In the rapidly expanding world of connected devices, securing your remote IoT platform with SSH keys is no longer an option but a fundamental necessity. As the Internet of Things (IoT) continues its explosive growth, permeating every aspect of our lives from smart homes to industrial automation, the sheer volume of deployed devices presents an unprecedented attack surface for cybercriminals. Ensuring the integrity, confidentiality, and availability of these devices and the data they handle is paramount.
The stakes in IoT security are incredibly high. A compromised device can lead to data breaches, operational disruptions, and even physical harm. Traditional password-based authentication, while familiar, often falls short in the complex and distributed IoT landscape. This is where the robust security of SSH (Secure Shell) keys, managed effectively through a dedicated remote IoT platform, steps in as a game-changer, offering a superior method for authenticating and securing remote access to your invaluable IoT assets.
Table of Contents
- Understanding the IoT Security Landscape
- The Core of Secure Remote Access: SSH Keys Explained
- Why a Dedicated Remote IoT Platform is Crucial for SSH Key Management
- Implementing SSH Keys on Your Remote IoT Platform: A Step-by-Step Guide
- Advanced Security Practices with Remote IoT Platform SSH Keys
- Overcoming Common Challenges in Remote IoT Security
- The E-E-A-T and YMYL Implications of Robust IoT Security
- Future Trends in Remote IoT Security and SSH Key Evolution
Understanding the IoT Security Landscape
The Internet of Things has transformed industries and daily life, connecting billions of devices, from simple sensors to complex industrial machinery. This connectivity, while enabling unprecedented efficiency and innovation, simultaneously introduces significant security vulnerabilities. Unlike traditional IT infrastructure, IoT devices often operate with limited processing power, memory, and battery life, making it challenging to implement robust security protocols. Many are deployed in remote, unattended locations, making physical access for maintenance or security updates impractical. Furthermore, the sheer scale of IoT deployments means that a single vulnerability can be replicated across millions of devices, creating a massive target for cyberattacks. The consequences of a breach can range from data theft and privacy violations to critical infrastructure disruption and even physical harm. This complex and distributed nature of IoT necessitates a security approach that is both scalable and resilient, precisely where a robust **remote IoT platform SSH key** management system becomes indispensable.The Core of Secure Remote Access: SSH Keys Explained
SSH, or Secure Shell, is a cryptographic network protocol that enables secure remote access to computers and devices over an unsecured network. It provides a secure channel over an unsecure network by using a client-server architecture, connecting an SSH client application with an SSH server. While SSH is commonly associated with accessing Linux servers, its principles are perfectly suited for securing remote access to IoT devices. The real power of SSH for IoT security lies in its use of public-key cryptography for authentication, moving beyond the inherent weaknesses of passwords. Instead of a single, guessable password, SSH key authentication relies on a pair of cryptographic keys: a public key and a private key. The public key is stored on the remote IoT device, while the private key remains securely on the user's local machine. When a connection is attempted, the device challenges the user, who then uses their private key to prove their identity without ever transmitting the private key itself. This challenge-response mechanism makes SSH keys incredibly resistant to brute-force attacks and credential stuffing, which are common tactics against password-protected systems.Password vs. SSH Key Authentication: A Security Showdown
