In the rapidly expanding world of the Internet of Things (IoT), the ability to remotely access and manage devices is paramount. However, a common hurdle for many enthusiasts and professionals alike is how to use RemoteIoT behind router without resorting to complex, often insecure, port forwarding configurations. This article delves deep into practical, secure, and efficient methods to achieve seamless remote access to your IoT devices, bypassing the traditional limitations imposed by Network Address Translation (NAT) and local network setups.
The challenge of connecting devices within a private network to the public internet without direct exposure has long plagued developers and system integrators. While port forwarding might seem like the most straightforward solution, it often introduces significant security vulnerabilities and management overhead, especially for dynamic IP addresses. Our goal here is to explore robust alternatives that allow you to effectively manage and interact with your RemoteIoT ecosystem, ensuring both accessibility and security, without the headaches of manual router configurations.
Table of Contents
- The Challenge of RemoteIoT Access Behind a Router
- Understanding RemoteIoT and Its Core Requirements
- Cloud-Based IoT Platforms: The Easiest "Without" Solution
- Reverse Proxy and Tunneling Services: A Robust Alternative
- MQTT Brokers with WebSockets: A Lightweight Approach
- Peer-to-Peer (P2P) Connections and NAT Traversal Techniques
- Software-Defined Networking (SDN) for IoT Connectivity
- Choosing the Right Method for Your RemoteIoT Deployment
The Challenge of RemoteIoT Access Behind a Router
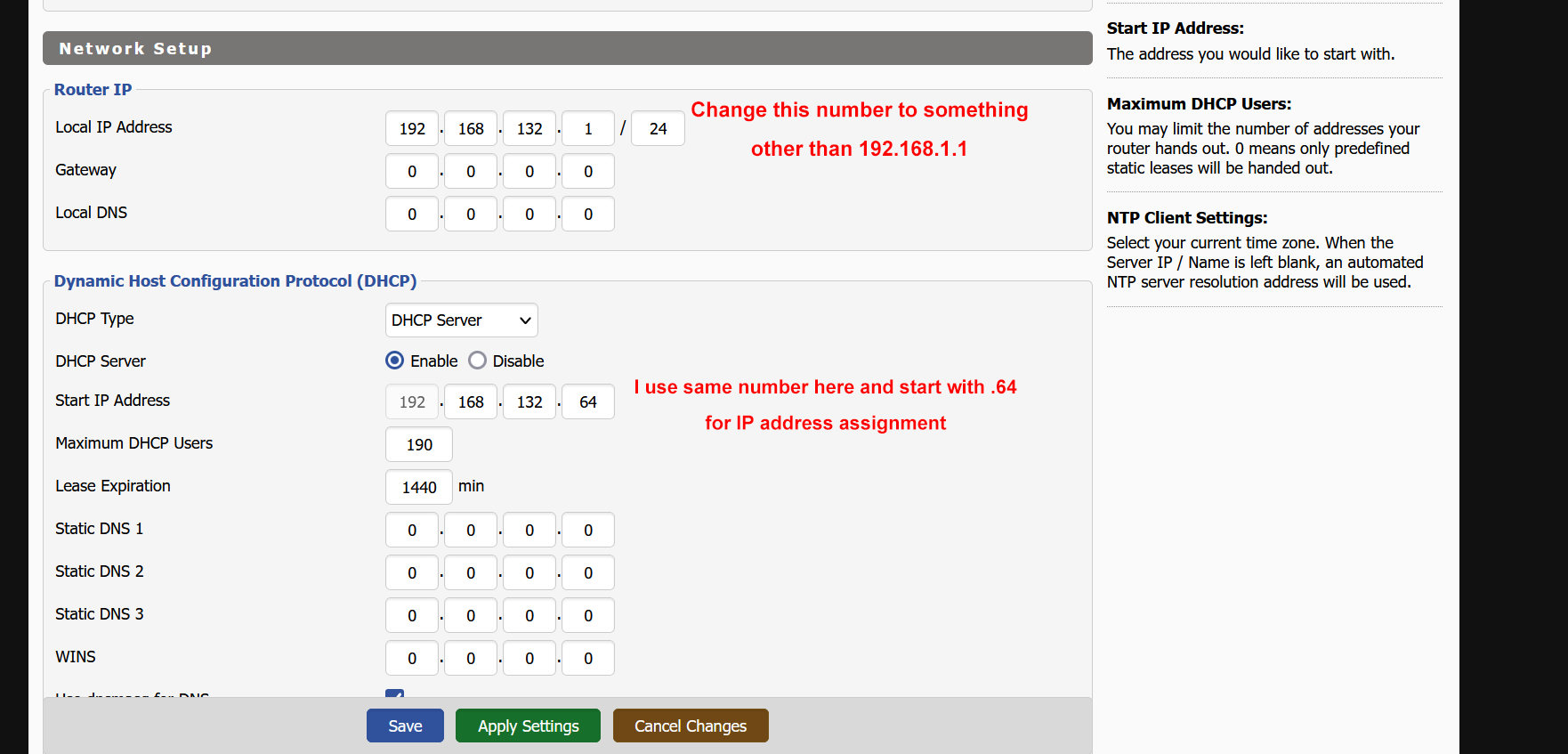
The vast majority of home and small business networks operate behind a router that performs Network Address Translation (NAT). This essential security feature allows multiple devices on a private local area network (LAN) to share a single public IP address provided by your Internet Service Provider (ISP). While excellent for conserving IP addresses and providing a basic layer of security by hiding internal network topology, NAT creates a significant barrier for inbound connections. Devices on your private network have private IP addresses (e.g., 192.168.1.x) that are not directly routable from the public internet. When you want to access an IoT device, like a smart camera or a home automation hub, from outside your home network, the router typically blocks these unsolicited incoming requests. The