**In today's interconnected world, the Internet of Things (IoT) is rapidly transforming industries, homes, and cities. From smart thermostats to industrial sensors, these devices collect vast amounts of data and often perform critical functions. However, this convenience comes with a significant challenge: security. Protecting these myriad endpoints from unauthorized access and cyber threats is paramount, and this is where an effective **ssh remoteiot example** becomes not just useful, but essential.** Without robust security measures, IoT devices can become vulnerable entry points for attackers, leading to data breaches, system compromises, or even physical damage. The very nature of IoT – distributed, often resource-constrained devices – makes traditional security models difficult to implement. This necessitates a lightweight yet powerful solution for remote management and secure communication. Secure Shell (SSH) emerges as a cornerstone technology, offering a cryptographically secure network protocol for remote command-line access and file transfers. Understanding how to effectively leverage SSH for your IoT deployments is crucial for maintaining control, ensuring data integrity, and safeguarding your entire ecosystem.
Table of Contents
- The Imperative of Secure IoT: Why SSH?
- Understanding the Core: What is SSH?
- SSH Authentication: Keys vs. Passwords in IoT
- Advanced SSH Configurations for IoT Devices
- Maintaining Persistent SSH Connections in IoT
- Troubleshooting Common SSH Remote IoT Connection Issues
- Scripting SSH for Automated IoT Management
- The Future of Secure IoT with SSH
The Imperative of Secure IoT: Why SSH?
The sheer volume and diversity of IoT devices present a unique security landscape. Many of these devices operate in remote, unattended locations, making physical access impractical for routine maintenance or troubleshooting. This is precisely where remote access protocols become indispensable. However, using insecure methods like Telnet or unencrypted HTTP for device management is akin to leaving your front door wide open. Such practices invite malicious actors to eavesdrop on communications, inject malware, or seize control of devices, potentially turning them into botnet participants or launching pads for larger attacks. SSH, or Secure Shell, provides a robust solution by encrypting all communication between the client (your computer) and the server (your IoT device). This encryption ensures that data, including credentials, commands, and output, remains confidential and protected from interception. Beyond encryption, SSH offers strong authentication mechanisms, verifying the identity of both the user and the device. For any practical **ssh remoteiot example**, security must be the top priority, and SSH delivers on this promise by providing a secure channel for managing distributed IoT infrastructure. It's not just about convenience; it's about safeguarding critical operations and sensitive data.Understanding the Core: What is SSH?
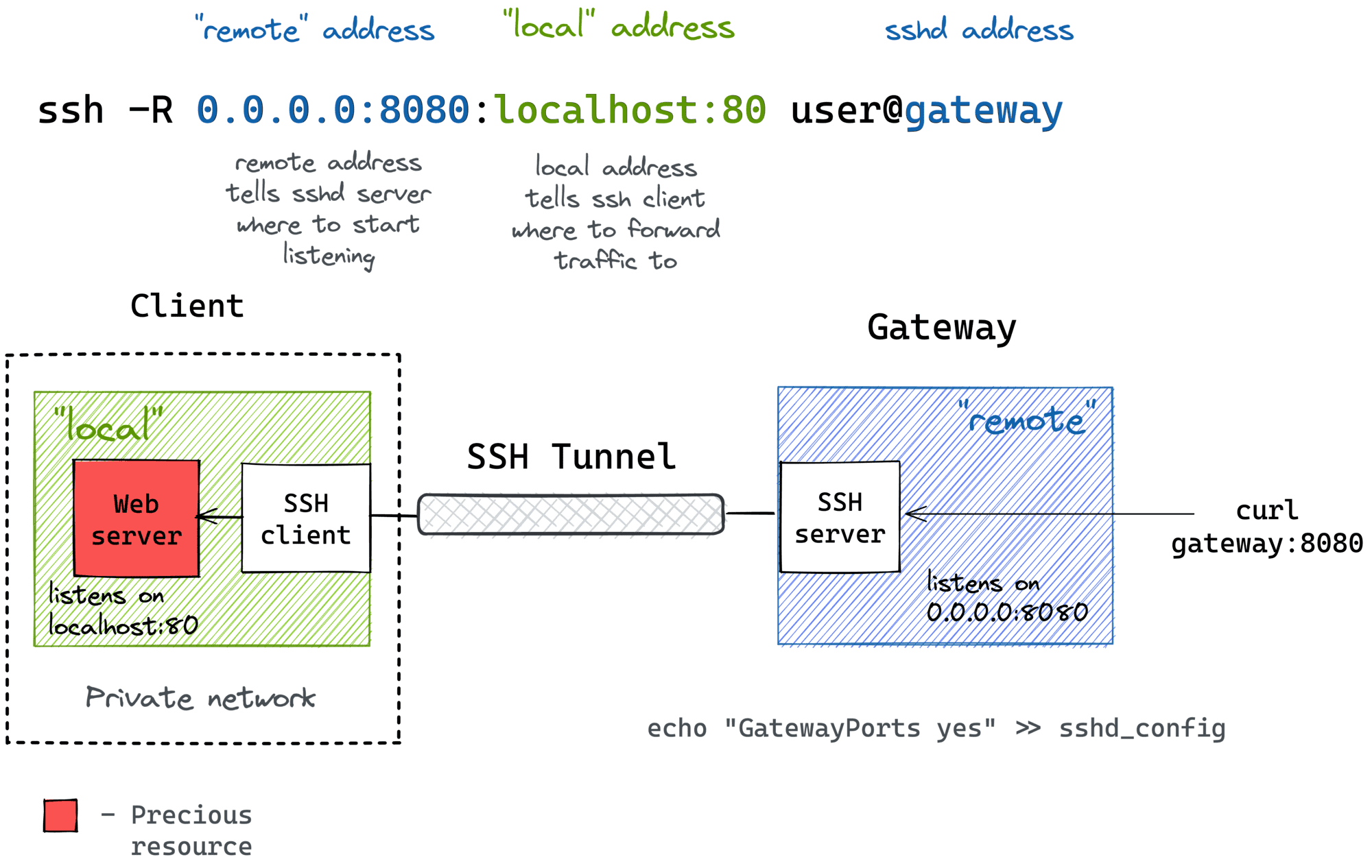
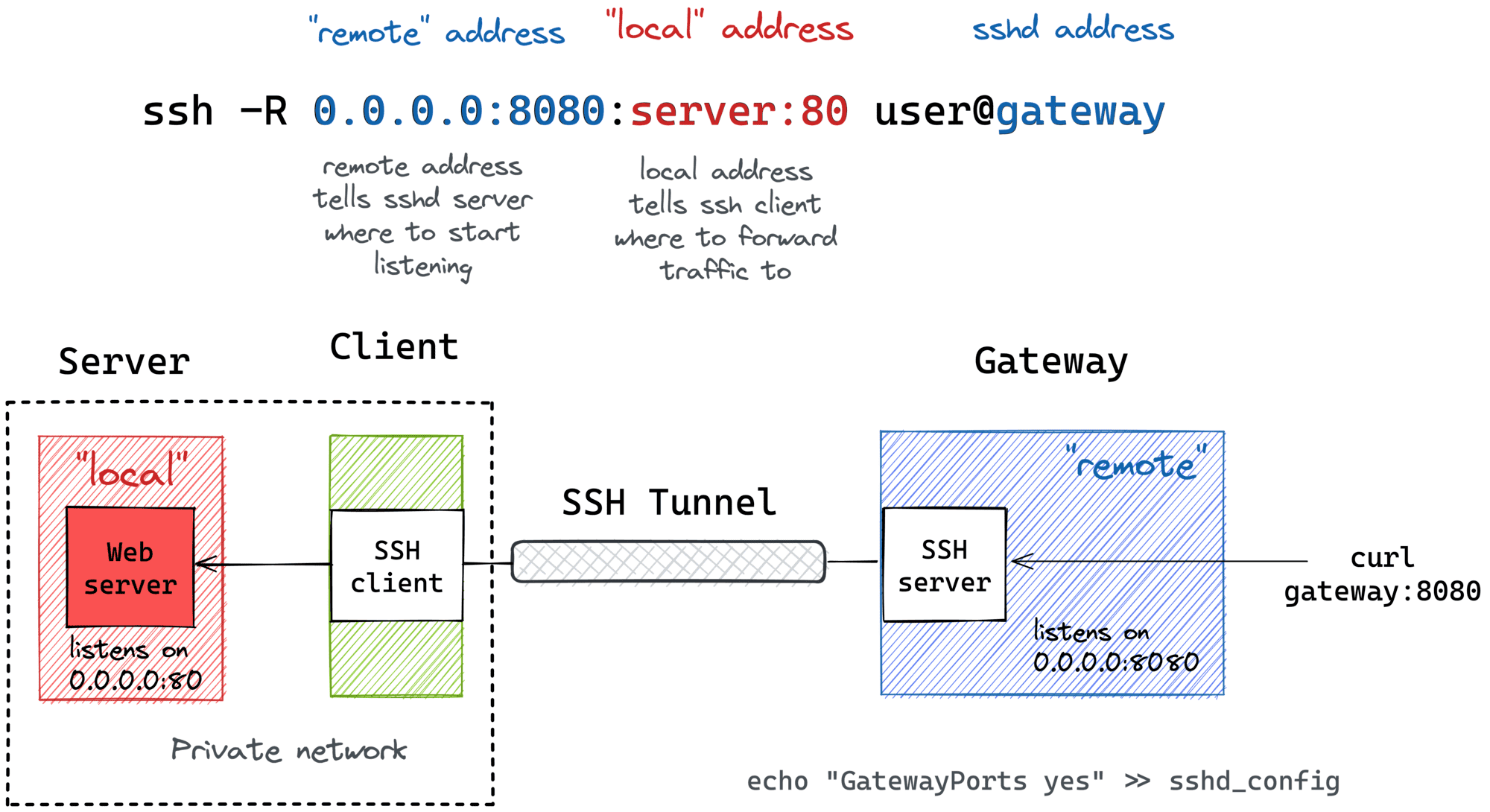
