In an increasingly interconnected world, the Internet of Things (IoT) is no longer a futuristic concept but a foundational element of modern infrastructure, driving innovation across industries from smart cities to industrial automation and healthcare. However, the true power of IoT is unlocked when devices can operate seamlessly and securely from virtually anywhere, necessitating a robust and well-architected network foundation. This is precisely where the concept of a remoteiot vpc network aws becomes not just beneficial, but absolutely critical for success.
The sheer volume and geographical dispersion of IoT devices present unique challenges, particularly concerning security, scalability, and reliable connectivity. Imagine a vast fleet of sensors deployed across continents, each collecting vital data, or critical industrial machinery reporting its status in real-time. Ensuring that this data flows securely and efficiently, without exposing sensitive information or compromising operational integrity, requires a dedicated and isolated networking environment. AWS Virtual Private Cloud (VPC) provides this private, on-demand network, offering the control and flexibility needed to manage remote IoT deployments with confidence and precision.
Table of Contents
- The Imperative of Secure IoT Connectivity: Why RemoteIoT Matters
- Understanding AWS VPC: Your Private Cloud Foundation
- Architecting Your RemoteIoT VPC Network on AWS
- Enhancing Security and Compliance in Your IoT VPC
- Scalability and Resilience for Global RemoteIoT Deployments
- Advanced RemoteIoT Use Cases and Best Practices
- The E-E-A-T and YMYL Perspective on RemoteIoT VPC Networks
- Conclusion
The Imperative of Secure IoT Connectivity: Why RemoteIoT Matters
The proliferation of IoT devices has transformed countless industries, offering unprecedented insights and automation capabilities. From smart homes and wearable tech to complex industrial control systems and precision agriculture, devices are increasingly deployed in remote, often unsecured, environments. This "remote" aspect of IoT brings forth a unique set of challenges that traditional networking models struggle to address. How do you securely connect a sensor in a remote oil field, a smart meter in a residential area, or a medical device in a patient's home, all while ensuring data integrity and protecting against cyber threats? The answer lies in a robust and secure network architecture. Without it, IoT deployments become vulnerable to a myriad of risks: data breaches, unauthorized access, denial-of-service attacks, and even physical tampering. Imagine a critical infrastructure system, like a power grid, relying on compromised IoT devices – the potential for widespread disruption and financial loss is immense. Furthermore, the sheer scale of IoT, with billions of devices expected to be connected in the coming years, demands a network solution that can not only handle massive data volumes but also scale effortlessly without compromising performance or security. This is where the strategic implementation of a remoteiot vpc network aws becomes indispensable, providing a dedicated, isolated, and highly configurable environment for your IoT ecosystem. It's about ensuring that your remote devices, no matter where they are, operate within a trusted and controlled digital perimeter.Understanding AWS VPC: Your Private Cloud Foundation
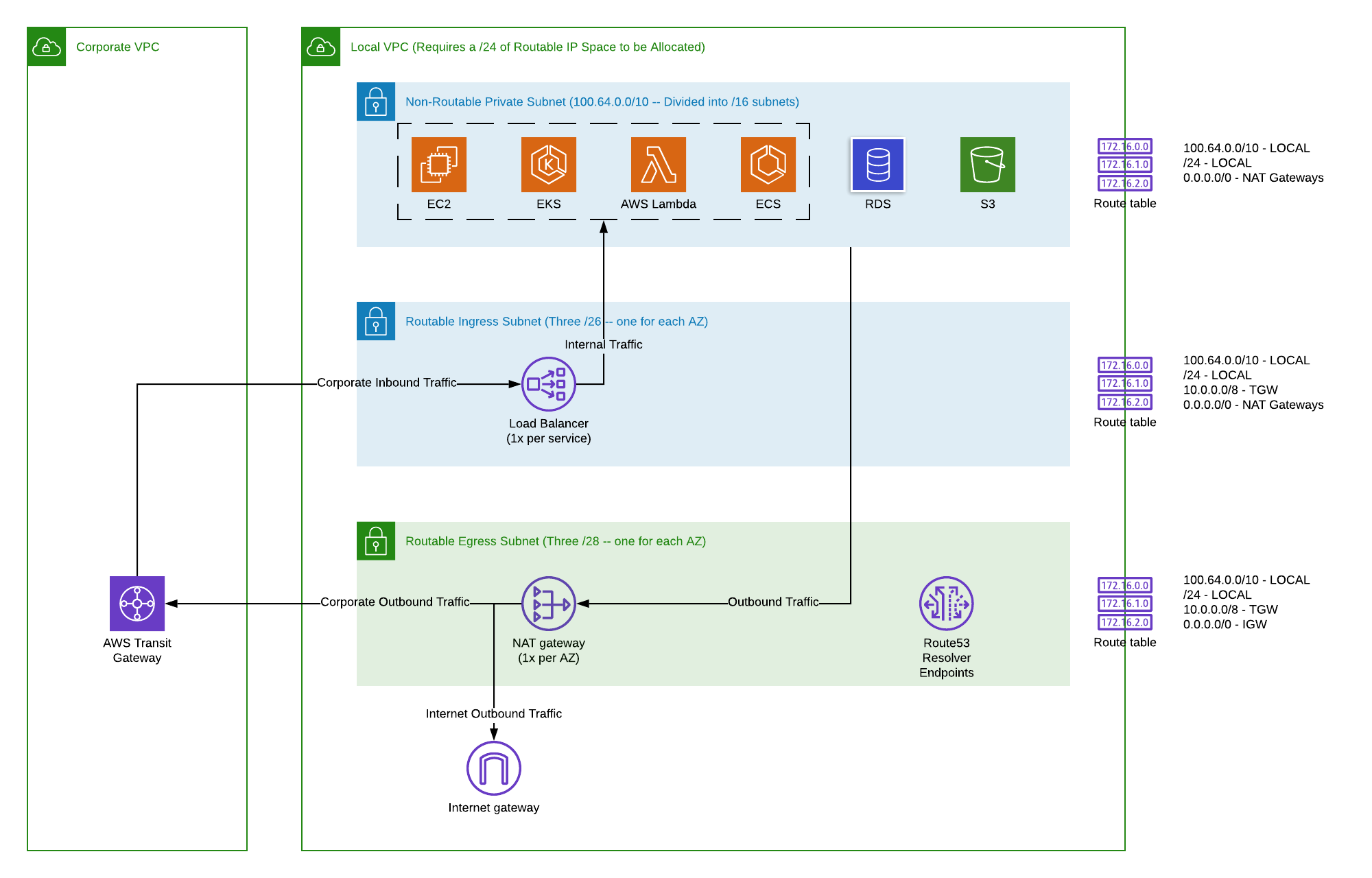
At its core, an AWS Virtual Private Cloud (VPC) is your own isolated section of the AWS cloud, where you can launch AWS resources in a virtual network that you define. Think of it as building your own private data center within AWS, complete with your own IP address ranges, subnets, route tables, network gateways, and security configurations. This level of isolation and control is paramount for any enterprise-grade application, and it is especially crucial for securing the diverse and often sensitive data streams generated by IoT devices. Within your VPC, you have granular control over your network environment. You can define IP address ranges (CIDR blocks), create subnets to segment your network, and configure route tables to dictate how traffic flows between these subnets and to the internet. Key components that make up a robust VPC include: * **Subnets:** Logical subdivisions of your VPC's