traditional solution, port forwarding, involves manually configuring your router to direct specific incoming traffic on a particular public port to a specific private IP address and port on your internal network. While effective, this method has several drawbacks:- Security Risks: Opening ports on your router can expose your internal devices to the internet, making them potential targets for malicious actors. It requires constant vigilance regarding device firmware updates and security patches.
- Complexity: For many users, navigating router settings and understanding port numbers, protocols, and IP addresses can be daunting.
- Dynamic IP Addresses: Most ISPs provide dynamic public IP addresses that change periodically. This means your port forwarding rule might become invalid, requiring manual updates or the use of Dynamic DNS (DDNS) services, adding another layer of complexity.
- Scalability: Managing port forwarding for multiple IoT devices, each potentially requiring its own port, quickly becomes unwieldy.
Understanding RemoteIoT and Its Core Requirements
Before diving into solutions, let's clarify what RemoteIoT entails and its fundamental requirements. RemoteIoT refers to the capability to interact with, monitor, and control Internet of Things devices from a location physically distant from the devices themselves. This could involve checking sensor readings from a smart garden, adjusting thermostat settings while on vacation, or troubleshooting an industrial sensor array from an office thousands of miles away. The core requirements for effective RemoteIoT access typically include:- Connectivity: The ability for the remote user or system to establish a communication channel with the IoT device.
- Security: Ensuring that communication is encrypted and authenticated, preventing unauthorized access or data interception. This is paramount, especially when dealing with sensitive data or critical infrastructure.
- Reliability: The connection should be stable and consistent, allowing for continuous monitoring and control without frequent disconnections.
- Low Latency: For real-time applications (e.g., controlling a robotic arm), minimal delay in communication is crucial.
- Scalability: The solution should be able to accommodate a growing number of devices and users without significant performance degradation or management overhead.
- Ease of Use: Ideally, the setup and ongoing management should be straightforward, even for those without deep networking expertise.
