In today's interconnected world, the ability to seamlessly and securely connect remote IoT devices to your AWS Virtual Private Cloud (VPC) is not just a convenience, but a fundamental requirement for many businesses. However, it's a common scenario for engineers and developers to exclaim, "My attempt to securely connect remote IoT VPC AWS not working!" This frustration often stems from the intricate interplay of networking, security, and IoT-specific configurations within the AWS ecosystem.
This comprehensive guide aims to demystify the complexities involved in establishing robust and secure IoT connectivity to your AWS VPC. We'll delve into common pitfalls, explore essential components, and provide actionable troubleshooting steps to help you diagnose and resolve connectivity issues, ensuring your remote IoT infrastructure operates flawlessly and securely.
Table of Contents
- Understanding the "Securely Connect Remote IoT VPC AWS Not Working" Conundrum
- Core Components of Secure Remote IoT Connectivity to AWS VPC
- Initial Diagnostic Steps: Is Your Network Even Reaching AWS?
- Deep Dive into AWS VPC Networking for IoT
- AWS IoT Core Configuration & Device Identity
- Advanced Troubleshooting: Beyond the Basics
- Best Practices for Robust & Secure IoT-VPC Connectivity
- When All Else Fails: Seeking AWS Support & Community Help
Understanding the "Securely Connect Remote IoT VPC AWS Not Working" Conundrum
The phrase "securely connect remote IoT VPC AWS not working" encapsulates a broad spectrum of issues, from network misconfigurations to incorrect security policies or even device-level problems. The inherent complexity arises because IoT deployments often involve diverse hardware, varied network conditions (cellular, Wi-Fi, satellite), and the need for stringent security across the entire data path. When connectivity fails, it can lead to data loss, operational downtime, and significant business impact. The stakes are high. Unsecured IoT devices are prime targets for cyberattacks, potentially compromising sensitive data, enabling unauthorized access to internal networks, or even being co-opted into botnets. Therefore, ensuring not just connectivity, but *secure* connectivity, is paramount. This guide will help you systematically break down the problem, identify the root cause, and implement effective solutions to get your remote IoT devices communicating securely with your AWS VPC.Core Components of Secure Remote IoT Connectivity to AWS VPC
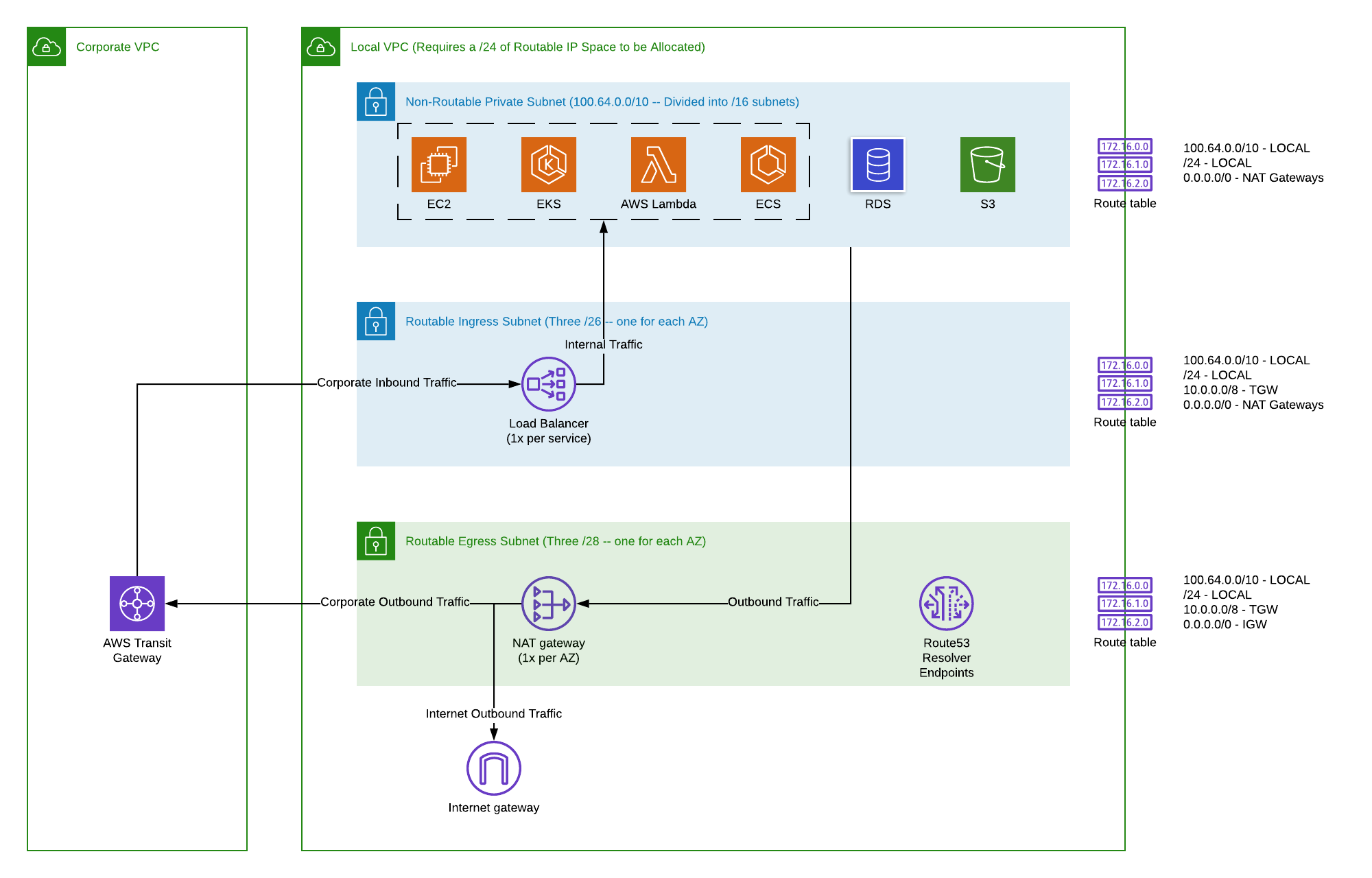
Before diving into troubleshooting, it's crucial to understand the fundamental AWS services and networking concepts that underpin secure remote IoT connectivity. A misconfiguration in any of these layers can lead to the dreaded "securely connect remote IoT VPC AWS not working" error.- AWS IoT Core: This is the central hub for managing your IoT devices, ingesting data, and enabling communication. It handles device authentication, authorization, message routing, and device shadow management.
