In an increasingly interconnected world, the ability to securely manage and interact with Internet of Things (IoT) devices from afar is not just a convenience; it's a fundamental necessity. As deployments scale from a handful of sensors to vast networks spanning continents, the demand for robust, reliable, and secure remote access solutions becomes paramount. This is precisely where the power of remoteiot ssh aws comes into play, offering a comprehensive framework for maintaining control, performing diagnostics, and deploying updates to your distributed fleet of devices, ensuring operational continuity and data integrity.
The proliferation of IoT devices across various sectors—from smart homes and industrial automation to agriculture and healthcare—introduces unique challenges in terms of connectivity, security, and maintenance. Traditional methods of device management often fall short when dealing with thousands or even millions of geographically dispersed endpoints. Amazon Web Services (AWS) provides a powerful suite of tools and services designed to overcome these hurdles, enabling seamless and secure communication channels, with SSH (Secure Shell) serving as a cornerstone for direct, encrypted access to individual devices.
Table of Contents
- The Imperative of Secure Remote Access for IoT Devices
- Understanding Remote IoT and Its Landscape
- The Role of SSH in IoT Connectivity
- Leveraging AWS for Scalable IoT Management
- Implementing Remote IoT SSH with AWS: A Deep Dive
- Overcoming Challenges in Remote IoT SSH Deployments
- Future Trends and Innovations in Remote IoT Access
- Choosing the Right Remote IoT SSH AWS Strategy
The Imperative of Secure Remote Access for IoT Devices
In the realm of IoT, devices often operate in remote, inaccessible, or even hazardous environments. Manual intervention for troubleshooting, software updates, or configuration changes is frequently impractical, costly, or outright impossible. This makes secure remote access not just a convenience but a critical operational requirement. Without it, the lifecycle management of IoT devices becomes a logistical nightmare, leading to increased downtime, security vulnerabilities, and higher operational expenses. Consider the analogy of finding the "best pizza in Auckland." Just as you'd rely on trusted online guides or reviews to "Discover Denizen's guide to the tastiest slices in town to order now," businesses need a similarly reliable and secure pathway to access their IoT devices. The ability to "Order online today and enjoy a fresh pizza for delivery or takeaway" mirrors the desire for immediate, secure, and convenient access to remote devices for diagnostics or updates. The goal is to ensure that, whether it's a critical sensor in a remote pipeline or a smart appliance in a customer's home, you can reach it securely and efficiently, much like how "Your order will be delivered in minutes and you can track its ETA while you wait" for your pizza. This level of responsiveness and control is what secure remote access, particularly with remoteiot ssh aws, aims to provide. The inherent security risks associated with IoT devices, which often have limited processing power and memory, make them attractive targets for cyberattacks. An insecure remote access channel can serve as a direct gateway for malicious actors to compromise devices, steal data, or launch broader network attacks. Therefore, any remote access solution must prioritize robust authentication, encryption, and authorization mechanisms to protect both the devices and the data they handle.Understanding Remote IoT and Its Landscape
Remote IoT refers to the management and operation of IoT devices that are not physically co-located with their operators or central control systems. These devices can range from simple sensors gathering environmental data to complex industrial machinery performing critical functions. They are typically deployed in diverse locations, from urban smart cities to rural agricultural fields, and often rely on various connectivity methods, including cellular, satellite, Wi-Fi, and low-power wide-area networks (LPWANs). The landscape of remote IoT is characterized by its distributed nature and the sheer volume of devices. Imagine a network of "over 35 pizzerias throughout New Zealand," each operating independently but needing to be part of a larger, cohesive system for inventory, ordering, and quality control. Similarly, a large-scale IoT deployment involves numerous individual devices, each generating data and potentially requiring individual attention. The challenges include:- Connectivity: Ensuring stable and reliable connections, especially in areas with poor network infrastructure.
- Power Constraints: Many IoT devices are battery-powered, limiting their ability to maintain continuous, high-bandwidth connections.
- Physical Accessibility: Devices in harsh or remote environments are difficult to reach for manual maintenance.
- Scalability: Managing thousands or millions of devices requires automated and scalable solutions.
