The explosion of Internet of Things (IoT) devices presents immense opportunities, but also significant challenges, particularly when it comes to securing and managing these devices remotely. Building a robust and secure network for your IoT deployment is paramount, and leveraging the power of an AWS Virtual Private Cloud (VPC) for your remote IoT infrastructure is a strategic move that offers unparalleled control, security, and scalability.
In today's interconnected world, IoT devices are everywhere, from smart homes and industrial sensors to healthcare monitors and smart city infrastructure. These devices often operate in remote, unmanaged environments, making their secure and reliable connection to cloud services a complex endeavor. An AWS VPC provides a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. This level of isolation and control is precisely what's needed to manage the unique demands of a remote IoT VPC network AWS, ensuring data integrity, device security, and operational efficiency.
Table of Contents
- Understanding the Core Challenge of Remote IoT Connectivity
- Why AWS VPC is the Foundation for Your Remote IoT Network
- Designing Your AWS VPC for Remote IoT: A Step-by-Step Guide
- Secure Connectivity for Remote IoT Devices within AWS VPC
- Advanced Security Measures for Your Remote IoT VPC
- Data Ingestion and Processing Architectures
- Monitoring, Management, and Scalability for Remote IoT
- Best Practices and Common Pitfalls to Avoid
- Conclusion
Understanding the Core Challenge of Remote IoT Connectivity
The Internet of Things, by its very nature, involves devices distributed across vast geographical areas, often in environments with unreliable power, intermittent network access, or even hostile conditions. Connecting these devices securely and reliably to a central cloud platform presents a unique set of challenges that differ significantly from traditional enterprise networking. Consider the sheer scale: an IoT deployment might involve thousands, even millions, of devices. Each device needs a secure identity, a way to authenticate, and a mechanism to transmit data without compromise. Latency can be a critical factor for real-time applications, while bandwidth limitations are common in remote areas. Furthermore, the diversity of IoT devices – from tiny, low-power sensors to powerful edge gateways – means a one-size-fits-all networking approach simply won't work. Security, above all, is paramount. A compromised IoT device can become an entry point for cyberattacks, leading to data breaches, operational disruptions, or even physical harm in critical infrastructure scenarios. Without a robust, isolated, and highly configurable network backbone, managing these challenges becomes an insurmountable task. This is where the strategic implementation of a remote IoT VPC network AWS truly shines.Why AWS VPC is the Foundation for Your Remote IoT Network
AWS Virtual Private Cloud (VPC) offers a fundamental building block for any secure and scalable cloud infrastructure, and it's particularly well-suited for the unique demands of IoT. A VPC allows you to provision a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. This means you have complete control over your virtual networking environment, including your own IP address range, subnets, route tables, and network gateways. The benefits of using an AWS VPC for your remote IoT deployment are manifold:- Isolation and Security: Your IoT backend services and data processing pipelines are isolated from other AWS customers and the public internet, reducing the attack surface. You control all inbound and outbound traffic.
- Granular Control: Define your own IP address spaces, create subnets for different tiers of your application (e.g., IoT Core endpoints, backend processing, databases), and configure routing tables. This level of control is essential for segmenting IoT traffic and applying specific security policies.
- Scalability: AWS VPCs are designed to scale. As your IoT fleet grows, you can easily add more subnets, expand IP ranges, and provision additional resources without re-architecting your entire network.
- Integration with AWS Services: VPC seamlessly integrates with a wide array of AWS services crucial for IoT, such as AWS IoT Core, Lambda, Kinesis, S3, and various compute options (EC2, ECS, EKS). This allows you to build end-to-end IoT solutions within a secure and managed environment.
- Hybrid Connectivity: For scenarios where IoT data needs to flow between your AWS cloud environment and on-premises data centers, VPC provides robust options like AWS Direct Connect and VPN connections.