IP address range. You can designate subnets as "public" (with a route to an Internet Gateway) for resources that need direct internet access, or "private" (without a direct route to the Internet Gateway) for resources that should remain isolated. For IoT, backend services often reside in private subnets. * **Internet Gateway (IGW):** Enables communication between your VPC and the internet. Public subnets route traffic through an IGW. * **NAT Gateway/NAT Instance:** Allows instances in a private subnet to initiate outbound connections to the internet (e.g., for software updates) while preventing inbound connections from the internet. * **Security Groups:** Act as virtual firewalls at the instance level, controlling inbound and outbound traffic for specific EC2 instances or other resources. * **Network Access Control Lists (Network ACLs):** Operate at the subnet level, providing stateless packet filtering for all traffic entering or leaving a subnet. * **VPC Endpoints:** Allow private connectivity to AWS services (like S3, DynamoDB, or AWS IoT Core) from within your VPC, without requiring traffic to traverse the public internet. This significantly enhances security and reduces latency. By leveraging these components, you can create a highly customized and secure network architecture that perfectly fits the unique demands of your remote IoT solution. It's the foundational layer that ensures your remote devices communicate with your backend systems in a controlled, private, and secure manner.Architecting Your RemoteIoT VPC Network on AWS
Designing a remoteiot vpc network aws requires careful consideration of security, scalability, and the specific communication patterns of your IoT devices. The goal is to create an environment where devices can securely connect, send data, and receive commands, while minimizing exposure to external threats. A common architectural pattern involves separating your network into public and private subnets. IoT devices typically connect to AWS IoT Core endpoints, which can be publicly accessible. However, the backend services that process and store this data (e.g., Lambda functions, EC2 instances, databases like DynamoDB or RDS) should ideally reside in private subnets. This ensures that these critical resources are not directly exposed to the internet. Connectivity options for your backend services within the VPC include: * **AWS IoT Core Endpoints:** Your devices will primarily communicate with AWS IoT Core via MQTT, HTTPS, or LoRaWAN. AWS IoT Core acts as the ingestion point for device data, and it is designed to handle billions of messages securely. * **VPC Endpoints for AWS Services:** For your backend services within the VPC to interact with other AWS services (like S3 for data storage, Lambda for processing, or DynamoDB for data persistence), it's best practice to use VPC Endpoints. These endpoints create a private connection between your VPC and the target AWS service, bypassing the public internet entirely. This significantly reduces the attack surface and improves data transfer performance. * **VPN or Direct Connect:** If your IoT devices are part of an on-premises network that needs to communicate directly with resources in your VPC (e.g., for device management or firmware updates), you can establish a secure VPN connection (IPsec VPN) or a dedicated network connection (AWS Direct Connect) between your on-premises network and your VPC. ###Secure Device Onboarding and Authentication
One of the most critical aspects of any remote IoT deployment is the secure onboarding and authentication of devices. Each device must be uniquely identified and authorized to communicate with your AWS IoT Core endpoints. AWS IoT Core provides robust mechanisms for this: * **X.509 Certificates:** Devices are typically provisioned with unique X.509 client certificates. These certificates, combined with private keys, are used for mutual TLS (mTLS) authentication with AWS IoT Core. This ensures that both the device and the service verify each other's identity before any data exchange occurs. * **AWS IoT Policies:** You define fine-grained policies that specify what actions a device is permitted to perform (e.g., publish to specific MQTT topics, subscribe to others, receive shadow updates). These policies are attached to the device's certificate. * **Just-in-Time Registration (JITR) / Just-in-Time Provisioning (JITP):** For large-scale deployments, JITR/JITP simplifies the onboarding process. Devices can be pre-provisioned with a client certificate signed by a Certificate Authority (CA) that you register with AWS IoT. When a device connects for the first time, AWS IoT automatically registers the device and attaches a pre-defined policy, streamlining the process and reducing manual intervention. This lowers the barrier to entry for large-scale device deployment, much like how a flight simulator can simplify learning to fly with minimal requirements. ###Data Ingress and Egress Strategies