Cloud-Based IoT Platforms: The Easiest "Without" Solution
One of the most widely adopted and arguably the easiest ways to use RemoteIoT behind router without direct inbound connections is by leveraging cloud-based IoT platforms. Major cloud providers like Amazon Web Services (AWS) IoT Core, Google Cloud IoT Core, and Microsoft Azure IoT Hub offer comprehensive services designed specifically for connecting, managing, and interacting with IoT devices at scale. The fundamental principle behind these platforms is that your IoT devices initiate *outbound* connections to the cloud platform. Since most routers allow outbound connections by default (e.g., when you browse the internet), your devices can easily establish a connection to the cloud. Once connected, the cloud platform acts as a central broker, allowing you to send commands to your devices or receive data from them, all without needing to open any inbound ports on your router.How Cloud Platforms Bypass NAT
The magic of cloud IoT platforms in bypassing NAT lies in their publish/subscribe (pub/sub) messaging model, typically utilizing protocols like MQTT (Message Queuing Telemetry Transport). Here’s how it works:- Device Connects Outbound: Your IoT device, running a small client application, connects to the cloud IoT platform's endpoint over a standard port (e.g., 8883 for MQTT over TLS). This is an outbound connection, which is permitted by your router.
- Persistent Connection: Once connected, the device maintains a persistent, secure connection to the cloud.
- Publishing Data: When the device has data to send (e.g., sensor readings), it "publishes" this data to a specific "topic" on the cloud platform.
- Subscribing for Commands: The device also "subscribes" to other topics where it expects to receive commands or configuration updates from the cloud.
- Remote Control via Cloud: When you, as a remote user or application, want to control the device, you send a command to the cloud platform on the relevant topic. The cloud platform then forwards this command to the connected device.
Benefits and Considerations of Cloud IoT
Benefits:- Ease of Use: Once configured, remote access is seamless. You interact with a unified cloud interface or API.
- Scalability: These platforms are designed to handle millions of devices, making them ideal for large-scale deployments.
- Security: They offer robust security features, including mutual TLS authentication, data encryption in transit and at rest, and fine-grained access control.
- Rich Ecosystem: Beyond connectivity, they provide services for data analytics, machine learning, device management, and integration with other cloud services.
- Reliability: Built on highly available and fault-tolerant infrastructure.
- Cost: While free tiers exist, costs can escalate with large data volumes or many active devices.
- Vendor Lock-in: Migrating from one cloud IoT platform to another can be challenging due to proprietary APIs and services.
- Internet Dependency: Devices require a constant internet connection to communicate with the cloud.
- Learning Curve: While conceptually simple, configuring and integrating with these platforms can have a learning curve for new users.
Reverse Proxy and Tunneling Services: A Robust Alternative
Another powerful approach to enable remote access to your IoT devices without opening router ports is the use of reverse proxies and tunneling services. Unlike cloud IoT platforms that offer a full suite of services, these solutions primarily focus on creating a secure, publicly accessible endpoint that forwards traffic to your privately located device. They essentially "punch a hole" through your NAT, but in a controlled and secure manner. A reverse proxy sits in front of your IoT device (or a local server that manages your IoT devices) and intercepts incoming requests from the internet. It then forwards these requests to the appropriate device on your private network. Services like ngrok, Cloudflare Tunnel, and Tailscale (which uses a different mechanism but achieves similar NAT traversal) exemplify this.Implementing a Reverse Proxy for RemoteIoT
The general principle is similar to cloud IoT platforms: your local server or device initiates an *outbound* connection to the tunneling service's public endpoint. This creates a secure, persistent tunnel. When someone tries to access your device via the public endpoint provided by the service, the traffic travels through this tunnel to your device. Let's take ngrok as a conceptual example:- Install Client: You install the ngrok client software on a machine within your local network (e.g., a Raspberry Pi running your IoT dashboard, or a PC acting as a gateway).
- Start Tunnel: You run a command like `ngrok http 80` (assuming your IoT device's web interface is on port 80).
- Outbound Connection: The ngrok client establishes an outbound, secure connection to the ngrok cloud service.