Designing Your AWS VPC for Remote IoT: A Step-by-Step Guide
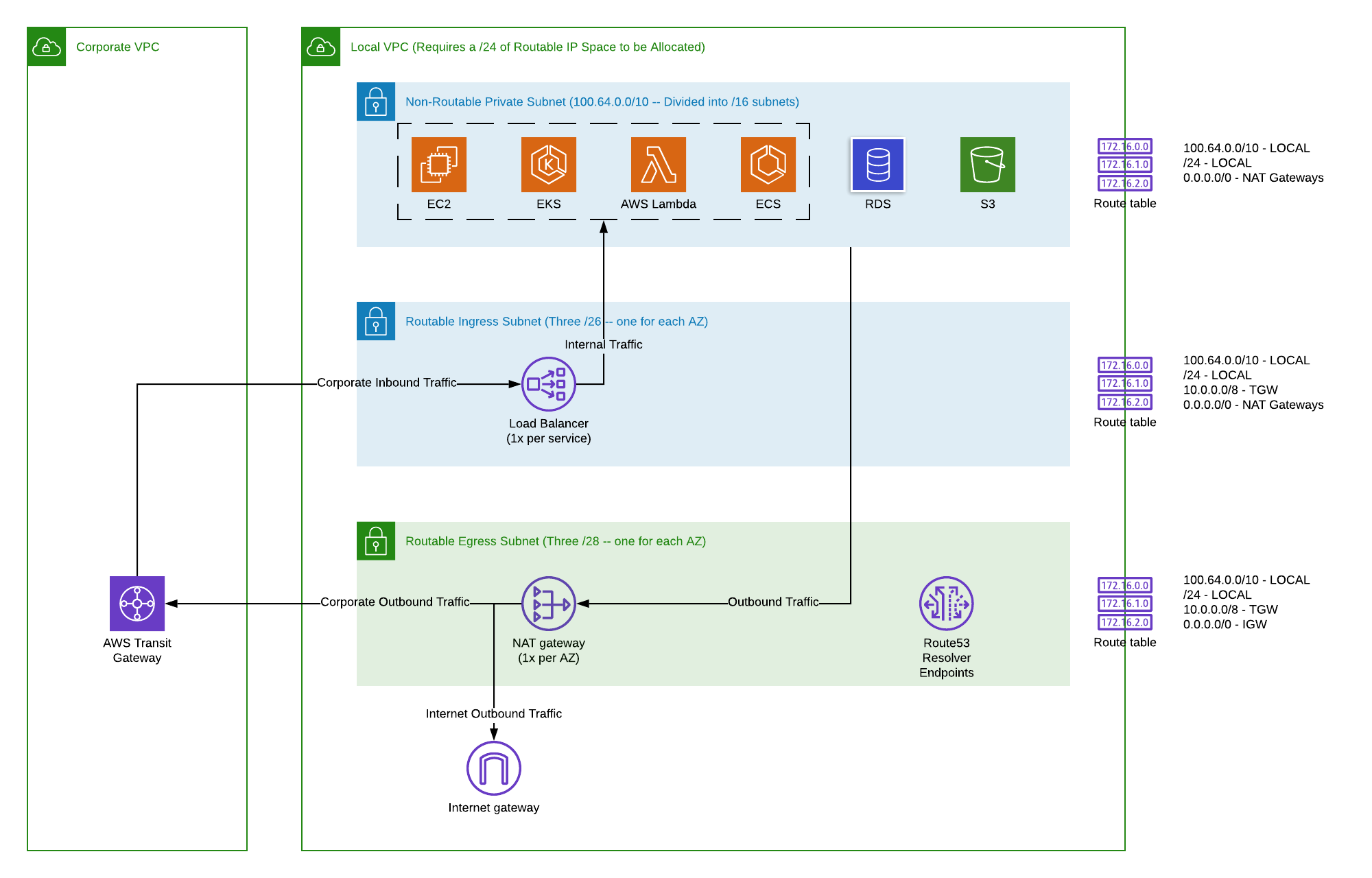
A thoughtful design is critical when building your remote IoT VPC network AWS. This isn't just about throwing resources into a cloud; it's about creating an optimized, secure, and scalable environment that supports the unique demands of IoT.VPC Sizing and IP Addressing Strategy
The first step is to define your VPC's CIDR block. This is a crucial decision as it determines the total number of private IP addresses available within your VPC. While you can add secondary CIDR blocks later, it's best to plan for future growth from the outset. For most IoT deployments, a `/16` CIDR block (e.g., `10.0.0.0/16`) provides over 65,000 private IP addresses, offering ample room for expansion. Once your VPC CIDR is set, you'll divide it into subnets. Subnets allow you to segment your network within the VPC, isolating resources and applying different security policies. A common best practice is to create a mix of public and private subnets:- Public Subnets: These subnets have a route to an Internet Gateway (IGW) and are typically used for resources that need to be directly accessible from the internet, such as load balancers or bastion hosts. For IoT, this might include specific IoT Core endpoints if direct device connectivity is required over the public internet, though private endpoints are often preferred for security.
