In an increasingly interconnected world, the Internet of Things (IoT) has seamlessly woven itself into the fabric of our daily lives, from smart thermostats and security cameras to wearable health monitors and connected appliances. While these devices offer unparalleled convenience and efficiency, their rapid proliferation has also introduced a complex web of security challenges. Protecting these myriad smart devices from cyber threats is no longer a luxury but a fundamental necessity, and at the forefront of this defense is the often-underestimated yet critically important IoT device firewall.
Understanding the critical role of a firewall in safeguarding your smart home or business network is paramount. Just as a traditional firewall protects your computer from malicious attacks, an IoT device firewall acts as a digital gatekeeper, meticulously controlling the flow of data to and from your connected gadgets. Without this vital layer of protection, your smart devices, and by extension, your personal data and privacy, remain vulnerable to a wide array of cyber risks, ranging from data breaches and unauthorized access to complete system compromise and even physical harm in some industrial IoT scenarios.
Table of Contents
- Understanding the IoT Landscape and Its Vulnerabilities
- What Exactly is an IoT Device Firewall?
- Why Your Smart Devices Desperately Need a Firewall
- Types of IoT Firewall Implementations
- Key Features of an Effective IoT Firewall
- Best Practices for Implementing and Managing IoT Firewalls
- Overcoming Challenges in IoT Firewall Deployment
- The Future of IoT Security and Firewalls
Understanding the IoT Landscape and Its Vulnerabilities
The sheer volume and diversity of IoT devices present a unique challenge for cybersecurity. Unlike traditional computing devices, many IoT gadgets are designed for convenience and cost-effectiveness, often at the expense of robust security features. This inherent vulnerability makes them attractive targets for cybercriminals.The Proliferation of Connected Devices
From smart refrigerators that order groceries to sophisticated industrial sensors monitoring critical infrastructure, IoT devices are everywhere. Each new device added to a network represents a potential entry point for attackers. A single compromised smart bulb, for instance, could potentially be used as a stepping stone to access more sensitive parts of your home network. The rapid growth of this ecosystem means that security measures must evolve just as quickly. Industry reports suggest that billions of IoT devices are currently active globally, with projections indicating exponential growth in the coming years. This vast attack surface underscores the urgent need for comprehensive protection, with a robust **IoT device firewall** being a cornerstone.Common IoT Security Gaps
Many IoT devices suffer from fundamental security weaknesses. These often include:- Default Passwords: Many devices ship with easily guessable or hardcoded default credentials that users rarely change.
- Lack of Updates: Manufacturers often fail to provide timely security updates, leaving known vulnerabilities unpatched.
- Insecure Communication: Data transmitted by devices may not be encrypted, making it susceptible to interception.
- Limited Processing Power: Small, low-power devices may not have the capacity for complex encryption or security protocols.
- Poorly Designed APIs: Application Programming Interfaces (APIs) used for device communication can have flaws that expose data.
What Exactly is an IoT Device Firewall?