The contrast between password-based authentication and SSH key authentication is stark, particularly in high-stakes environments like IoT. Passwords, by their nature, are susceptible to a myriad of attacks. They can be guessed, brute-forced, phished, or stolen from compromised databases. Users often choose weak, easily memorable passwords or reuse them across multiple services, dramatically increasing their vulnerability. Even strong, unique passwords can be compromised if the system they are protecting has other weaknesses. In contrast, SSH keys offer a fundamentally more secure approach. They are cryptographically generated, making them virtually impossible to guess or brute-force. A typical RSA SSH key pair, for example, uses a 2048-bit or 4096-bit encryption, which would take an astronomical amount of computational power to crack. Furthermore, the private key never leaves the client's machine, meaning it cannot be intercepted during transmission. While a password can be compromised if stolen from a server or intercepted, an SSH private key, when properly secured with a passphrase, provides an additional layer of protection even if the file itself is accessed. This inherent strength makes a **remote IoT platform SSH key** system a vastly superior choice for securing distributed device fleets.Why a Dedicated Remote IoT Platform is Crucial for SSH Key Management
Managing SSH keys manually across a large fleet of IoT devices is a logistical nightmare and a significant security risk. Imagine having hundreds or thousands of devices, each requiring a unique public key, and then needing to rotate or revoke those keys periodically. This manual process is prone to errors, incredibly time-consuming, and simply not scalable. A dedicated remote IoT platform solves these challenges by centralizing the entire lifecycle of SSH key management. Such a platform can automate the generation of unique key pairs for each device, securely distribute the public keys to the respective devices during provisioning, and crucially, facilitate automated key rotation and revocation. This automation ensures that security best practices are consistently applied across the entire fleet without human intervention. Furthermore, a robust platform provides an audit trail of all key-related activities, enhancing accountability and compliance. It allows for granular access control, ensuring that only authorized personnel or systems can access specific devices, thereby significantly reducing the attack surface. By leveraging a specialized platform, organizations can implement a secure and efficient **remote IoT platform SSH key** strategy that scales with their growth and adapts to evolving threat landscapes.Implementing SSH Keys on Your Remote IoT Platform: A Step-by-Step Guide
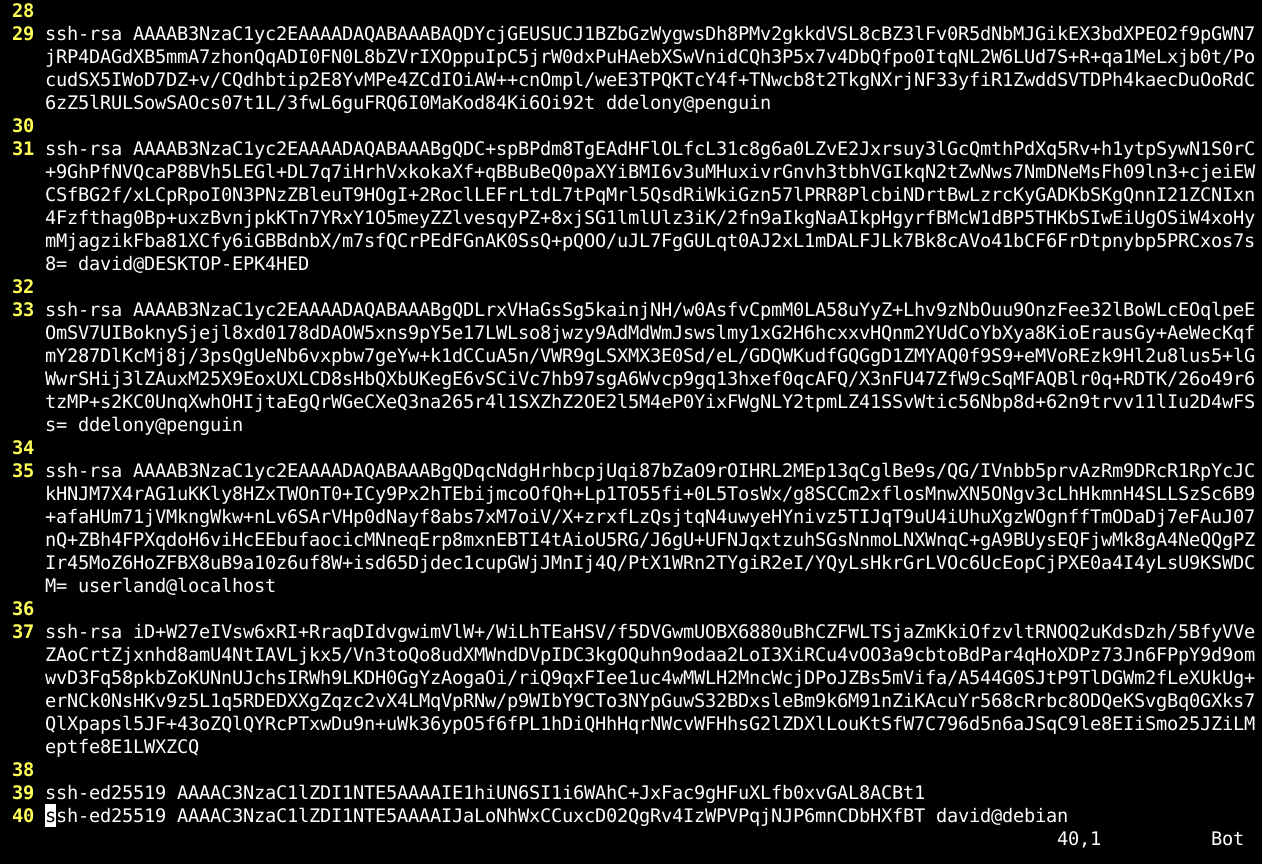
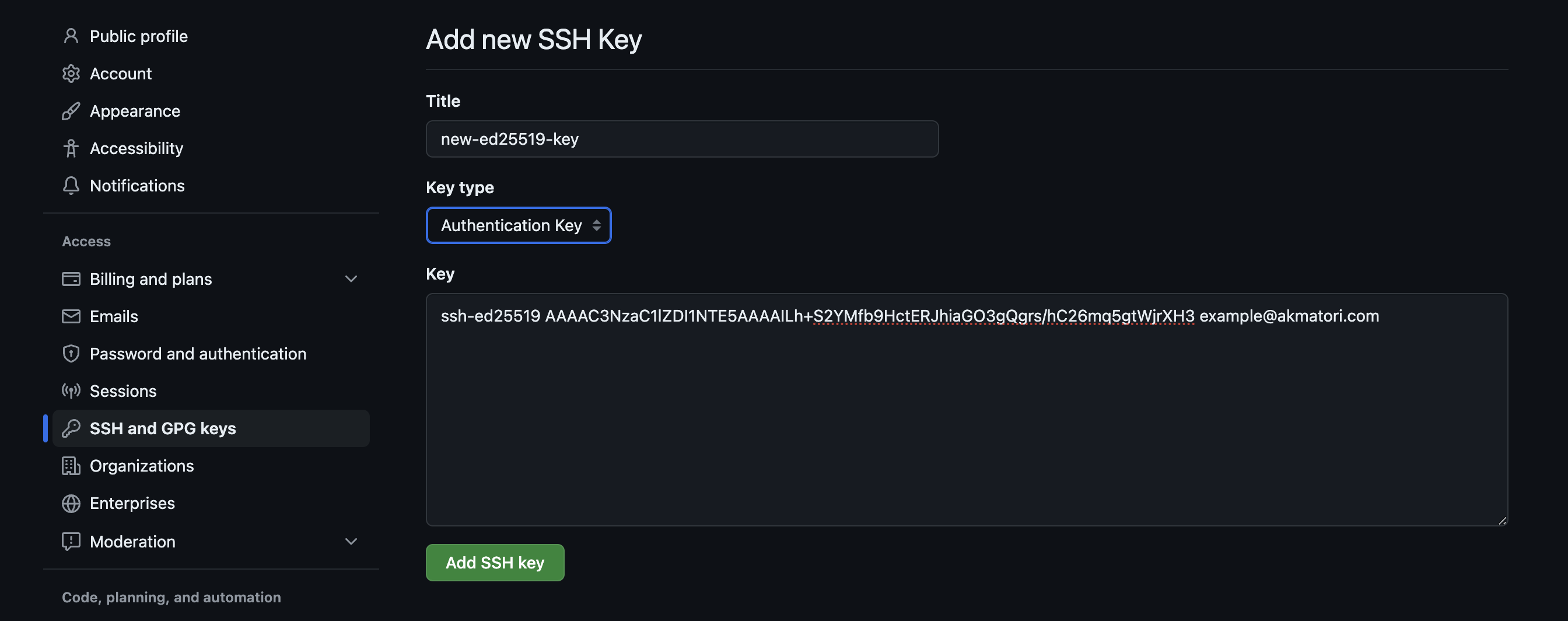
Implementing SSH keys effectively within a remote IoT platform involves several critical steps to ensure seamless and secure operation. The process typically begins with generating a secure SSH key pair. This is usually done on the client machine (e.g., a developer's workstation or a central management server) using tools like `ssh-keygen`. The output will be two files: a private key (e.g., `id_rsa`) and a public key (e.g., `id_rsa.pub`). The next crucial step is securely distributing the public key to each target IoT device. This is often automated by the remote IoT platform during the device provisioning phase. When a new device is onboarded, the platform pushes the unique public key to the device's authorized_keys file (typically located in `~/.ssh/authorized_keys`). The private key, however, must remain strictly confidential and secured on the client side, ideally protected by a strong passphrase. Once the public keys are deployed, the remote IoT platform is configured to recognize and manage these keys. This involves setting up access policies, associating specific keys with device groups or individual devices, and defining user permissions. Finally, connecting securely becomes straightforward: the user or automated system attempts to connect to the IoT device via SSH. The device, having the public key, challenges the client. The client responds by proving possession of the corresponding private key, and if the cryptographic handshake is successful, a secure, encrypted tunnel is established. This systematic approach ensures that every connection to your IoT devices via the **remote IoT platform SSH key** system is authenticated and encrypted, providing a strong defense against unauthorized access.Advanced Security Practices with Remote IoT Platform SSH Keys
