Understanding SSH: The Backbone of Remote IoT Management
Establishing Your First SSH Connection to IoT Devices
The Power of SSH Keys: Beyond Passwords for IoT Security
Advanced SSH Configuration for Seamless IoT Access
Automating IoT Commands with SSH: Scripting for Efficiency
Addressing Common SSH Challenges in IoT Environments
- Love And Light Tv Yes King Full Video Twitter
- Westland Football
- Max Dood Twitter
- Waifusummer Onlyfans
- Branch White
Preventing Idle Disconnects: Keeping Your Putty/SSH Sessions AliveUnderstanding X11 Forwarding for GUI Applications on IoT
SSH Host Keys and Trust: Securing Your IoT Connections
Best Practices for Secure SSH Remote IoT Commands
In today's interconnected world, the Internet of Things (IoT) is rapidly expanding, bringing with it an unprecedented need for secure and efficient remote management. Whether you're overseeing a smart home, an industrial sensor network, or a fleet of autonomous devices, the ability to control and monitor these devices from afar is paramount. This is where SSH remote IoT commands become not just useful, but absolutely indispensable. Secure Shell (SSH) provides a cryptographic network protocol for operating network services securely over an unsecured network, making it the de facto standard for remote administration of Linux-based IoT devices.
Navigating the complexities of remote device management can be daunting, especially when security is a critical concern. From establishing initial connections to automating routine tasks and troubleshooting common issues, a solid understanding of SSH is fundamental. This comprehensive guide will delve into the core aspects of using SSH for your IoT deployments, offering practical advice, security best practices, and solutions to common challenges, ensuring your remote IoT commands are both powerful and protected.
Understanding SSH: The Backbone of Remote IoT Management
SSH, or Secure Shell, is a network protocol that allows data to be exchanged using a secure channel between two networked devices. It's designed to replace insecure remote login protocols like Telnet and rlogin, providing strong authentication and secure communications over insecure networks. For IoT devices, which are often deployed in diverse and potentially vulnerable environments, SSH offers a lifeline for secure remote access and command execution.
The beauty of SSH lies in its ability to encrypt all traffic between the client and the server, including passwords, commands, and output. This encryption prevents eavesdropping, connection hijacking, and other network-level attacks. When you issue SSH remote IoT commands, you're not just sending instructions; you're establishing a trusted, encrypted tunnel through which your sensitive data flows securely.
The SSH Protocol: A Quick Overview
At its core, the SSH protocol operates on a client-server model. An SSH client initiates a connection to an SSH server (daemon) running on the remote device. Once the connection is established, the server authenticates the client, and if successful, a secure session is created. This session can then be used for various purposes, including:
- Remote Command Execution: Running commands directly on the IoT device.
- File Transfers: Securely copying files to and from the device using SCP (Secure Copy Protocol) or SFTP (SSH File Transfer Protocol).
- Port Forwarding/Tunneling: Creating secure tunnels for other network services.
- X11 Forwarding: Running graphical applications from the remote device on your local machine.
For IoT, the primary use case is often remote command execution, allowing administrators to update software, check sensor readings, restart services, or diagnose issues without physically interacting with the device. This capability is what truly empowers effective SSH remote IoT commands.
Establishing Your First SSH Connection to IoT Devices
The journey into managing your IoT devices remotely often begins with a simple SSH command. If you're trying to SSH login to my remote server, the basic syntax is straightforward: `ssh username@ip_address` or `ssh username@hostname`. For instance, if your IoT device has the IP address `192.168.1.100` and the default username is `pi` (common for Raspberry Pi), you would type: `ssh pi@192.168.1.100`.
Upon your first connection to a new device, SSH will typically prompt you to verify the server's host key. This is a critical security measure. The prompt will ask something like, "The authenticity of host '192.168.1.100' can't be established. Are you sure you want to continue connecting (yes/no/[fingerprint])?". This is part of how the server identifies itself to you, using its host key. You should always verify this fingerprint against a known good one if possible, especially in production environments, to prevent man-in-the-middle attacks. Once confirmed, the host key is stored in your `~/.ssh/known_hosts` file, and clients remember the host key associated with a particular host.