- AWS Virtual Private Cloud (VPC): Your isolated virtual network in AWS where you launch AWS resources. It's crucial for housing backend services that process IoT data, such as EC2 instances, Lambda functions, or databases.
- Network Connectivity Options:
- AWS Site-to-Site VPN: Establishes an encrypted tunnel between your remote IoT gateway (or a network device at your remote site) and your AWS VPC. Ideal for connecting on-premises networks or remote locations with a static IP.
- AWS Direct Connect: Provides a dedicated, private network connection from your premises to AWS. Offers higher bandwidth and lower latency than VPN, suitable for large-scale deployments or mission-critical applications.
- AWS Transit Gateway: A network hub that connects your VPCs and on-premises networks through a central gateway. Simplifies network management, especially for complex architectures with many VPCs and remote sites.
- Public Internet (with TLS/SSL): For devices that connect directly to AWS IoT Core endpoints over the public internet, TLS/SSL is critical for encryption. While simpler, it relies on public routing and might not be suitable for sensitive data or strict compliance needs without additional layers of security.
- Security Mechanisms:
- Security Groups: Act as virtual firewalls for EC2 instances and other resources within your VPC, controlling inbound and outbound traffic at the instance level.
- Network Access Control Lists (NACLs): Stateless firewalls for subnets within your VPC, providing an additional layer of security.
- AWS Identity and Access Management (IAM): Manages access to AWS resources. Crucial for defining permissions for IoT devices, users, and backend services.
- Device Certificates & Policies: X.509 certificates are used for device authentication with AWS IoT Core, and IoT policies define what actions a device is authorized to perform (e.g., publish to specific topics, subscribe to others).
Initial Diagnostic Steps: Is Your Network Even Reaching AWS?
When you find that you "securely connect remote IoT VPC AWS not working," the very first step is to ascertain whether there's any network path from your remote IoT device or gateway to your AWS environment. This isn't about AWS IoT Core yet; it's about fundamental network reachability.- Ping/Traceroute from Remote IoT Device/Gateway:
- Attempt to ping a known public AWS endpoint (e.g., `ping data.iot.us-east-1.amazonaws.com`). This verifies basic internet connectivity from your device.
- If you're using a VPN or Direct Connect, try pinging an EC2 instance or an internal IP address within your AWS VPC. This confirms the tunnel or direct connection is up and routing traffic.
- Use `traceroute` (or `tracert` on Windows) to see the path the packets take. This can reveal where the connection is dropping or encountering delays.
- Checking Local Firewall Rules:
- Ensure that any local firewalls on your remote IoT device, gateway, or local network are not blocking outbound connections on the necessary ports (e.g., MQTT over TLS uses port 8883, HTTPS uses 443).