While basic SSH key implementation provides a strong foundation, advanced practices significantly enhance the security posture of your IoT fleet. One critical practice is implementing strict key rotation policies. Just as passwords should be changed periodically, SSH keys should also be rotated to minimize the window of opportunity for a compromised key to be exploited. A robust remote IoT platform facilitates automated key rotation, generating new keys, distributing them, and revoking old ones on a predefined schedule. Another layer of security involves protecting the private keys with strong passphrases. Even if a private key file is stolen, the passphrase acts as a second factor, preventing its immediate use. Furthermore, integrating multi-factor authentication (MFA) with your SSH key access adds an extra layer of verification, requiring something the user knows (passphrase), something they have (private key), and potentially something they are (biometrics) or something they have access to (authenticator app code). Finally, adhering to the principle of least privilege is paramount: ensure that each user or automated process only has the minimum necessary access rights to perform its function. This limits the potential damage if a key or account is compromised.The Importance of Key Rotation and Revocation
Key rotation and revocation are cornerstones of a proactive cybersecurity strategy, especially for distributed systems like IoT. Key rotation involves periodically replacing existing SSH key pairs with new ones. This practice significantly reduces the risk associated with a long-lived key being compromised without detection. If a key is stolen or exposed, its limited lifespan means the attacker's window of opportunity is constrained. Automated key rotation, a feature often provided by advanced remote IoT platforms, ensures that this crucial security measure is consistently applied across all devices without manual oversight, preventing human error or oversight. Revocation, on the other hand, is the immediate invalidation of a key that is known or suspected to be compromised. This is a critical incident response capability. If an employee leaves, a device is lost, or a breach is detected, the ability to instantly revoke the associated SSH keys prevents further unauthorized access. Without a centralized **remote IoT platform SSH key** management system, performing these actions at scale would be virtually impossible, leaving the IoT infrastructure exposed to significant and persistent threats.Overcoming Common Challenges in Remote IoT Security
Securing IoT devices presents unique challenges that go beyond traditional IT security. Device heterogeneity is a major hurdle; IoT deployments often involve a vast array of devices from different manufacturers, running various operating systems and firmware versions, each with its own quirks and vulnerabilities. This diversity makes a "one-size-fits-all" security solution difficult to implement. Network constraints are another significant factor; many IoT devices operate on low-power, low-bandwidth networks, limiting the complexity of cryptographic operations they can perform or the size of security updates they can receive. Ensuring firmware integrity is also critical, as compromised firmware can turn a device into a botnet member or a backdoor into the network. While SSH keys secure the access channel, the underlying device itself must be trustworthy. A comprehensive **remote IoT platform SSH key** strategy must therefore be complemented by other security layers that address these inherent IoT challenges, ensuring a holistic defense.Securing the Device Edge: Beyond SSH Keys