At its core, an IoT device firewall is a security system that monitors and controls incoming and outgoing network traffic for your connected devices based on predetermined security rules. Think of it as a digital bouncer, deciding which data packets are allowed in or out of your IoT network. It operates by analyzing the source and destination of data, the type of data, and the ports being used, then applying rules to either permit or deny the connection.Beyond Traditional Firewalls
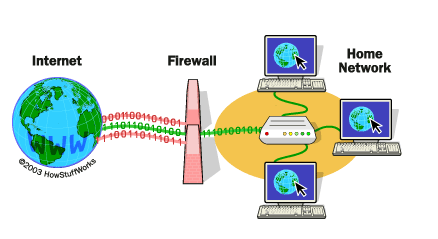
While the concept of a firewall is familiar from personal computers (like the Windows Firewall), an IoT device firewall has unique considerations. Traditional firewalls, like Microsoft Defender Firewall on Windows 10/11, are designed for general-purpose operating systems with a wide range of applications. They allow users to set specific rules, such as allowing Chrome to access the network or blocking certain outbound connections. You can even configure Windows 11 firewall to alert you when any program attempts a connection to or from the internet to your PC, much like the "max security of the older" systems. An IoT device firewall, however, must contend with a much broader and more diverse ecosystem of devices, many of which have limited interfaces, minimal computing power, and specialized communication protocols. It's not about allowing or blocking a web browser; it's about managing traffic for a smart light bulb, a doorbell camera, or a garage door opener. These firewalls are often implemented at the network edge (e.g., within your router or a dedicated IoT security hub) rather than on each individual device, providing a centralized point of control. They are designed to understand the specific traffic patterns of IoT devices and block anything anomalous.Why Your Smart Devices Desperately Need a Firewall
The necessity of a dedicated **IoT device firewall** stems from the inherent risks associated with connected technology. Without one, your smart home becomes an open invitation for cybercriminals.The Threat of Inbound and Outbound Attacks
Just like a traditional network, IoT devices are susceptible to both inbound and outbound threats.- Inbound Threats: These are attempts by external malicious entities to gain unauthorized access to your devices. This could be an attacker trying to exploit a known vulnerability in your smart camera's firmware, or attempting to brute-force their way into your smart lock. As the "Data Kalimat" highlights, "Inbound connections that do not match a rule are blocked." An IoT firewall strictly enforces this, ensuring only legitimate traffic reaches your devices. Without proper rules, a device could be hijacked, leading to privacy breaches (e.g., camera feeds accessed) or even physical security risks.
- Outbound Threats: Equally, if not more, dangerous are outbound threats. If an IoT device is compromised (perhaps through an inbound attack or a pre-existing vulnerability), it can be weaponized. It might attempt to connect to malicious command-and-control servers, send spam, launch Distributed Denial of Service (DDoS) attacks against other targets, or exfiltrate your personal data. "Outbound connections that do not match a rule are blocked" is a critical principle here. An IoT firewall prevents compromised devices from "calling home" to attackers or participating in botnets. It's not just about what comes in; it's also about what goes out. For instance, some services might use specific IPs for certain functions, and both the IPs and URLs need to be permitted through the firewall to ensure proper connectivity, but only for legitimate services. An effective **IoT device firewall** meticulously controls this traffic, allowing only necessary communications.
- Data Breaches: Preventing unauthorized access to sensitive data collected by your devices (e.g., health data from wearables, location data from smart vehicles).
- Privacy Violations: Ensuring your smart speakers aren't recording conversations they shouldn't, or cameras aren't streaming without your consent.
- Network Overload: Blocking excessive or malicious traffic that could slow down your entire home network.
- Ransomware: Preventing malware from encrypting your device data or demanding payment.
Types of IoT Firewall Implementations
IoT firewalls aren't a one-size-fits-all solution. Their implementation varies depending on the scale and nature of the IoT deployment.- Router-Based Firewalls: Many modern home routers come with built-in firewall capabilities. These can offer a basic level of protection by segmenting your network (e.g., creating a separate guest Wi-Fi network) and blocking common ports. However, they often lack the granular control needed for advanced IoT security.
- Dedicated IoT Security Hubs/Gateways: These are specialized devices designed to sit between your router and your IoT devices. They act as a central point of control, inspecting all traffic to and from IoT devices. They often include features like intrusion detection/prevention, device profiling, and automated threat blocking.
- Cloud-Based Firewalls: For larger-scale or industrial IoT deployments, security can be managed in the cloud. Traffic from devices is routed through a cloud-based security service that applies firewall rules, performs threat analysis, and provides centralized management.
- Software-Defined Networking (SDN) Firewalls: In complex enterprise or industrial IoT environments, SDN allows for highly flexible and programmable network segmentation and firewalling, adapting to the dynamic nature of IoT traffic.
- Device-Level Firewalls (Limited): Some more sophisticated IoT devices (e.g., industrial controllers, high-end smart hubs) may have rudimentary firewall capabilities built into their firmware. However, these are typically limited and not sufficient as a standalone solution.