Troubleshooting Connection Errors: "Connection Closed"
It's not uncommon to encounter issues when trying to connect. But whenever I try to login through terminal using ssh command, for example, `ssh root@{ip_address}`, I get an error like "Connection closed by {ip_address}". This is a common frustration, and several factors can cause it:
- Incorrect IP Address or Hostname: Double-check the IP address or hostname. A simple typo can prevent a connection.
- SSH Server Not Running: The `sshd` service might not be running on your IoT device. You'd need physical access or another remote method to start it.
- Firewall Issues: A firewall on either your client machine or the IoT device (or an intermediary network device) might be blocking port 22 (the default SSH port). You might need to open port 22 on the IoT device's firewall.
- Incorrect Credentials: If you're using password authentication, ensure the username and password are correct.
- SSH Configuration Restrictions: The `sshd_config` file on the IoT device might have restrictions, such as disallowing root login (`PermitRootLogin no`) or only allowing specific users. If you're trying to SSH login as `root`, and it's disabled, you'll be rejected.
- Host Key Mismatch: If the host key on the server has changed (e.g., after reinstalling the OS), your client will detect a mismatch and refuse to connect. You'll get a warning about a "POSSIBLE DNS SPOOFING" or "REMOTE HOST IDENTIFICATION HAS CHANGED!" error. You'll need to remove the old entry from your `~/.ssh/known_hosts` file.
When you get "Connection closed by {ip_address}", I checked hosts, firewalls, and `sshd_config` on the remote device. These are usually the first places to look. For example, if `PermitRootLogin` is set to `no` in `/etc/ssh/sshd_config`, trying to log in as `root` will always result in a connection closed error.
The Power of SSH Keys: Beyond Passwords for IoT Security
While password authentication is an option, it's generally considered less secure for IoT devices. Passwords can be brute-forced, guessed, or intercepted. The gold standard for SSH authentication, especially for SSH remote IoT commands, is public-private key authentication. This method is far more secure and convenient, eliminating the need to type a password for every connection.
When you connect to an SSH server, you identify yourself to the server (using either your login and password, or a key), and the server identifies itself to you, using its host key. With key-based authentication, you generate a pair of cryptographic keys: a private key (which you keep secret and secure on your local machine) and a public key (which you place on the remote IoT device). When you attempt to connect, the server challenges your client, which then uses your private key to prove your identity without ever sending the private key itself over the network.
Generating and Managing SSH Keys
Generating an SSH key pair is a straightforward process. You typically use the `ssh-keygen` command. For example, if I was also following these instructions and was quite new to this, I'd start with `ssh-keygen -t rsa -b 4096 -C "your_email@example.com"`. This command creates a 4096-bit RSA key pair. When prompted, "Enter file in which to save the key," you can press Enter to accept the default location (`~/.ssh/id_rsa`) or specify a new path. It's highly recommended to set a strong passphrase for your private key, which adds an extra layer of security.
Then I looked up on the internet and found that I had to generate an SSH key for my account on GitHub. This is a common scenario, as many services (like GitHub, GitLab, and cloud providers) leverage SSH keys for secure access. The process is identical; you generate the key locally and then add the *public* key to your account settings on the respective service or to the `~/.ssh/authorized_keys` file on your IoT device.
Once generated, you need to copy your public key to the IoT device. The `ssh-copy-id` command is the easiest way: `ssh-copy-id username@ip_address`. If `ssh-copy-id` isn't available or you prefer manual methods, you can copy the contents of your public key file (e.g., `~/.ssh/id_rsa.pub`) and paste it into the `~/.ssh/authorized_keys` file on the remote device. Ensure the `~/.ssh` directory and `authorized_keys` file have the correct permissions (e.g., `chmod 700 ~/.ssh` and `chmod 600 ~/.ssh/authorized_keys`).
Configuring Multiple SSH Keys for Diverse IoT Deployments
As your IoT ecosystem grows, you might find yourself needing to manage multiple SSH keys. For instance, you might have one key for personal devices, another for work-related IoT deployments, and yet another for specific services like Git. Now I want to use multiple SSH keys (so my key will get the name `id_rsa_test`), so how do I configure the `.ssh/config` file under Windows, that it works with a usual Git server?