- Verify that your network's NAT (Network Address Translation) configuration is correct if your devices are behind a NAT device.
Verifying VPN/Direct Connect Status
If your architecture relies on a VPN or Direct Connect, these are critical points of failure.- AWS Management Console: Navigate to the VPC service in the AWS console.
- For Site-to-Site VPN: Check the "Site-to-Site VPN connections" section. Ensure both tunnels are "UP" and showing healthy status. Look for BGP status if you're using dynamic routing.
- For Direct Connect: Check "Direct Connect connections" and "Virtual Interfaces." Ensure the connection is "Available" and the VIFs are "Up."
- On-Premises/Remote Device Configuration: Verify that your customer gateway device (for VPN) or router (for Direct Connect) is correctly configured, has the right IP addresses, shared secrets, and routing protocols (e.g., BGP) established. Mismatched configurations are a very common reason for VPN tunnels failing to establish or pass traffic.
- Route Propagation: Ensure that routes from your remote network are correctly propagated into your AWS VPC route tables (if using dynamic routing) or manually added if using static routes. Conversely, ensure your VPC routes are advertised back to your remote network.
Deep Dive into AWS VPC Networking for IoT
Once basic network reachability is confirmed, the next layer of investigation when you find that you "securely connect remote IoT VPC AWS not working" moves to your AWS VPC configuration itself.- Route Tables: Ensuring Paths to IoT Devices:
- Every subnet in your VPC is associated with a route table. Ensure that the route tables associated with the subnets where your backend services reside (e.g., EC2 instances processing IoT data) have routes pointing back to your remote IoT devices/network via your VPN, Direct Connect, or Transit Gateway.
- If your IoT devices connect directly to AWS IoT Core over the public internet, ensure your VPC's internet gateway (IGW) is correctly configured and route tables direct outbound internet traffic through it.
- Security Groups: Inbound/Outbound Rules for IoT Traffic:
- Security groups are stateful, instance-level firewalls. If your IoT devices are trying to connect to an EC2 instance or an internal service within your VPC, ensure the security group attached to that resource allows inbound traffic on the necessary ports (e.g., 8883 for MQTT, 443 for HTTPS) from the IP range of your remote IoT devices or your VPN/Direct Connect gateway.
- Also, check outbound rules from your backend services if they need to initiate connections back to your IoT devices (less common for IoT Core-centric architectures but relevant for direct device-to-server communication).
- Network ACLs: Stateless Filtering at Subnet Level:
- NACLs are stateless, meaning they must explicitly allow both inbound and outbound traffic. If you have custom NACLs, verify that they permit traffic on the required ports (e.g., 8883, 443) from/to your remote IoT network or the public internet.
- Remember to allow ephemeral ports (1024-65535) for return traffic if your devices are initiating connections. This is a common oversight.
VPC Endpoints for AWS IoT Core
For enhanced security and privacy, especially when your backend services within a VPC need to interact with AWS IoT Core without traversing the public internet, VPC Endpoints are invaluable. If your setup includes these, they become a critical troubleshooting point.- Why Use Them? Private Connectivity: VPC Endpoints (specifically, interface endpoints powered by AWS PrivateLink) allow your VPC to privately connect to AWS IoT Core services. This keeps traffic within the AWS network, reducing exposure to the public internet.
- Troubleshooting Endpoint Policies:
- When creating a VPC endpoint, you can attach an endpoint policy that controls which IAM principals can use the endpoint to access the service. Ensure this policy grants the necessary permissions to your IoT devices (if they are connecting via the endpoint) or your backend services.
- Verify that the security groups associated with the VPC endpoint allow inbound traffic from your backend services' security groups or your remote IoT network's IP range.
- Check the DNS resolution within your VPC. If you're using private DNS for the endpoint, ensure it's resolving correctly to the private IP addresses of the endpoint.
AWS IoT Core Configuration & Device Identity
Even if your network path is perfect, issues within AWS IoT Core's configuration or device identity management can cause your "securely connect remote IoT VPC AWS not working" problem. This layer deals with how devices authenticate and authorize with the IoT platform.- Device Certificates & Policies: Common Pitfalls:
- Incorrect Certificate: Ensure the device is using the correct X.509 certificate and private key that was registered with AWS IoT Core. A mismatch will lead to authentication failure.
- Expired Certificate: Certificates have validity periods. An expired certificate will prevent connection.
- Incorrect Root CA: Devices need the correct Amazon Root CA certificate to establish a trust chain with AWS IoT Core. Ensure the correct CA is installed on the device.
