Nam non non ipsam beatae facere ipsum qui.
- followers : 1486
- following : 544
tiktok:
- url : https://tiktok.com/@boehmb
- username : boehmb
- bio : Aliquid eius sit illum amet velit iste.
- followers : 2160
- following : 156
facebook:
- url : https://facebook.com/beulah_boehm
- username : beulah_boehm
- bio : Animi qui omnis totam culpa sed similique. Saepe omnis est nesciunt quae quod.
- followers : 6477
- following : 375
instagram:
- url : https://instagram.com/beulahboehm
- username : beulahboehm
- bio : Rerum laudantium iusto odio nemo. Quod dolor et minima maxime. Veniam sunt id eum.
- followers : 616
- following : 2786