- Private Subnets: These subnets do not have a direct route to the Internet Gateway. Resources in private subnets can only access the internet via a NAT Gateway (for outbound connections like software updates) or through a VPC endpoint. This is where the majority of your IoT backend services, databases, and sensitive data processing will reside, providing a higher level of security.
Subnetting for IoT Device Segregation
Effective subnetting is key to a secure IoT architecture. You should segregate your network based on function and security posture. For a remote IoT VPC network AWS, consider these subnet types:- IoT Core Endpoints Subnets: If you're using VPC endpoints for AWS IoT Core (highly recommended for enhanced security), these endpoints will reside in private subnets. This ensures that your devices communicate with IoT Core over the AWS private network, bypassing the public internet where possible.
- Application Backend Subnets: These private subnets host your application servers, microservices (e.g., running on EC2, ECS, or EKS), and processing logic that interacts with IoT data.
- Database Subnets: Dedicated private subnets for your databases (e.g., Amazon RDS, DynamoDB, Amazon Timestream) ensure that your data stores are isolated and not directly exposed.
- Management Subnets: A smaller, potentially public or private subnet for bastion hosts or VPN endpoints used for administrative access to your VPC resources.
Implementing Network Access Control Lists (NACLs) and Security Groups
AWS provides two powerful tools for controlling traffic within your VPC: Network Access Control Lists (NACLs) and Security Groups. Understanding their differences and using them effectively is crucial for a secure remote IoT VPC network AWS.- Network Access Control Lists (NACLs): These act as stateless firewalls for your subnets. They evaluate rules in order, from lowest to highest, and apply to all instances within a subnet. NACLs can allow or deny both inbound and outbound traffic. Because they are stateless, if you allow inbound traffic, you must also explicitly allow the corresponding outbound response. They are excellent for broad, coarse-grained filtering at the subnet level. For example, you might use a NACL to deny all traffic from known malicious IP ranges to your IoT backend subnets.
- Security Groups: These act as stateful firewalls for individual instances (or network interfaces). They evaluate all rules before deciding to allow traffic. Because they are stateful, if you allow inbound traffic, the outbound response is automatically allowed. Security groups are ideal for fine-grained control over specific instances or groups of instances. For example, you would use a security group to allow only MQTT traffic on port 8883 from your IoT Core endpoint to your application backend servers, or to allow only SSH access from your bastion host to your EC2 instances.
Secure Connectivity for Remote IoT Devices within AWS VPC
Once your VPC is designed, the next critical step is establishing secure and reliable communication channels for your remote IoT devices to interact with your cloud infrastructure. This involves leveraging AWS IoT Core and potentially hybrid cloud connectivity options.Leveraging AWS IoT Core Endpoints
AWS IoT Core is the managed cloud service that allows connected devices to easily and securely interact with cloud applications and other devices. It provides various endpoints for device connectivity:- Device Gateway Endpoint (MQTT, HTTPS, WSS): This is the primary entry point for devices. Devices can connect using MQTT (Message Queuing Telemetry Transport), a lightweight messaging protocol ideal for IoT, or HTTPS/WSS (WebSockets Secure) for web-based applications or devices that prefer HTTP. For enhanced security and lower latency, especially for devices with consistent internet access, consider using VPC endpoints for AWS IoT Core. These endpoints allow devices to connect to IoT Core over a private connection from your VPC, bypassing the public internet. This is a game-changer for a secure remote IoT VPC network AWS.
- Data Plane Endpoint: Used for publishing and subscribing to MQTT topics.
- Credential Provider Endpoint: For devices to obtain temporary AWS credentials for direct access to other AWS services (e.g., S3 for large file uploads).
VPN and Direct Connect for On-Premises Integration
Many IoT solutions involve a hybrid architecture, where devices or data might originate from or need to interact with on-premises systems. AWS offers two primary services to securely bridge your AWS VPC with your corporate data centers:- AWS Site-to-Site VPN: This establishes an encrypted tunnel over the public internet between your on-premises network and your AWS VPC. It's a cost-effective and relatively quick way to set up secure connectivity. VPN is suitable for many use cases, especially for initial deployments or when dedicated bandwidth is not strictly required.
- AWS Direct Connect: This provides a dedicated, private network connection from your premises to AWS. Direct Connect bypasses the public internet entirely, offering higher bandwidth, lower latency, and a more consistent network experience compared to VPN. It's ideal for mission-critical IoT applications that require high throughput, predictable performance, and maximum security, such as industrial IoT or large-scale data transfer.