- Mismatched Client ID: The client ID used by the device when connecting must match the client ID specified in its IoT policy or be allowed by a wildcard in the policy.
- Restrictive IoT Policy: The IoT policy attached to the device's certificate (or thing) defines what actions the device can perform (e.g., `iot:Connect`, `iot:Publish`, `iot:Subscribe`, `iot:Receive`). If the policy is too restrictive, the device might connect but fail to publish or subscribe, giving the impression of a general connectivity issue. For example, if `iot:Connect` is denied, the device won't even establish a session.
- Active/Inactive Certificates: In the AWS IoT console, ensure the device certificate status is "ACTIVE."
- IoT Rules Engine: Ensuring Data Flow:
- While not directly a "connection" issue, if devices connect but data doesn't appear in your backend, the IoT Rules Engine might be misconfigured.
- Check the SQL query in your rules to ensure it's correctly selecting messages.
- Verify the rule's action (e.g., sending to S3, Lambda, DynamoDB) has the correct permissions (IAM role) and target configuration.
- Monitor CloudWatch metrics for your rules (e.g., `MessagesSent`, `Errors`).
- Device Shadow & Registry: Correct Registration:
- Ensure your "Things" are correctly registered in the AWS IoT registry.
- If using Device Shadow, verify that the device is attempting to update/retrieve the correct shadow name.
IAM Roles and Policies for IoT Interactions
IAM is the backbone of security in AWS. Incorrect IAM permissions are a frequent cause of the "securely connect remote IoT VPC AWS not working" error, especially when backend services are involved.- Permissions for Devices: As mentioned, IoT policies attached to certificates govern device permissions. These are essentially IAM policies tailored for IoT actions.
- Permissions for Backend Services:
- If your Lambda functions, EC2 instances, or other AWS services need to interact with AWS IoT Core (e.g., publishing messages, updating shadows, listing things), ensure their associated IAM roles have the necessary permissions (e.g., `iot:Publish`, `iot:UpdateThingShadow`, `iot:ListThings`).
- For IoT rules that invoke other AWS services (e.g., Lambda, Kinesis, S3), the IAM role assigned to the rule must have permissions to perform those actions on the target service.
- Permissions for Users/Administrators: Ensure that the IAM users or roles you are using to configure and manage AWS IoT and networking resources have the necessary permissions to view, create, and modify these resources.
Advanced Troubleshooting: Beyond the Basics
When the standard checks don't reveal the culprit behind your "securely connect remote IoT VPC AWS not working" issue, it's time to dig deeper with advanced logging and monitoring tools.- CloudWatch Logs & Metrics: Monitoring Connection Attempts and Failures:
- AWS IoT Core Logs: Configure AWS IoT Core to send connection and authentication logs to CloudWatch Logs. Look for entries indicating connection attempts, disconnections, authentication failures, or authorization errors. These logs are invaluable for pinpointing whether the issue is with the device's credentials, policy, or network.
- VPC Flow Logs: Enable VPC Flow Logs for your VPC, subnets, or network interfaces. Flow Logs capture information about IP traffic going to and from network interfaces in your VPC. Analyze these logs in CloudWatch Logs Insights or export them to S3/Athena to identify if traffic from your remote IoT devices is even reaching your VPC, and if so, whether it's being accepted or rejected by security groups/NACLs.
- VPN/Direct Connect Metrics: CloudWatch provides metrics for VPN tunnels and Direct Connect connections, showing data transfer, tunnel state, and BGP status. Monitor these for any anomalies.
- Lambda/EC2 Logs: If your IoT data is supposed to trigger Lambda functions or be processed by EC2 instances, check their respective CloudWatch Logs for application-level errors or if they are even receiving the expected input.
- Packet Capture (if possible on device/gateway):
- If you have access to the remote IoT gateway or a network device along the path, performing a packet capture (e.g., using Wireshark or tcpdump) can provide granular insight into the network traffic.
- Look for SYN/ACK handshakes, TLS negotiation failures, or explicit rejections. This can confirm if packets are being sent, received, or dropped at a specific point.
- Network Analyzer Tools:
- For complex VPC setups, AWS Network Access Analyzer can help identify unintended network access paths.
- AWS Reachability Analyzer can test reachability between a source and destination resource within your VPCs or between your VPCs and on-premises networks, helping to validate your network configurations.
Best Practices for Robust & Secure IoT-VPC Connectivity
Preventing the "securely connect remote IoT VPC AWS not working" scenario is always better than troubleshooting it. Adhering to best practices significantly enhances the reliability and security of your IoT solution.- Least Privilege Principle: Grant only the necessary permissions to devices, users, and roles. For IoT devices, their policies should only allow them to publish/subscribe to specific topics, not broad wildcards.