The `~/.ssh/config` file is your best friend for managing multiple keys and custom SSH settings. This variable sounds like what I am looking for, but it is not defined by default; you'll need to create it. You can define specific hosts or patterns and associate them with different private keys. Here's an example:
Host my_iot_device_alpha HostName 192.168.1.101 User pi IdentityFile ~/.ssh/id_rsa_alpha_iot Host my_iot_device_beta HostName 192.168.1.102 User admin IdentityFile ~/.ssh/id_rsa_beta_iot Host github.com HostName github.com User git IdentityFile ~/.ssh/id_rsa_test IdentitiesOnly yes With this configuration, you can simply type `ssh my_iot_device_alpha` to connect to `192.168.1.101` using the `id_rsa_alpha_iot` key. For GitHub, you'd use `ssh git@github.com`, and it would automatically pick up `id_rsa_test`. This makes managing SSH remote IoT commands across different environments much more efficient and secure.
Advanced SSH Configuration for Seamless IoT Access
Beyond basic connections and key management, the `~/.ssh/config` file offers powerful options to streamline your SSH remote IoT commands and improve your workflow. This configuration file allows you to define aliases, specify non-standard ports, enable connection persistence, and much more.
For IoT deployments, where devices might be behind firewalls or on non-standard ports, configuring these settings in `~/.ssh/config` saves time and reduces errors. What is interesting there is the line defining a specific host and its associated settings. This centralizes your connection parameters, making it easier to manage a fleet of devices.
Setting Up ~/.ssh/config on Windows (OpenSSH)
For Windows users, especially those using OpenSSH through PowerShell or Command Prompt, the `~/.ssh/config` file works similarly to Linux/macOS. How do I set the host name and port in a config file for Windows, using OpenSSH through PowerShell? The process is identical: the file is located at `C:\Users\YourUsername\.ssh\config`.
Edit or create the file now by typing `notepad C:\Users\YourUsername\.ssh\config` in PowerShell or Command Prompt. Then, you can add entries like this:
Host my_windows_iot_device HostName 192.168.1.103 User admin Port 2222 # If your device listens on a non-standard port IdentityFile C:\Users\YourUsername\.ssh\id_rsa_windows_iot This allows you to simply type `ssh my_windows_iot_device` from your PowerShell terminal, and OpenSSH will handle the custom port and key file automatically. This is particularly useful for SSH remote IoT commands where devices might have varied network configurations.