Advanced Security Measures for Your Remote IoT VPC
While VPCs provide foundational network isolation, a truly secure remote IoT VPC network AWS requires a multi-layered security approach. Beyond NACLs and Security Groups, consider these advanced measures:- IAM Policies for IoT Core and Other Services: Implement granular Identity and Access Management (IAM) policies to control which users and roles can interact with your IoT Core resources (e.g., register devices, publish messages, update shadows) and other AWS services within your VPC. Follow the principle of least privilege – grant only the permissions necessary for a task.
- Certificate-Based Authentication for Devices: For device authentication, always prefer X.509 certificates over username/password. Each device should have a unique certificate, and these certificates should be securely provisioned and managed. AWS IoT Core's Just-in-Time Registration (JITR) or Just-in-Time Provisioning (JITP) can automate this process.
- VPC Flow Logs: Enable VPC Flow Logs to capture information about the IP traffic going to and from network interfaces in your VPC. These logs can be published to Amazon CloudWatch Logs or Amazon S3, providing invaluable data for network monitoring, security analysis, and troubleshooting. Analyzing flow logs can help detect anomalous traffic patterns that might indicate a security breach.
- AWS WAF and Shield: For public-facing endpoints (if any) or web applications interacting with your IoT data, deploy AWS WAF (Web Application Firewall) to protect against common web exploits and bots. AWS Shield provides managed Distributed Denial of Service (DDoS) protection.
- AWS PrivateLink for Service Endpoints: As mentioned, using VPC endpoints (powered by PrivateLink) for AWS IoT Core ensures that traffic between your devices (if they are within a corporate network connected to your VPC) and IoT Core stays entirely within the AWS network, never traversing the public internet. Extend this to other AWS services your IoT solution uses, such as S3, DynamoDB, or Kinesis, for maximum security.
- Regular Security Audits and Penetration Testing: Periodically review your VPC configuration, security groups, NACLs, and IAM policies. Conduct penetration testing on your IoT solution to identify and remediate vulnerabilities before they can be exploited.
Data Ingestion and Processing Architectures
A secure remote IoT VPC network AWS is only half the battle; the other half is efficiently ingesting, processing, and storing the vast amounts of data generated by your devices. AWS offers a rich ecosystem of services that integrate seamlessly within your VPC to handle this data pipeline:- AWS IoT Core Rules Engine: After devices connect and publish data to AWS IoT Core, the Rules Engine acts as a powerful routing and processing hub. It allows you to define rules that transform, filter, and route messages to other AWS services. For example, a rule can send sensor readings directly to:
- Amazon Kinesis (Data Streams or Firehose): For real-time streaming data ingestion and delivery to analytics services or data lakes. Kinesis is ideal for high-throughput, low-latency data pipelines.
- AWS Lambda: To trigger serverless functions for immediate processing, data validation, or custom logic based on incoming messages.
- Amazon S3: For cost-effective, highly durable storage of raw IoT data (e.g., for data lakes or archival purposes).
- Amazon DynamoDB or Amazon Timestream: For storing device state, metadata, or time-series data, respectively. These databases are optimized for high-volume, low-latency access.
- VPC Endpoints for Data Services: To maintain security and keep data traffic within the AWS network, ensure that your Lambda functions, EC2 instances, or other compute resources within your VPC access services like S3, DynamoDB, or Kinesis via VPC endpoints (PrivateLink). This prevents data from traversing the public internet, even within AWS.
- Data Lakes and Analytics: Once data is in S3 or other storage, you can leverage services like Amazon Athena (for querying S3 data), Amazon Redshift (for data warehousing), or Amazon QuickSight (for business intelligence and visualization) to derive insights from your IoT data. All these services can be configured to interact securely within or across VPCs.
Monitoring, Management, and Scalability for Remote IoT
Deploying a remote IoT VPC network AWS is an ongoing process that requires continuous monitoring, efficient management, and the ability to scale seamlessly.- Amazon CloudWatch: This is your primary tool for monitoring. Use CloudWatch to collect and track metrics, collect and monitor log files (from VPC Flow Logs, Lambda, EC2, etc.), and set alarms. For IoT, monitor device connectivity, message rates, rule executions, and service health. Create dashboards to visualize key performance indicators (KPIs) and set up alarms to notify you of anomalies or potential issues.
- AWS IoT Device Management: This suite of services helps you onboard, organize, monitor, and remotely manage your IoT devices at scale. Key features include:
- Device Registry: To register and organize your devices.