Once devices are securely connected, managing the flow of data is paramount. * **Data Ingress:** Device data typically flows into AWS IoT Core via MQTT messages or HTTPS requests. From IoT Core, the Rules Engine takes over. The Rules Engine allows you to define rules that process, filter, and route messages to other AWS services. For example, a rule might send sensor data to an S3 bucket for storage, trigger a Lambda function for real-time processing, or insert data into a DynamoDB table. By using VPC Endpoints, these backend services within your VPC can receive data from IoT Core securely and privately, without traversing the public internet. This ensures that your sensitive IoT data remains within your private network perimeter as much as possible. * **Data Egress:** While most IoT data flows from devices *into* the cloud, there are scenarios where data needs to flow *out* from your VPC to external systems or dashboards. This could involve sending processed data to a third-party analytics platform, generating reports, or pushing notifications. For controlled egress, you would use NAT Gateways in public subnets, or secure VPN/Direct Connect connections to on-premises systems. For services within your VPC that need to access the internet (e.g., to fetch firmware updates for devices), a NAT Gateway in a public subnet allows outbound connections while preventing unsolicited inbound connections, maintaining the security of your private resources.Enhancing Security and Compliance in Your IoT VPC
Security is not a feature; it's a continuous process, especially when dealing with distributed IoT devices. A remoteiot vpc network aws provides a robust foundation, but true security requires a multi-layered approach. * **Granular Traffic Control:** Leverage Security Groups and Network ACLs meticulously. Security Groups operate at the instance level, allowing you to define rules for specific resources (e.g., only allow traffic on port 8883 for MQTT to your IoT Core endpoint, or restrict SSH access to specific IP ranges). Network ACLs provide an additional, stateless layer of defense at the subnet level, useful for broad traffic filtering. * **DDoS Protection:** AWS Shield Standard is automatically included for all AWS customers, providing basic protection against common DDoS attacks. For higher levels of protection, especially for critical IoT applications, AWS Shield Advanced offers enhanced detection and mitigation capabilities. AWS WAF (Web Application Firewall) can protect web applications and APIs (like those exposed by your backend services) from common web exploits. * **Monitoring and Logging:** Visibility is key to security. AWS CloudTrail logs all API calls made to your AWS account, providing an audit trail of actions taken. AWS CloudWatch monitors your AWS resources and applications, allowing you to collect and track metrics, collect and monitor log files, and set alarms. For network-level insights, VPC Flow Logs capture information about the IP traffic going to and from network interfaces in your VPC. Analyzing these logs can help detect anomalies, troubleshoot connectivity issues, and identify potential security threats. This is akin to a "live map showing all pilots currently flying" in a flight simulator, giving you real-time visibility into your network's activity. * **Compliance Considerations:** Depending on your industry and the type of data your IoT devices handle, compliance with regulations like GDPR, HIPAA, or industry-specific standards (e.g., ISA/IEC 62443 for industrial control systems) is paramount. AWS provides a secure and compliant environment, but it's your responsibility to ensure your application architecture and data handling practices within your VPC meet these requirements. This includes data encryption at rest and in transit, access control, and data retention policies. By carefully architecting your VPC and adhering to AWS best practices, you can significantly lower the barrier to entry for achieving compliance in complex IoT deployments.Scalability and Resilience for Global RemoteIoT Deployments