At its heart, SSH is a network protocol that enables secure data communication between two networked devices. It operates on a client-server model. An SSH client initiates a connection to an SSH server (often `sshd` on Linux-based IoT devices). Once the connection is established, SSH provides a secure channel over an unsecured network by using strong encryption algorithms. This secure channel can then be used for various purposes, including remote command execution, secure file transfer (using SCP or SFTP), and even tunneling other protocols. When you connect to an SSH server, you identify yourself to the server (using either your login and password, or a key), and the server identifies itself to you, using its host key. This mutual authentication is a critical security feature. The host key, typically based on a file like `/etc/ssh/ssh_host_rsa_key.pub`, generates a fingerprint. This fingerprint is generally for easy identification/verification of the host, helping you confirm that you are connecting to the legitimate device and not a malicious imposter. It's a foundational element for building any secure **ssh remoteiot example**. A common misconception is that SSH always runs on port 22. While this is the default, the ssh server you are attempting to connect to will have sshd running on one port and that need not be 22. Many servers move SSH to a high port to cut down on the number of automated scanning attempts from bots looking for default SSH services. This simple change can significantly reduce the noise in your logs and add a layer of obscurity, making your IoT devices less obvious targets for casual attackers.SSH Authentication: Keys vs. Passwords in IoT
One of the most critical decisions in setting up an **ssh remoteiot example** is choosing the authentication method. SSH supports two primary methods: password-based authentication and public-key authentication. While both can provide secure access, their implications for IoT security and management differ significantly. ### The Power of SSH Keys For most IoT deployments, public-key authentication is the gold standard. This method involves a pair of cryptographic keys: a public key and a private key. The public key is placed on the IoT device (server), and the private key remains securely on your local machine (client). When you attempt to connect, the server challenges your client, which then uses its private key to prove its identity without ever sending the private key over the network. This is vastly more secure than passwords because: 1. **No Password Transmission:** Passwords, even encrypted, are vulnerable to brute-force attacks if intercepted. Keys are never transmitted. 2. **Stronger Security:** Key pairs are typically much longer and more complex than any human-generated password, making them virtually impossible to guess or crack. 3. **Automation Friendly:** Keys enable seamless, scriptable access without human intervention, ideal for automated IoT management tasks. 