- Device Shadow: To store and retrieve the current state of your devices.
- Jobs: To remotely send commands to devices, deploy software updates, or perform reboots.
- Fleet Indexing: To search and aggregate device data across your fleet.
- Device Defender: To audit device configurations, detect anomalous behavior, and alert you to potential security risks.
- Auto Scaling: For your backend services (e.g., EC2 instances running your application logic, ECS/EKS clusters), configure Auto Scaling groups. This ensures that your application can automatically adjust its compute capacity to maintain performance as demand from your IoT devices fluctuates, without manual intervention.
- AWS Systems Manager: For managing your EC2 instances within the VPC, Systems Manager provides tools for operational insights, patch management, remote command execution, and more.
Best Practices and Common Pitfalls to Avoid
Building a successful remote IoT VPC network AWS requires adherence to best practices and awareness of common pitfalls.Best Practices:
- Security First: Always prioritize security. Implement the principle of least privilege for IAM roles and policies. Use strong authentication (certificates for devices), encrypt data in transit and at rest, and regularly audit your security configurations.
- Modular Design: Design your VPC and subnets with modularity in mind. Separate concerns into different subnets (e.g., IoT Core endpoints, application logic, databases) to enhance security and simplify management.
- Automate Everything: Use Infrastructure as Code (IaC) tools like AWS CloudFormation or Terraform to define and manage your VPC, subnets, security groups, and other resources. This ensures consistency, repeatability, and reduces human error.
- Monitor and Alert: Implement comprehensive monitoring using CloudWatch and set up alerts for critical metrics and security events. Proactive alerting can help you identify and respond to issues before they impact your operations.
- Cost Optimization: While AWS offers immense flexibility, costs can accumulate. Regularly review your resource utilization, right-size instances, and leverage cost-effective storage options like S3 Intelligent-Tiering. Utilize VPC Flow Logs to identify unexpected traffic patterns that might incur costs.
- Disaster Recovery and High Availability: Design your VPC across multiple Availability Zones (AZs) within a region to ensure high availability. Plan for disaster recovery scenarios, including data backups and failover strategies.
- Thorough Testing: Before deploying to production, thoroughly test your entire IoT solution, including device connectivity, data flow, security rules, and scalability under load.
Common Pitfalls to Avoid:
- Overly Permissive Security Groups/NACLs: Opening too many ports or allowing traffic from overly broad IP ranges creates significant security vulnerabilities. Be as restrictive as possible.
- Lack of IP Address Planning: Not planning your CIDR block and subnetting carefully can lead to IP address exhaustion, requiring complex re-architecture later.
- Ignoring Logging and Monitoring: Without proper logs and monitoring, you're blind to performance issues, security threats, and operational problems.
- No Device Identity Management: Relying on weak or shared credentials for devices is a major security risk. Each device needs a unique, strong identity.
- Not Using PrivateLink/VPC Endpoints: Forgoing private endpoints for services like IoT Core, S3, or DynamoDB means your data unnecessarily traverses the public internet, even within AWS, increasing latency and security risk.
Related Resources:


Detail Author:
- Name : Mr. Murl Wehner
- Username : gjohnston
- Email : clarissa.haley@willms.com
- Birthdate : 1970-12-14
- Address : 84075 Kessler Valleys New Jackyport, ME 25115-2241
- Phone : 424.578.6003
- Company : Bernier and Sons
- Job : Hazardous Materials Removal Worker
- Bio : Laborum autem autem delectus recusandae et. Quod et eum qui veniam. Animi non deleniti veritatis ut magnam harum.
Socials
twitter:
- url : https://twitter.com/elzaprohaska
- username : elzaprohaska
- bio : Ab quaerat eligendi eos explicabo sint aut. Dignissimos enim aut et harum animi hic.
- followers : 2029
- following : 2344
tiktok:
- url : https://tiktok.com/@prohaska1986
- username : prohaska1986
- bio : Rerum voluptatem provident enim esse. Excepturi et quis ducimus.
- followers : 5285
- following : 823
instagram:
- url : https://instagram.com/elza_prohaska
- username : elza_prohaska
- bio : Et inventore et voluptas dolorum libero facere. Sit dolor veniam numquam repudiandae quas.
- followers : 3849
- following : 1665
linkedin:
- url : https://linkedin.com/in/elzaprohaska
- username : elzaprohaska
- bio : Sapiente eaque voluptatem cumque officiis id et.
- followers : 2312
- following : 910