- Public URL: ngrok provides you with a unique, publicly accessible URL (e.g., `https://abcdef12345.ngrok.io`).
- Inbound Traffic via Tunnel: When someone accesses this public URL, ngrok's cloud infrastructure receives the request and forwards it through the established tunnel to your local machine, which then routes it to your IoT device.
- NAT Traversal: Specifically designed to bypass NAT without manual port forwarding.
- Security: Traffic is typically encrypted (TLS) within the tunnel. Services like Cloudflare Tunnel add DDoS protection and WAF (Web Application Firewall) capabilities.
- Dynamic IP Friendly: Works seamlessly with dynamic public IP addresses, as the public endpoint remains constant.
- Flexibility: Can tunnel various protocols (HTTP/S, TCP, SSH).
- Simplicity: Often easier to set up than a full VPN server.
- Performance: Traffic flows through an external server, which can introduce latency depending on the service and server location.
- Reliance on Third-Party: You're dependent on the tunneling service's uptime and security.
- Cost: Free tiers often have limitations (e.g., session length, bandwidth); paid tiers are required for production use.
- Exposure: While more secure than direct port forwarding, you are still exposing a service to the internet. Proper authentication and authorization on the IoT device or local gateway are crucial.
MQTT Brokers with WebSockets: A Lightweight Approach
While MQTT is often associated with cloud IoT platforms, it can also be used with self-hosted brokers to achieve remote access, especially when combined with WebSockets. MQTT is a lightweight, publish/subscribe messaging protocol designed for constrained devices and low-bandwidth, high-latency networks. It's ideal for IoT data transmission. Typically, MQTT communication happens over TCP/IP on port 1883 (unencrypted) or 8883 (encrypted with TLS). However, if your router is blocking these ports, or you simply don't want to open them, MQTT can be tunneled over WebSockets. WebSockets provide full-duplex communication channels over a single TCP connection, often leveraging standard HTTP/S ports (80/443). Since most routers and firewalls permit outbound HTTP/S traffic, an MQTT client can connect to a public MQTT broker (or your own self-hosted broker with a public IP) using WebSockets. Here's how this method allows you to use RemoteIoT behind router without specific port forwarding for MQTT: 1. Public MQTT Broker: You need an MQTT broker accessible from the internet. This could be a cloud-hosted broker (like HiveMQ Cloud or Mosquitto running on a VPS) or a broker behind a reverse proxy (as discussed in the previous section). 2. WebSocket Support: The MQTT broker must be configured to accept WebSocket connections. Many popular brokers like Mosquitto, EMQX, and HiveMQ support this. 3. Device Connects via WebSockets: Your IoT device, instead of connecting directly to port 1883/8883, establishes a WebSocket connection to the broker's public HTTP/S port (e.g., `ws://yourbroker.com:80/mqtt` or `wss://yourbroker.com:443/mqtt`). This outbound connection is usually allowed by your router. 4. Pub/Sub Communication: Once the WebSocket connection is established, MQTT messages flow normally over this tunnel. Your device publishes data and subscribes to command topics. This approach is particularly useful for scenarios where you want fine-grained control over your messaging infrastructure or prefer not to use a full cloud IoT platform. It leverages common web ports to bypass NAT restrictions for IoT data.Security Best Practices for MQTT and WebSockets
Even when using WebSockets to bypass NAT, security remains paramount:- Always Use TLS/SSL (WSS): Encrypt your WebSocket connections using `wss://` (WebSocket Secure) to prevent eavesdropping and tampering. This typically runs over port 443.
- Client Authentication: Implement strong authentication for MQTT clients. This usually involves username/password credentials, client certificates, or integration with identity providers.
- Authorization (ACLs): Configure Access Control Lists (ACLs) on your MQTT broker to restrict which clients can publish or subscribe to which topics. Devices should only have access to the topics they absolutely need.
- Strong Passwords: For any authentication method, use strong, unique passwords.
- Broker Security: Keep your MQTT broker software updated and ensure its operating system is patched. Limit access to the broker's management interface.