4. **Revocation:** If a private key is compromised, it can be easily revoked on the server without affecting other users or devices. When trying to generate a public key for my Git, for instance, the process typically involves `ssh-keygen` and prompts like "Enter file in which to save the..." This process is identical for generating keys for your IoT devices. It's a fundamental step for any secure **ssh remoteiot example**. I can speculate that this prevents adding your public key (which is paired with encrypted private key) without proper authorization, ensuring only trusted keys are installed. ### When Passwords are (Sometimes) Necessary Despite the clear advantages of SSH keys, there are scenarios where password-based authentication might seem necessary, or where it's the only immediate option. For example, you might need to log in to a machine using a password instead of a key, which I practically never do. Seems it should be easy but nope, SSH refuses to use anything but a key if a key is configured and preferred. This often happens when a system is strictly configured for key-only access for enhanced security. Remote SSH login password would be enough in this case for initial setup or emergency access, but it should be immediately replaced with key-based authentication. If you find yourself in a situation where you need to use a password, ensure it's strong, unique, and changed regularly. For production IoT deployments, relying solely on passwords is a significant security risk and should be avoided at all costs.Advanced SSH Configurations for IoT Devices
Optimizing SSH for IoT goes beyond basic connectivity. Advanced configurations can enhance security, streamline management, and improve the reliability of your remote connections. ### Custom Ports and Host Key Fingerprints As mentioned earlier, moving SSH from its default port 22 to a higher, non-standard port (e.g., 2222 or 22022) is a simple yet effective security measure. This doesn't stop a determined attacker, but it significantly reduces the volume of automated scanning and brute-force attempts against your IoT devices. When configuring your SSH client, you'll specify this custom port. Another critical aspect is understanding host key fingerprints. The fingerprint is based on the host's public key, usually based on the `/etc/ssh/ssh_host_rsa_key.pub` file. Generally, it's for easy identification/verification of the host. When you first connect to a new SSH server, your client will present this fingerprint and ask you to verify it. Always verify this fingerprint against a known-good source (e.g., from the device's documentation or a trusted out-of-band communication channel) before proceeding. This prevents "man-in-the-middle" attacks where an attacker impersonates your IoT device. ### Managing Multiple SSH Keys and Configuration Files For complex IoT deployments, you might be managing access to dozens or even hundreds of devices, each potentially requiring different SSH keys or configurations. This is where the SSH client configuration file (`~/.ssh/config` on Linux/macOS, or `%USERPROFILE%\.ssh\config` on Windows OpenSSH) becomes invaluable. This file allows you to define aliases, specify custom ports, user names, and, crucially, point to specific private keys for different hosts. For example, if you want to use multiple SSH keys (so my key will get the name `id_rsa_test`), you can configure the `.ssh/config` file under Windows so that it works with a usual Git server, and similarly for your IoT devices. A typical entry might look like this: ``` Host my_iot_device_alpha HostName 192.168.1.100 User admin Port 2222 IdentityFile ~/.ssh/id_rsa_iot_alpha Host my_iot_device_beta HostName iot.example.com User root Port 22 IdentityFile ~/.ssh/id_rsa_iot_beta ``` This variable sounds like what I am looking for, but it is not defined by default, you need to create or edit the file. To edit or create the file now, you can simply type `notepad %USERPROFILE%\.ssh\config` in PowerShell for Windows, or `nano ~/.ssh/config` on Linux. This centralizes your SSH settings, making it much easier to manage connections to a diverse fleet of IoT devices, a practical **ssh remoteiot example** of efficient management. The documentation is not always clear on how to explicitly use only that key, but by specifying `IdentityFile` in your config, SSH will automatically try that specific key for the corresponding host. This avoids issues where SSH tries all available keys, which can sometimes lead to connection delays or errors if too many keys are offered.Maintaining Persistent SSH Connections in IoT
A common challenge when managing remote IoT devices is maintaining a stable SSH connection. I have an SSH connection to a machine which gets disconnected by that machine after 30 minutes of no user input. However, if I start something like `top`, the connection stays alive. This behavior is typically due to server-side timeouts or network inactivity. To combat this, you can configure your SSH client to send "keep-alive" packets. These small packets are sent periodically to prevent the connection from timing out due to inactivity. You can add the following lines to your `~/.ssh/config` file for specific hosts or globally: ``` Host * ServerAliveInterval 60 ServerAliveCountMax 3 ``` `ServerAliveInterval 60` tells the client to send a keep-alive message every 60 seconds if no data has been received from the server. `ServerAliveCountMax 3` means the client will try 3 times before giving up and closing the connection. This ensures your **ssh remoteiot example** connections remain active even during periods of low activity, crucial for monitoring or long-running processes on resource-constrained devices.Troubleshooting Common SSH Remote IoT Connection Issues
Even with the best configurations, you might encounter issues when trying to connect to your IoT devices via SSH. I am trying to SSH login to my remote server, but whenever I try to login through terminal using `ssh root@{ip_address}` I get an error: "Connection closed by {ip_address}." I checked hosts. This is a common problem with several potential causes: 1. **Incorrect Credentials/Keys:** Double-check the username, password, or ensure the correct private key is being used and has the right permissions (`chmod 400 private_key`). 2. **Firewall Issues:** A firewall on either the client, the network path, or the IoT device itself might be blocking the connection. Ensure the SSH port (default 22 or your custom port) is open. 3. **SSH Server Not Running:** The `sshd` service might not be running on the IoT device. You might need to physically access the device or use an alternative management interface to restart it. 4. **Incorrect IP Address/Hostname:** Verify the IP address or hostname is correct and resolvable. 