The promise of IoT often involves massive deployments spanning diverse geographical locations, requiring a network that can scale horizontally and remain resilient in the face of failures. A remoteiot vpc network aws is inherently designed for this. * **High Availability (Multi-AZ):** AWS regions are composed of multiple Availability Zones (AZs), which are isolated locations within a region. By distributing your resources (e.g., EC2 instances, databases) across multiple AZs within your VPC, you can design highly available applications that can withstand the failure of an entire AZ. If one AZ experiences an outage, your application can seamlessly failover to resources in another AZ. * **Auto Scaling:** For backend services processing IoT data, AWS Auto Scaling groups can automatically adjust the number of EC2 instances in response to demand. This ensures that your application can handle spikes in data ingestion from devices without performance degradation, and scale down during periods of low activity to optimize costs. * **Global IoT Deployments:** AWS IoT Core is a global service, meaning devices can connect to the nearest AWS IoT endpoint, and rules can process data and route it to services in any AWS region. This global reach, much like a flight simulator that uses "worldwide satellite images" and allows you to "fly in the world," enables you to manage IoT devices and data streams across continents efficiently. You can centralize your data processing in a single region or distribute it across multiple regions for lower latency and improved resilience. * **Data Consistency and Replication:** For critical IoT data, consider using services like Amazon DynamoDB Global Tables for multi-region replication, ensuring high availability and low-latency access to your data from anywhere in the world. AWS S3 also offers cross-region replication for robust data backup and disaster recovery. By leveraging these capabilities, you can build a remote IoT solution that is not only secure and performant but also capable of growing with your business, handling millions or even billions of devices and data points without breaking a sweat.Advanced RemoteIoT Use Cases and Best Practices
Beyond basic connectivity and data ingestion, a well-architected remoteiot vpc network aws opens the door to more sophisticated IoT applications and operational efficiencies. * **Edge Computing with AWS IoT Greengrass:** For scenarios requiring low-latency processing, offline capabilities, or local decision-making, AWS IoT Greengrass extends AWS cloud capabilities to edge devices. Greengrass devices can run Lambda functions, manage local data, and communicate with other devices locally, all while securely interacting with AWS IoT Core. Integrating Greengrass with your VPC allows for secure communication between edge deployments and your cloud backend, ensuring that your edge devices can seamlessly push aggregated data or receive new configurations. * **Digital Twins and Simulation Environments:** The ability to simulate real-world environments and device behavior is invaluable for testing, training, and predictive maintenance. AWS IoT TwinMaker allows you to create digital twins of real-world systems, and you can integrate this with your VPC to pull data from connected devices and visualize their operational state. This is akin to a "realistic flight simulation experience" where you can model and test complex scenarios without impacting live operations. You can even use these simulations as a "training tool in education" or for "flying schools" for your operational staff. * **Data Analytics Pipelines:** The true value of IoT lies in the insights derived from the data. Your VPC can host a powerful data analytics pipeline using services like Amazon Kinesis for real-time stream processing, AWS Lambda for serverless data transformation, Amazon S3 for data lake storage, and Amazon Athena or Amazon Redshift for querying and analysis. This allows you to turn raw device data into actionable intelligence, driving business decisions and operational improvements. ###Monitoring and Troubleshooting Your RemoteIoT VPC