Key Features of an Effective IoT Firewall
An effective **IoT device firewall** goes beyond simple packet filtering. It incorporates a range of advanced features to provide robust protection:- Deep Packet Inspection (DPI): Unlike basic firewalls that only look at headers, DPI examines the actual content of data packets to identify malicious payloads or unusual traffic patterns specific to IoT protocols.
- Device Profiling and Whitelisting: The firewall learns the normal behavior of each IoT device (e.g., which servers it usually communicates with, what data it sends). Any deviation from this profile triggers an alert or block. This is akin to only adding outbound rules for some specific, trusted connections, as mentioned in the "Data Kalimat."
- Network Segmentation: The ability to isolate IoT devices onto a separate network segment (VLAN) from your main computers and sensitive data. If an IoT device is compromised, the breach is contained within that segment, preventing lateral movement to other parts of your network.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems actively monitor network traffic for signatures of known attacks and block them in real-time.
- Automated Threat Intelligence Feeds: The firewall should continuously update its threat intelligence database to recognize and block new and emerging threats.
- Centralized Management and Alerts: A user-friendly interface to configure rules, monitor traffic, and receive alerts about suspicious activity. Just as a user might want Windows 11 firewall to alert them when a program attempts a connection, an IoT firewall should provide similar visibility.
- Firmware Update Management: Some advanced IoT firewalls can help manage and ensure that connected devices receive necessary security updates, addressing a critical vulnerability.
- IP/URL Filtering: The ability to explicitly allow or block communication with specific IP addresses or URLs, ensuring that devices only connect to legitimate services. As the "Data Kalimat" notes, "The IPs listed do relate to the URLs, and both need to be permitted through the firewall to ensure proper connectivity."
Best Practices for Implementing and Managing IoT Firewalls
Deploying an IoT firewall is only the first step. Ongoing management and adherence to best practices are crucial for maintaining a secure environment.- Network Segmentation: This is arguably the most important step. Create a separate Wi-Fi network (or VLAN) specifically for your IoT devices. This ensures that even if an IoT device is compromised, it cannot directly access your computers, smartphones, or sensitive files on your main network.
- Default-Deny Policy: Configure your **IoT device firewall** to block all inbound and outbound connections by default, and then explicitly allow only the necessary communications for each device. This is the most secure approach, echoing the principle that "Inbound connections that do not match a rule are blocked, Outbound connections that do not match a rule are blocked."
- Regular Monitoring: Periodically check your firewall logs for unusual activity. Many IoT firewalls provide alerts for suspicious connections. Pay attention to these alerts.
- Keep Firmware Updated: Ensure your firewall device (e.g., router, IoT hub) has the latest firmware. Similarly, update the firmware on your IoT devices whenever possible. Outdated software is a common entry point for attackers.
- Strong, Unique Passwords: Change default passwords on all IoT devices and your firewall management interface immediately. Use strong, unique passwords for each device.
- Disable Unused Features: Turn off any features or services on your IoT devices that you don't use. This reduces the attack surface.
- Research Before You Buy: Before purchasing new IoT devices, research their security features and the manufacturer's commitment to security updates. Look for devices with a good track record.
- Be Wary of Public Wi-Fi: Avoid connecting critical IoT devices to public Wi-Fi networks, which are inherently less secure.
- Consult Troubleshooting Resources: If you encounter connectivity issues, just as you might search for "troubleshoot settings" for a Windows firewall, consult your IoT firewall's documentation or support forums. Sometimes, allowing specific IPs or URLs is necessary for device functionality, as mentioned in the "Data Kalimat" regarding network access.
Overcoming Challenges in IoT Firewall Deployment
While essential, implementing and managing an **IoT device firewall** isn't without its hurdles.- Complexity for Home Users: Many home users find network configuration daunting. The advanced settings of a dedicated IoT security hub can be complex, much like navigating "Windows Firewall with Advanced Security" (msc) for the first time. Simplifying user interfaces is key.
- Device Compatibility: Not all IoT devices play nicely with every firewall solution. Some older or niche devices might use proprietary protocols that a generic firewall struggles to understand.