5. **Host Key Mismatch:** If the host key fingerprint has changed (e.g., after reinstalling the OS on the IoT device), your client will refuse to connect due to a security warning. You'll need to remove the old entry from your `~/.ssh/known_hosts` file. 6. **Unsupported Algorithms:** Sometimes, the client and server might not agree on common MACs, ciphers, or key exchange algorithms. Is there a way to make SSH output what MACs, ciphers, and KexAlgorithms that it supports? I'd like to find out dynamically instead of having to look at the source. You can use the `-v` (verbose) flag with your SSH command (`ssh -v user@host`) to get detailed debugging output, which often reveals these negotiation failures. For more specific algorithm support, you might need to consult the `sshd_config` file on the server or the `ssh_config` on the client, or even the OpenSSH documentation for your specific version. When troubleshooting, starting with verbose output (`ssh -vvv`) is often the most effective way to pinpoint the exact point of failure. This detailed log can reveal issues with authentication, key exchange, or network connectivity, guiding you towards a solution for your **ssh remoteiot example** connection woes.Scripting SSH for Automated IoT Management
The true power of SSH in an IoT context shines when it's integrated into automated scripts. Manually logging into dozens or hundreds of devices is simply not scalable. We have a Windows batch script, which connects automatically to a Linux server via Plink (PuTTY Link). There is no public-private key authentication; the user and the password are in the script. While this approach works, hardcoding credentials directly into scripts is a significant security vulnerability. Anyone with access to the script can gain access to your devices. For a robust and secure **ssh remoteiot example** in automation, always use SSH keys. Tools like `sshpass` (for Linux/macOS, though generally discouraged for security reasons in production) or PuTTY's `plink` (for Windows) can be used in scripts, but they should always be combined with key-based authentication. Here's a more secure approach for Windows using OpenSSH through PowerShell, building on the `.ssh/config` file: ```powershell # Example PowerShell script to run a command on an IoT device # Ensure your .ssh/config file is set up for 'my_iot_device_alpha' with IdentityFile $iotDevice = "my_iot_device_alpha" $command = "uptime" try { Write-Host "Connecting to $iotDevice and executing '$command'..." $result = ssh $iotDevice $command Write-Host "Command Output:" Write-Host $result } catch { Write-Error "Failed to connect or execute command on $iotDevice. Error: $($_.Exception.Message)" } ``` This script leverages the `Host` entry defined in your `.ssh/config` file, automatically using the correct user, port, and most importantly, the SSH key. This makes your automation both powerful and secure. For more complex tasks, consider using configuration management tools like Ansible, which rely heavily on SSH for agentless management of remote hosts, including IoT devices.The Future of Secure IoT with SSH