Peer-to-Peer (P2P) Connections and NAT Traversal Techniques
For certain types of IoT applications, particularly those involving real-time communication like video streaming (e.g., IP cameras) or direct device-to-device control, peer-to-peer (P2P) connections can be an attractive alternative. P2P aims to establish a direct connection between two devices without an intermediary server, reducing latency and reliance on cloud infrastructure for data transfer. However, P2P behind NAT is notoriously challenging and requires specialized techniques. The primary techniques for NAT traversal in P2P scenarios are:- STUN (Session Traversal Utilities for NAT): A protocol that allows a client behind a NAT to discover its public IP address and the type of NAT it's behind. This information helps in establishing a direct connection.
- TURN (Traversal Using Relays around NAT): If STUN fails (e.g., symmetric NAT, which is very common), TURN acts as a relay server. Both peers connect to the TURN server, and the server forwards traffic between them. This is less ideal as it reintroduces a relay, but it guarantees connectivity.
- ICE (Interactive Connectivity Establishment): A framework that combines STUN and TURN, along with direct connection attempts, to find the best possible path for two peers to communicate. WebRTC (Web Real-Time Communication) heavily relies on ICE for its P2P capabilities.
- Real-time Media: IP cameras, video doorbells, and other devices streaming live audio/video where low latency is critical.
- Direct Device Control: Scenarios where a remote user needs to directly control an IoT device without an intermediary cloud processing every command.
- Reduced Bandwidth Costs: Once a direct P2P connection is established, it bypasses cloud data transfer fees.
- Complexity: Implementing P2P with NAT traversal is significantly more complex than using cloud IoT platforms or tunneling services. It requires deep networking knowledge and specialized libraries (e.g., WebRTC libraries).
- Reliability: Direct P2P connections are not always guaranteed due to diverse NAT types and firewall rules. TURN servers are necessary fallback but add latency and cost.
- Security: While direct connections can be encrypted, managing authentication and authorization in a decentralized P2P model requires careful design.
Software-Defined Networking (SDN) for IoT Connectivity
Software-Defined Networking (SDN) represents a more advanced and architectural approach to network management that can indirectly facilitate remote IoT access without traditional router configurations. While not a direct "plug-and-play" solution for individual devices, SDN principles can be applied to create highly flexible and programmable networks that abstract away underlying complexities like NAT. In an SDN environment, the network's control plane (which dictates how traffic is routed) is separated from the data plane (which forwards the actual packets). This centralized control allows network administrators to programmatically define network behavior, including how devices communicate across different network segments, even those behind NAT. How SDN helps to use RemoteIoT behind router without traditional methods: 1. Virtual Overlays: SDN can create virtual overlay networks (e.g., using VXLAN or Geneve) that span across different physical networks, including those separated by NAT. IoT devices within these overlays can communicate as if they are on the same logical network, even if they are physically behind different routers. 2. Centralized Policy: A central SDN controller can define policies for remote access, automatically configuring tunnels or routes as needed, rather than requiring manual port forwarding on each router. 3. Dynamic Connectivity: SDN can dynamically establish connections or tunnels between IoT devices and remote users/applications based on predefined policies or on-demand requests, adapting to changing network conditions or device locations. 4. Enhanced Security: By centralizing control, SDN enables more granular security policies and micro-segmentation, isolating IoT devices and controlling their communication pathways more effectively than traditional firewall rules. Applicability: SDN is typically implemented in larger, more complex IoT deployments, such as smart cities, industrial IoT (IIoT), or large enterprise networks where hundreds or thousands of devices need to be managed across diverse geographical locations and network infrastructures. It's less of a solution for a single home IoT setup and more of an architectural paradigm for robust, scalable IoT networks. Considerations:- Complexity and Cost: Implementing SDN requires significant expertise, specialized hardware/software, and considerable investment.
- Overkill for Small Deployments: For a few IoT devices, SDN is an overly complex solution.