- Performance Impact: Deep packet inspection and extensive rule sets can sometimes introduce latency, potentially affecting the responsiveness of real-time IoT applications (e.g., smart home automation).
- Cost: Dedicated IoT security hubs or cloud-based solutions can represent an additional investment beyond the cost of the devices themselves.
- False Positives: Overly aggressive firewall rules can block legitimate traffic, leading to devices not functioning correctly. This requires careful tuning and understanding of device communication patterns.
- Lack of Standardization: The IoT ecosystem is fragmented, with many different manufacturers and communication standards, making a universal firewall solution challenging.
The Future of IoT Security and Firewalls
The landscape of IoT security is constantly evolving. As devices become more sophisticated and deeply integrated into our lives, so too must the defenses protecting them. The future of the **IoT device firewall** will likely see several key developments:- AI and Machine Learning Integration: Firewalls will increasingly leverage AI and ML to learn normal device behavior, detect anomalies with greater precision, and automatically adapt security policies in real-time, moving beyond static rule sets.
- Zero Trust Architectures: The principle of "never trust, always verify" will become more prevalent. Every device and connection will be authenticated and authorized, regardless of its location within the network.
- Edge Computing Security: More security processing will occur at the "edge" of the network, closer to the devices themselves, reducing latency and improving responsiveness.
- Regulatory and Compliance Standards: Governments and industry bodies will likely introduce stricter regulations and certifications for IoT device security, forcing manufacturers to build security in from the design phase.
- Quantum-Resistant Cryptography: As quantum computing advances, the need for new encryption methods that can withstand quantum attacks will become critical for protecting IoT data.
- Enhanced User Control and Transparency: Future firewalls will offer users more intuitive ways to understand what their devices are doing and to control their data, perhaps even providing alerts similar to how Windows firewall can notify users of connection attempts.
Conclusion
The proliferation of IoT devices has undeniably transformed our homes and industries, offering unprecedented convenience and efficiency. However, this revolution comes with a significant caveat: security. As we've explored, the inherent vulnerabilities of many smart devices make a robust **IoT device firewall** not just an option, but a critical necessity for safeguarding your privacy, data, and even physical safety. From meticulously controlling inbound and outbound connections to leveraging advanced features like device profiling and network segmentation, these firewalls act as the frontline defense against a myriad of cyber threats. By understanding the threats, implementing best practices like network segmentation and strong passwords, and staying informed about the evolving security landscape, you can significantly enhance the protection of your connected world. Don't leave your smart home vulnerable; invest in and properly configure an IoT device firewall. What are your biggest concerns about IoT security, or what firewall solutions have you found most effective? Share your thoughts and experiences in the comments below, and consider exploring our other articles on home network security to further fortify your digital defenses.Related Resources:

Detail Author:
- Name : Lue Haag
- Username : lang.garth
- Email : charles.runte@yahoo.com
- Birthdate : 1982-12-17
- Address : 9934 Ford Radial Apt. 552 Lake Jacquesborough, KS 46991-7591
- Phone : 801-874-9047
- Company : Volkman-Quitzon
- Job : Medical Equipment Repairer
- Bio : Rerum ut explicabo quisquam omnis. Exercitationem numquam velit ut sint distinctio ut. Autem eos consectetur ullam in quia autem. Itaque totam ullam qui quod rerum perferendis odit sapiente.
Socials
twitter:
- url : https://twitter.com/magdalena_stehr
- username : magdalena_stehr
- bio : Dolores molestiae architecto aut consequatur. Quas voluptate natus consequatur enim nostrum vitae. Officiis aliquam soluta tempore.
- followers : 2704
- following : 210
instagram:
- url : https://instagram.com/stehrm
- username : stehrm
- bio : Omnis ipsum harum tempore. Reiciendis earum impedit veniam sint porro optio quia.
- followers : 544
- following : 187
tiktok:
- url : https://tiktok.com/@magdalena5014
- username : magdalena5014
- bio : Adipisci recusandae sit quaerat quia.
- followers : 1053
- following : 68