- Automated Deployment & Configuration Management: Use Infrastructure as Code (IaC) tools like AWS CloudFormation or Terraform to define and deploy your VPC, IoT Core resources, and security configurations. This ensures consistency, reduces human error, and makes changes auditable.
- Regular Security Audits: Periodically review your IoT policies, security group rules, NACLs, and IAM roles. Look for overly permissive rules or unused resources that could pose a security risk. Utilize AWS Config and AWS Security Hub for continuous monitoring.
- Redundancy and High Availability:
- For VPNs, configure redundant tunnels to different AWS VPN endpoints.
- For Direct Connect, consider multiple connections to different locations or partners.
- Design your backend services within your VPC across multiple Availability Zones (AZs) to ensure resilience.
- Implement retry mechanisms and exponential backoff in your device firmware for connection attempts to AWS IoT Core.
- Centralized Logging and Monitoring: Ensure all relevant logs (IoT Core, VPC Flow, Lambda, EC2) are aggregated in CloudWatch Logs and that alarms are set up for critical metrics (e.g., connection failures, unauthorized attempts, high latency).
- Certificate Rotation Strategy: Plan for regular rotation of device certificates to enhance security and mitigate risks associated with compromised credentials.
- Use VPC Endpoints for Private Connectivity: Whenever possible, use VPC Endpoints for private communication between your VPC resources and AWS IoT Core, eliminating exposure to the public internet.
When All Else Fails: Seeking AWS Support & Community Help
Even with the best practices and troubleshooting guides, there might be times when you still face the "securely connect remote IoT VPC AWS not working" issue. Don't hesitate to leverage AWS support or the broader community.- Gathering Diagnostic Data: Before reaching out, compile all the information you've gathered:
- Error messages from device logs, CloudWatch Logs (IoT Core, Flow Logs, Lambda, EC2).
- Configuration details of your VPC (CIDR blocks, subnets, route tables, security groups, NACLs).
- VPN/Direct Connect configuration (tunnel status, BGP, customer gateway config).
- AWS IoT Core configurations (Thing names, certificate IDs, IoT policies, rules).
- Traceroute results from the device to AWS.
- Any changes made recently to the environment.
- Formulating Clear Support Requests:
- If you have an AWS Support plan, open a detailed support case. Clearly describe the problem, the steps you've already taken, and provide all relevant diagnostic data.
- For community help (e.g., AWS re:Post, Stack Overflow, Reddit), provide a concise problem description, your architecture diagram (if possible), and the specific error messages or observed behavior. Avoid sharing sensitive information.
Conclusion
The challenge of "securely connect remote IoT VPC AWS not working" is a common hurdle, but one that can be overcome with a systematic approach to troubleshooting and a solid understanding of AWS networking, security, and IoT Core services. We've explored the critical components, walked through initial and advanced diagnostic steps, and highlighted best practices to ensure your remote IoT devices connect securely and reliably to your AWS VPC. By meticulously checking network reachability, VPC configurations (route tables, security groups, NACLs, VPC Endpoints), and AWS IoT Core settings (device certificates, policies, IAM roles), you can pinpoint and resolve most connectivity issues. Remember to leverage AWS's powerful logging and monitoring tools like CloudWatch and VPC Flow Logs for deeper insights. Implementing robust security practices and designing for high availability from the outset will significantly reduce future headaches. If you've encountered similar issues or have specific solutions that worked for you, please share your experiences in the comments below. Your insights can help the wider community debug and deploy more resilient IoT solutions. For further reading, explore the official AWS documentation on IoT Core, VPC, and various networking services. Happy connecting!Related Resources:


Detail Author:
- Name : Dr. Dandre O'Conner
- Username : kilback.felicita
- Email : dino.conn@ryan.com
- Birthdate : 1977-07-21
- Address : 5409 Tromp Knolls New Destineyville, ME 40236
- Phone : 614.560.6109
- Company : Gutmann Ltd
- Job : Scientific Photographer
- Bio : Eius eveniet facilis non esse. Ut necessitatibus dolores architecto accusantium et dolores. Consequatur reprehenderit culpa veritatis error laborum ex exercitationem et.
Socials
tiktok:
- url : https://tiktok.com/@tomas.conroy
- username : tomas.conroy
- bio : Ut explicabo perspiciatis animi. Ea sequi sint iure soluta.
- followers : 1542
- following : 1646
linkedin:
- url : https://linkedin.com/in/tomas_conroy
- username : tomas_conroy
- bio : Eum dicta est soluta.
- followers : 4522
- following : 2170