As IoT continues to expand, the need for secure, scalable, and manageable remote access solutions will only grow. SSH, with its long-standing reputation for security and flexibility, is well-positioned to remain a cornerstone technology for **ssh remoteiot example** deployments. Future developments may include tighter integration with device identity management systems, enhanced hardware-backed key storage on IoT devices, and more sophisticated anomaly detection based on SSH connection patterns. Beyond the technical configurations, the human element remains crucial. Regular security audits, prompt patching of SSH vulnerabilities, and strict adherence to best practices for key management are paramount. Education for developers and administrators on secure SSH usage is also vital. By embracing SSH's capabilities and continuously refining our security posture, we can ensure that the promise of a connected future is realized without compromising privacy, safety, or operational integrity.Conclusion
Securing your Internet of Things infrastructure is not merely an option; it's a fundamental requirement in today's digital landscape. As we've explored, SSH provides a robust, flexible, and highly secure protocol for managing and interacting with your remote IoT devices. From understanding the core principles of SSH authentication using keys over passwords, to mastering advanced configurations like custom ports and `~/.ssh/config` files, and troubleshooting common connection issues, every **ssh remoteiot example** benefits from a deep understanding of this powerful tool. The ability to maintain persistent connections, dynamically discover server capabilities, and, most importantly, script automated management tasks securely using SSH keys, transforms the daunting task of IoT fleet management into an efficient and reliable process. By prioritizing strong authentication, diligent configuration, and continuous vigilance, you can harness the full potential of your IoT deployments while mitigating the inherent security risks. We encourage you to implement these best practices in your own IoT projects. Share your experiences in the comments below – what challenges have you faced with SSH in IoT, and what solutions have you found most effective? Your insights can help others navigate the complexities of securing the connected world. For more detailed guides on specific SSH configurations or advanced security topics, explore other articles on our site.Related Resources:

Detail Author:
- Name : Dr. Dandre O'Conner
- Username : kilback.felicita
- Email : dino.conn@ryan.com
- Birthdate : 1977-07-21
- Address : 5409 Tromp Knolls New Destineyville, ME 40236
- Phone : 614.560.6109
- Company : Gutmann Ltd
- Job : Scientific Photographer
- Bio : Eius eveniet facilis non esse. Ut necessitatibus dolores architecto accusantium et dolores. Consequatur reprehenderit culpa veritatis error laborum ex exercitationem et.
Socials
tiktok:
- url : https://tiktok.com/@tomas.conroy
- username : tomas.conroy
- bio : Ut explicabo perspiciatis animi. Ea sequi sint iure soluta.
- followers : 1542
- following : 1646
linkedin:
- url : https://linkedin.com/in/tomas_conroy
- username : tomas_conroy
- bio : Eum dicta est soluta.
- followers : 4522
- following : 2170