Automating IoT Commands with SSH: Scripting for Efficiency
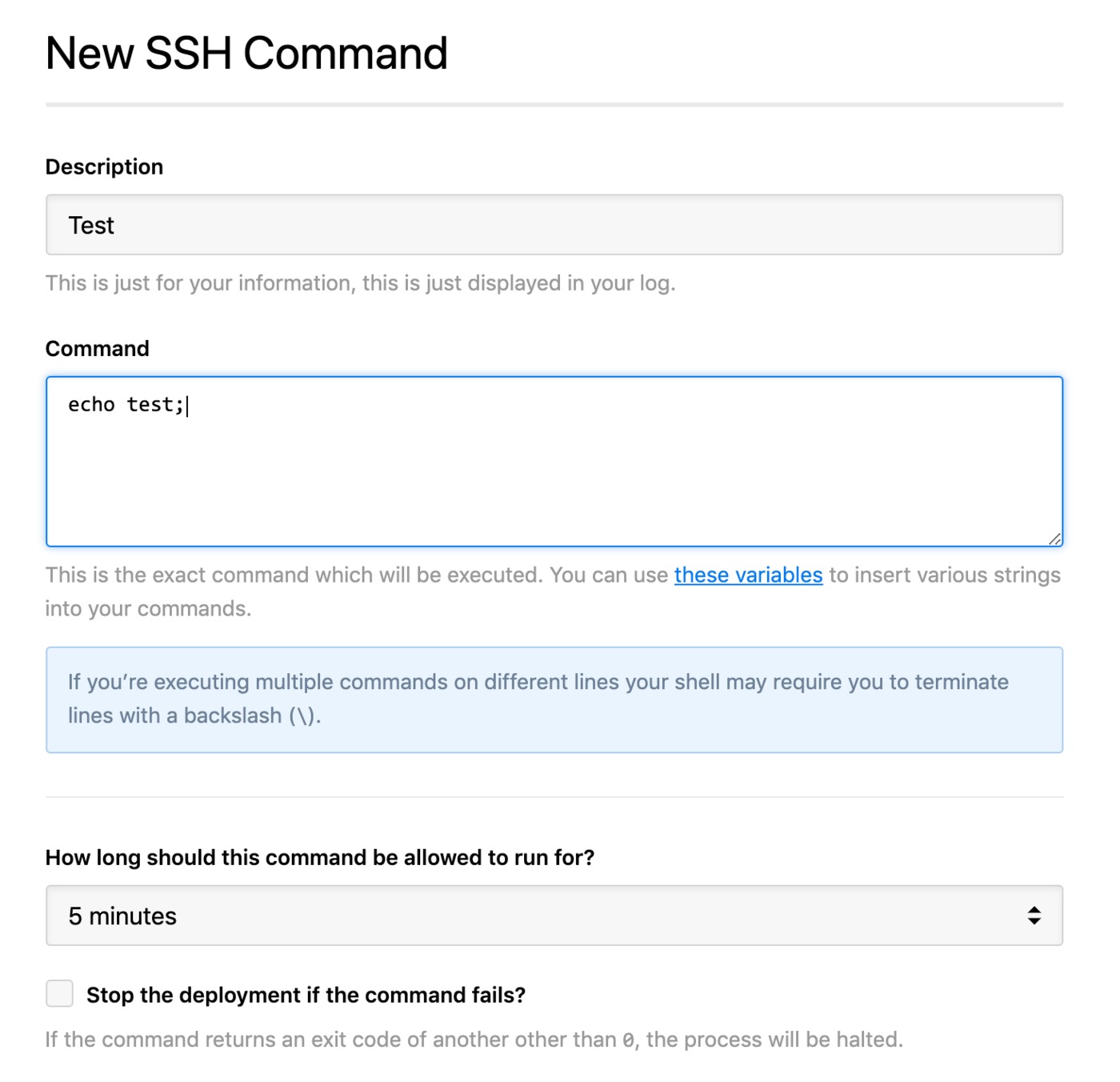
The true power of SSH for IoT comes alive with automation. Manually logging into each device to run commands is inefficient and prone to human error, especially with a large number of devices. This is where scripting SSH remote IoT commands becomes essential. Automation allows you to deploy updates, collect data, or perform maintenance tasks across your entire fleet with a single script.
We have a Windows batch script, which connects automatically to a Linux server via Plink (Putty). This illustrates a common scenario: automating connections from a Windows environment. However, there is no public private key authentication; the user and the password are in the script. While this might seem convenient, it's a significant security risk. Embedding passwords directly in scripts exposes them to anyone who can read the script, making your IoT infrastructure vulnerable. Always prioritize key-based authentication for automation.
Scripting SSH Commands from Server to Server
A common advanced use case is creating a bash script from server 1 that will execute some commands on server 2 via SSH. This is perfect for orchestrating tasks between different parts of your IoT backend or for managing a hierarchical network of devices. How do I SSH to server 2 using my private key file from server 1?
You can achieve this in several ways:
- Direct Command Execution:
The simplest way is to pass the command directly to SSH:
ssh -i /path/to/your/private_key_on_server1/id_rsa_server2_key user@server2_ip "ls -l /var/log/iot_data"This command logs into `server2_ip` as `user` using the specified private key and immediately executes `ls -l /var/log/iot_data`. The output is returned to `server1`.
- Using `~/.ssh/config` on Server 1:
Even better, configure `~/.ssh/config` on Server 1 to define Server 2:
Host server2_alias HostName server2_ip User user IdentityFile ~/.ssh/id_rsa_server2_keyThen, your script on Server 1 can simply use:
ssh server2_alias "sudo systemctl restart iot_service"This is cleaner and more secure as the key path isn't hardcoded in every command. Remember, the private key `id_rsa_server2_key` must reside securely on Server 1.