While SSH keys are indispensable for securing remote access to IoT devices, a truly robust IoT security posture extends far beyond just the access mechanism. Securing the device edge, where the physical world meets the digital, requires a multi-layered approach. This includes implementing secure boot mechanisms, which ensure that only trusted, signed firmware can run on a device, preventing tampering from the moment it powers on. Hardware roots of trust (HRoT), often in the form of secure elements or Trusted Platform Modules (TPMs), provide a tamper-resistant foundation for cryptographic operations and secure storage of keys and certificates directly on the device. Regular, over-the-air (OTA) firmware updates are crucial for patching vulnerabilities and deploying security enhancements, even in remote locations. Furthermore, network segmentation and intrusion detection systems specific to IoT traffic can help identify and isolate suspicious activities. By combining strong access control via a **remote IoT platform SSH key** system with these device-level and network-level security measures, organizations can build a resilient and comprehensive defense for their valuable IoT assets.The E-E-A-T and YMYL Implications of Robust IoT Security
In today's digital economy, the principles of Expertise, Authoritativeness, and Trustworthiness (E-E-A-T) are paramount, especially for topics touching upon Your Money or Your Life (YMYL) areas like cybersecurity. Robust IoT security, underpinned by effective **remote IoT platform SSH key** management, directly impacts these critical aspects. Organizations that prioritize and implement strong security measures demonstrate their expertise in managing complex technological infrastructures and their commitment to protecting sensitive data. This builds authoritativeness within their industry and fosters trust among customers, partners, and stakeholders. For instance, a smart home company ensuring the utmost security of its devices through advanced SSH key management builds consumer confidence that their personal data and home environment are safe. The YMYL implications are particularly acute in IoT. A security breach in an industrial IoT system could lead to catastrophic operational failures, significant financial losses, and even threats to human life (e.g., in critical infrastructure, healthcare, or autonomous vehicles). Similarly, compromised personal IoT devices can expose highly sensitive personal information, leading to identity theft or privacy violations, directly impacting an individual's financial well-being and life quality. Therefore, investing in and expertly managing IoT security, particularly through proven methods like SSH key authentication on a dedicated platform, is not merely a technical decision but a fundamental business imperative that safeguards assets, reputations, and human lives.Building Trust in the Connected World
In an increasingly interconnected world, trust is the most valuable currency. For businesses operating in the IoT space, establishing and maintaining trust is directly tied to their ability to secure their devices and the data they process. When a company demonstrates a clear commitment to security through the implementation of best practices, such as leveraging a **remote IoT platform SSH key** system, it signals to customers, investors, and regulators that their data and operations are handled with the utmost care. This proactive approach to cybersecurity fosters consumer confidence, which is crucial for market adoption and brand loyalty. Conversely, a single, significant security incident can erode trust overnight, leading to severe reputational damage, legal repercussions, and financial penalties. By prioritizing robust security, organizations not only protect themselves from threats but also contribute to a safer, more reliable digital ecosystem, reinforcing their credibility and ensuring long-term success in the competitive IoT landscape.Future Trends in Remote IoT Security and SSH Key Evolution