Maintaining the health and performance of your remote IoT network is crucial. AWS provides a suite of tools for comprehensive monitoring and troubleshooting: * **Amazon CloudWatch:** This service is your primary tool for monitoring. You can collect metrics on network traffic (bytes in/out for EC2 instances, NAT Gateways), CPU utilization, and memory usage for your backend services. CloudWatch Logs can centralize logs from all your services, making it easy to search, filter, and analyze operational data. You can set up alarms to notify you of critical events, such as high latency or network errors. This proactive monitoring helps "troubleshoot issues and performance problems" before they escalate. * **VPC Flow Logs:** These logs capture detailed information about IP traffic flowing to and from network interfaces in your VPC. You can publish flow logs to Amazon CloudWatch Logs or Amazon S3. Analyzing flow logs helps identify unusual traffic patterns, diagnose connectivity issues between instances, and ensure that your Security Group and Network ACL rules are functioning as intended. * **AWS X-Ray:** For understanding the performance of your distributed applications that process IoT data, X-Ray helps trace requests as they travel through your services, identifying bottlenecks and performance issues across your entire architecture. ###Cost Optimization Strategies for Your IoT VPC
While security and performance are paramount, managing costs effectively is also a key consideration for any large-scale remoteiot vpc network aws. * **Right-Sizing Resources:** Continuously monitor your resource utilization (EC2 instances, databases, Lambda concurrency) and right-size them to match your actual workload. Avoid over-provisioning. * **Optimizing Data Transfer Costs:** Data transfer costs can accumulate, especially for large IoT deployments. Leverage VPC Endpoints to keep traffic within the AWS network where possible, reducing egress costs to the public internet. Optimize data formats (e.g., using binary formats like Protobuf instead of verbose JSON) to minimize data volume. * **Reserved Instances and Savings Plans:** For stable, predictable workloads, consider purchasing EC2 Reserved Instances or Savings Plans, which offer significant discounts compared to On-Demand pricing. * **Lifecycle Management for S3:** For IoT data stored in S3, implement lifecycle policies to automatically transition older, less frequently accessed data to lower-cost storage classes (like S3 Infrequent Access or S3 Glacier) or delete it after a defined period. * **Monitor Spend with AWS Cost Explorer:** Regularly review your AWS bill and use AWS Cost Explorer to analyze your spending patterns, identify cost drivers, and pinpoint areas for optimization.The E-E-A-T and YMYL Perspective on RemoteIoT VPC Networks
When it comes to architecting a remoteiot vpc network aws, the principles of E-E-A-T (Expertise, Authoritativeness, Trustworthiness) and YMYL (Your Money or Your Life) are not just theoretical guidelines but practical necessities. **Expertise:** Building a secure and scalable IoT solution on AWS requires deep technical expertise. This isn't a task for novices. Professionals involved must possess a thorough understanding of networking fundamentals, cloud security best practices, AWS IoT services, and the intricacies of VPC configuration. Misconfigurations can lead to severe vulnerabilities, data breaches, or operational downtime. Relying on certified AWS solution architects and engineers ensures that the network is designed with a deep understanding of potential pitfalls and optimal solutions. **Authoritativeness:** The information and practices applied must come from authoritative sources. For AWS environments, this primarily means adhering to AWS's own well-architected framework, security best practices, and official documentation. Solutions should be built on proven patterns and industry standards, not experimental or unverified methods. An authoritative approach ensures that the network is robust, reliable, and compliant with recognized benchmarks. **Trustworthiness:** A secure IoT network fosters trust. For businesses, this means trust from customers whose