- Executing Multiple Commands or Scripts:
For multiple commands or a full script, you can pipe a local script to SSH:
ssh user@server2_ip < local_script.shOr use a "here document" in your bash script on Server 1:
ssh user@server2_ip << EOF # Commands to execute on Server 2 sudo apt update sudo apt upgrade -y echo "Updates complete!" EOF
These methods are crucial for robust SSH remote IoT commands, enabling complex automation workflows while maintaining security through key-based authentication.
Addressing Common SSH Challenges in IoT Environments
Even with a solid understanding of SSH, you might encounter specific challenges in IoT deployments. These often relate to network stability, resource constraints on devices, or specific application requirements. Knowing how to troubleshoot these issues is key to maintaining reliable SSH remote IoT commands.
Preventing Idle Disconnects: Keeping Your Putty/SSH Sessions Alive
A common annoyance, especially when monitoring IoT devices over long periods, is idle session disconnects. A Putty session left idle will disconnect at a time determined by the host server, or by network intermediaries. This can be frustrating if you're waiting for a specific event or simply keeping a session open for quick access.
The solution typically involves configuring the SSH client to send "keep-alive" packets. This causes Putty to send null SSH packets to the remote server at regular intervals, preventing the connection from being considered idle. In Putty, you can find this option under Connection -> Seconds between keepalives (0 to disable). Set it to a value like 300 (5 minutes). For OpenSSH clients, you can add `ServerAliveInterval 60` to your `~/.ssh/config` file under the specific host or globally. This tells your client to send a null packet to the server every 60 seconds if no data has been exchanged.
Understanding X11 Forwarding for GUI Applications on IoT
While most IoT interactions are command-line based, sometimes you might need to run a graphical application on your remote IoT device and display its interface on your local machine. This is where X11 forwarding comes in. If you run `ssh` and `DISPLAY` is not set, it means SSH is not forwarding the X11 connection, and any graphical applications you try to run will fail to display.
To enable X11 forwarding, use the `-X` option with your SSH command: `ssh -X user@ip_address`. On the server side, X11 forwarding must also be enabled in `/etc/ssh/sshd_config` (look for `X11Forwarding yes`). To confirm that SSH is forwarding X11, check for a line containing "requesting X11 forwarding" in your SSH client's verbose output (`ssh -v -X user@ip_address`). You'll also need an X server running on your local machine (e.g., Xming for Windows, XQuartz for macOS, or a desktop environment on Linux). Once configured, you can run a GUI application on your IoT device, and its window will appear on your local desktop.
SSH Host Keys and Trust: Securing Your IoT Connections
Security is paramount in IoT. Every host has a key when using SSH, and this host key plays a crucial role in establishing trust between your client and the remote IoT device. When you connect to an SSH server, you identify yourself to the server (using either your login and password, or a key), and the server identifies itself to you, using its host key. This two-way identification process is fundamental to SSH's security model.
Clients remember the host key associated with a particular
Related Resources:


Detail Author:
- Name : Piper Baumbach
- Username : xleffler
- Email : jarret.will@hotmail.com
- Birthdate : 1994-12-10
- Address : 13238 Langworth Corners Suite 743 Dareborough, NH 30121
- Phone : 1-916-303-1679
- Company : Raynor-Cruickshank
- Job : Biochemist or Biophysicist
- Bio : Omnis placeat error nostrum sunt esse nesciunt. Laudantium quia sit quam est sed corporis. Consequatur quas recusandae sed ipsa iure sint deserunt. Culpa soluta sunt quis dolore et.
Socials
tiktok:
- url : https://tiktok.com/@bogisich2024
- username : bogisich2024
- bio : Dolor rerum id cupiditate ad quia voluptatem.
- followers : 1577
- following : 526
twitter:
- url : https://twitter.com/emma_official
- username : emma_official
- bio : Laborum mollitia ab magni voluptatem assumenda aliquid vel. Accusamus praesentium sunt voluptate vitae dignissimos.
- followers : 414
- following : 2676