- Learning Curve: Understanding and managing an SDN environment requires specialized networking skills.
Choosing the Right Method for Your RemoteIoT Deployment
Selecting the optimal method to use RemoteIoT behind router without port forwarding depends heavily on your specific needs, the scale of your deployment, your technical expertise, and your budget. Here's a quick guide to help you decide:- For Simplicity and Scalability (Most Common Use Case): Cloud-Based IoT Platforms
- Best for: Most general IoT applications, large-scale deployments, data collection and analytics, users who prefer managed services, those who want to avoid network configuration entirely.
- Examples: AWS IoT Core, Google Cloud IoT Core, Azure IoT Hub.
- Pros: Easiest to set up for remote access, highly scalable, robust security, rich feature sets.
- Cons: Can be costly at scale, vendor lock-in, requires internet connection.
- For Direct Access to Web Interfaces or Services: Reverse Proxy/Tunneling Services
- Best for: Exposing a local web server, SSH access, or a specific application running on your IoT gateway/device, testing, and development.
- Examples: ngrok, Cloudflare Tunnel, Tailscale.
- Pros: Simple to configure, works well with dynamic IPs, adds a layer of security over direct port forwarding.
- Cons: Dependent on third-party service, potential latency, free tiers have limitations.
- For Custom Messaging and Controlled Infrastructure: MQTT with WebSockets
- Best for: Developers who want more control over their messaging infrastructure, lightweight data exchange, avoiding full cloud IoT platforms, using standard web ports.
- Examples: Mosquitto, EMQX (self-hosted or cloud-hosted with WebSocket support).
- Pros: Efficient for IoT messaging, uses common ports, flexible.
- Cons: Requires setting up and managing a broker, security needs careful configuration.
- For Real-time Media and Direct Device-to-Device Communication: P2P with NAT Traversal
- Best for: IP cameras, video streaming, direct low-latency control, reducing cloud bandwidth.
- Examples: WebRTC implementations.
- Pros: Lowest latency for direct connections, reduces cloud reliance for data transfer.
- Cons: Highly complex to implement, reliability can vary, requires signaling server.
- For Large-Scale, Enterprise-Grade Networks: Software-Defined Networking (SDN)
- Best for: Industrial IoT, smart city deployments, large enterprises with complex network architectures, highly dynamic and programmable network needs.
- Examples: OpenFlow, Cisco ACI, VMware NSX.
- Pros: Ultimate network flexibility and control, enhanced security, highly scalable.
- Cons: Extremely complex, high cost, significant expertise required.
Conclusion
Navigating the complexities of network address translation to achieve remote access for your Internet of Things devices can seem daunting, but as we've explored, numerous sophisticated and secure alternatives exist beyond the traditional, often risky, method of port forwarding. From the comprehensive offerings of cloud-based IoT platforms to the focused tunneling capabilities of reverse proxies and the elegant simplicity of MQTT over WebSockets, the options available empower you to effectively use RemoteIoT behind router without compromising on security or convenience. Whether you're managing a handful of smart home devices or orchestrating a vast industrial IoT deployment, understanding these methodsRelated Resources:

Detail Author:
- Name : Fiona Goodwin
- Username : fquigley
- Email : mae.anderson@kulas.com
- Birthdate : 1983-04-11
- Address : 68026 Mitchell Stream New Garnet, OH 18371
- Phone : (520) 393-7687
- Company : Zemlak and Sons
- Job : Barber
- Bio : Voluptatem corporis adipisci iure similique. Qui nemo dolor odit possimus laboriosam. Numquam voluptas in doloremque ut.
Socials
instagram:
- url : https://instagram.com/berta6875
- username : berta6875
- bio : Unde deleniti id hic et accusamus et. Quia quae eveniet aut accusamus error.
- followers : 6095
- following : 1900
linkedin:
- url : https://linkedin.com/in/berta.watsica
- username : berta.watsica
- bio : Aut dolores aut velit vel.
- followers : 3789
- following : 2428