The landscape of IoT security is constantly evolving, driven by new threats and technological advancements. The future of **remote IoT platform SSH key** management will likely see several key trends. Post-quantum cryptography (PQC) is gaining traction, as researchers work to develop cryptographic algorithms that can withstand attacks from future quantum computers. While not an immediate threat, preparing for PQC will involve updating SSH key algorithms to quantum-resistant standards. The adoption of zero-trust architectures will become more prevalent in IoT, meaning no device, user, or application is inherently trusted, regardless of its location. Every access attempt will be verified, minimizing the attack surface. Furthermore, the integration of Artificial Intelligence (AI) and Machine Learning (ML) for anomaly detection in IoT traffic will enhance the ability to identify and respond to unusual SSH connection attempts or device behavior in real-time, moving beyond traditional signature-based detection. These trends signify a continuous push towards more resilient, adaptive, and intelligent security solutions to protect the ever-expanding IoT frontier.In conclusion, the security of your IoT ecosystem hinges significantly on robust access control, and for this, the **remote IoT platform SSH key** system stands as an unparalleled solution. By leveraging public-key cryptography and centralizing key management through a dedicated platform, organizations can overcome the inherent vulnerabilities of password-based authentication and the complexities of managing a vast device fleet. This strategic approach not only fortifies your defenses against cyber threats but also underpins your adherence to critical E-E-A-T and YMYL principles, building invaluable trust with your stakeholders.
- Maegan Hall Twitter
- Halle Jonah Together Blind Item Twitter
- Ebony X
- Lildedjanet Leaked Twitter
- Goddesshwan Onlyfans
As IoT continues to expand, the importance of proactive, scalable, and intelligent security measures will only grow. Embracing advanced practices like key rotation, multi-factor authentication, and exploring future trends such as post-quantum cryptography will be essential for maintaining a secure and resilient IoT infrastructure. Don't leave your connected future to chance; secure it with the power of SSH keys on a purpose-built remote IoT platform. What are your biggest challenges in securing your IoT devices? Share your thoughts and experiences in the comments below, or explore our other articles on cutting-edge cybersecurity solutions for connected technologies.
Related Resources:

Detail Author:
- Name : Martine Zulauf Sr.
- Username : littel.juston
- Email : rohan.faye@gmail.com
- Birthdate : 1995-02-15
- Address : 299 Eloisa Lake Apt. 705 Cassieshire, HI 93218
- Phone : 1-920-392-1903
- Company : Kozey, Glover and Kassulke
- Job : Computer Systems Analyst
- Bio : Nihil voluptatem non est ex voluptatum. Explicabo ex ea et quam itaque optio. Tempora quod omnis sit pariatur tempore.
Socials
twitter:
- url : https://twitter.com/maida1136
- username : maida1136
- bio : Aut ullam commodi cum. Impedit distinctio et voluptatem. Quam officia eligendi optio a quia sapiente.
- followers : 2533
- following : 2054
facebook:
- url : https://facebook.com/maida.carroll
- username : maida.carroll
- bio : Consequatur in rem possimus dolorum sed.
- followers : 746
- following : 85
instagram:
- url : https://instagram.com/maida_carroll
- username : maida_carroll
- bio : Voluptatibus vero tempore occaecati perferendis. Quo ipsam modi culpa enim corrupti.
- followers : 2457
- following : 625
tiktok:
- url : https://tiktok.com/@mcarroll
- username : mcarroll
- bio : Sunt quasi aut accusamus voluptatem tempora ut qui.
- followers : 5345
- following : 583
linkedin:
- url : https://linkedin.com/in/mcarroll
- username : mcarroll
- bio : Dolorem sed unde quidem.
- followers : 3467
- following : 1881