data is handled, from partners relying on your services, and from internal stakeholders whose operations depend on reliable IoT data. A compromised IoT network can severely damage a company's reputation, leading to customer churn, legal liabilities, and significant financial losses. Demonstrating trustworthiness through a meticulously secured VPC network is paramount. **YMYL (Your Money or Your Life):** The implications of a poorly secured or designed remote IoT VPC network can directly impact "Your Money or Your Life." * **Your Money:** * **Financial Loss:** Data breaches can lead to massive fines (e.g., GDPR violations), legal costs, and remediation expenses. Downtime in industrial IoT can halt production, resulting in millions in lost revenue. * **Operational Disruption:** A compromised network can lead to critical systems failing, disrupting supply chains, logistics, or essential services. * **Reputational Damage:** Loss of customer trust due to security incidents can have long-term financial repercussions, affecting brand loyalty and market share. * **Your Life:** * **Physical Safety:** In domains like healthcare (e.g., remote patient monitoring, connected medical devices) or industrial control systems (e.g., smart factories, autonomous vehicles), a compromised IoT network can directly endanger human lives. Malicious actors could manipulate devices, leading to accidents, system failures, or even direct harm. * **Privacy Violations:** IoT devices often collect highly personal and sensitive data. Breaches can expose private information, leading to identity theft, blackmail, or severe privacy violations that impact individuals' well-being. Therefore, the design, implementation, and continuous management of a remote IoT VPC network on AWS must be approached with the utmost diligence, recognizing its profound impact on financial stability, operational continuity, and, most critically, human safety and privacy. It's not just about connecting devices; it's about safeguarding livelihoods.Conclusion
The journey to harness the full potential of the Internet of Things is inextricably linked to building a secure, scalable, and resilient network foundation. A remoteiot vpc network aws offers precisely this, providing an isolated, highly controllable, and flexible environment within the cloud to manage your diverse and geographically dispersed IoT devices. From secure device onboarding and robust data ingress/egress strategies to multi-layered security controls and global scalability, AWS VPC empowers organizations to deploy and manage their IoT solutions with confidence. By meticulously architecting your VPC, leveraging AWS IoT Core, and implementing best practices for security, monitoring, and cost optimization, you can transform the challenges of remote IoT into opportunities for innovation and efficiency. The principles of E-E-A-T and YMYL underscore the critical importance of this endeavor, emphasizing that a well-designed IoT network is not merely a technical achievement but a safeguard for financial stability, operational integrity, and human well-being. As you embark on or continue your IoT journey, remember that the network is the backbone. Invest in a robust remoteiot vpc network awsRelated Resources:


Detail Author:
- Name : Lue Haag
- Username : lang.garth
- Email : charles.runte@yahoo.com
- Birthdate : 1982-12-17
- Address : 9934 Ford Radial Apt. 552 Lake Jacquesborough, KS 46991-7591
- Phone : 801-874-9047
- Company : Volkman-Quitzon
- Job : Medical Equipment Repairer
- Bio : Rerum ut explicabo quisquam omnis. Exercitationem numquam velit ut sint distinctio ut. Autem eos consectetur ullam in quia autem. Itaque totam ullam qui quod rerum perferendis odit sapiente.
Socials
twitter:
- url : https://twitter.com/magdalena_stehr
- username : magdalena_stehr
- bio : Dolores molestiae architecto aut consequatur. Quas voluptate natus consequatur enim nostrum vitae. Officiis aliquam soluta tempore.
- followers : 2704
- following : 210
instagram:
- url : https://instagram.com/stehrm
- username : stehrm
- bio : Omnis ipsum harum tempore. Reiciendis earum impedit veniam sint porro optio quia.
- followers : 544
- following : 187
tiktok:
- url : https://tiktok.com/@magdalena5014
- username : magdalena5014
- bio : Adipisci recusandae sit quaerat quia.
- followers : 1053
- following : 68