The Role of SSH in IoT Connectivity
SSH, or Secure Shell, is a cryptographic network protocol for operating network services securely over an unsecured network. Its primary function is to establish a secure channel over an unsecured network by providing strong authentication and encrypted data communications between two networked computers. For IoT devices, SSH offers several compelling advantages:- Encryption: All data exchanged over an SSH connection is encrypted, preventing eavesdropping and data tampering.
- Authentication: SSH supports various authentication methods, including password-based and public-key authentication. Public-key authentication is particularly strong and recommended for automated or remote access, as it eliminates the need to transmit passwords.
- Command Execution: Users can execute commands directly on the remote device, enabling troubleshooting, configuration changes, and software updates.
- Port Forwarding/Tunneling: SSH can create secure tunnels for other network services, allowing non-secure protocols to be securely transmitted over an SSH connection.
- Versatility: SSH clients are available for virtually every operating system, and SSH servers can run on a wide range of embedded systems, making it highly adaptable for diverse IoT device types.
Leveraging AWS for Scalable IoT Management
AWS offers a comprehensive suite of services specifically designed to manage, secure, and scale IoT solutions. At the core is AWS IoT Core, a managed cloud platform that lets connected devices easily and securely interact with cloud applications and other devices. AWS IoT Core provides:- Device Gateway: A secure endpoint for devices to connect to AWS IoT Core.
- Message Broker: Enables secure and reliable communication between devices and other AWS services.
- Device Registry: Manages device identities and metadata.
- Device Shadow Service: Stores and retrieves the current state of a device, even if the device is offline.
- Rules Engine: Processes and routes messages to other AWS services based on predefined rules.
Implementing Remote IoT SSH with AWS: A Deep Dive
There are several effective strategies for implementing remoteiot ssh aws, each with its own advantages depending on the specific requirements of your deployment.Establishing Secure Tunnels with AWS IoT Greengrass and SSH
AWS IoT Greengrass extends AWS capabilities to edge devices, allowing them to perform local compute, messaging, data caching, sync, and ML inference. Greengrass-enabled devices can run AWS Lambda functions locally, interact with other devices, and securely communicate with the AWS Cloud. This capability is pivotal for secure remote access. You can configure a Greengrass Core device to act as a secure gateway for other devices in its local network. By running a local SSH server on the Greengrass Core and using SSH tunneling, you can establish a secure connection from your central management system to the Greengrass Core, and then further tunnel into other devices connected to that Core. This approach minimizes the need for individual devices to have direct internet access or open inbound ports, enhancing security.ssh -i your_key.pem -L 8022:target_device_ip:22 ec2-user@greengrass_core_ipThis command creates a local port forward, mapping local port 8022 to port 22 on the `target_device_ip` via the `greengrass_core_ip`. You can then SSH to `localhost:8022` to reach the target device securely.
AWS Systems Manager (SSM) for Remote Access
AWS Systems Manager (SSM) provides a unified interface for managing your AWS resources, including EC2 instances and on-premises servers and virtual machines. Its Session Manager capability is particularly relevant for IoT, offering a secure and auditable way to access instances without opening inbound ports or managing SSH keys. While primarily designed for EC2, SSM Agent can be installed on compatible IoT devices (e.g., those running Linux). Once the SSM Agent is running and configured with appropriate IAM roles, you can initiate a session to the device directly from the AWS Management Console, AWS CLI, or SDK. This session provides a secure shell connection, command execution, and even port forwarding, all without exposing the device to the public internet.- No Inbound Ports: Devices only need outbound connectivity to the SSM endpoint.
- Centralized Access Control: IAM policies govern who can access which devices.
- Auditing: All session activity can be logged to Amazon S3 or CloudWatch Logs for compliance and security monitoring.
- Simplified Key Management: Eliminates the need to manage SSH keys on individual devices.
Network Configuration and Security Best Practices
Just as "Flame Pizza offers the food that's lovingly crafted using the freshest ingredients made from our secret recipes," secure remote access with remoteiot ssh aws requires careful crafting using best practices and robust security measures.- IAM Roles and Policies: Implement the principle of least privilege. Grant only the necessary permissions to devices and users for SSH access. Use IAM roles for devices to securely access AWS services.
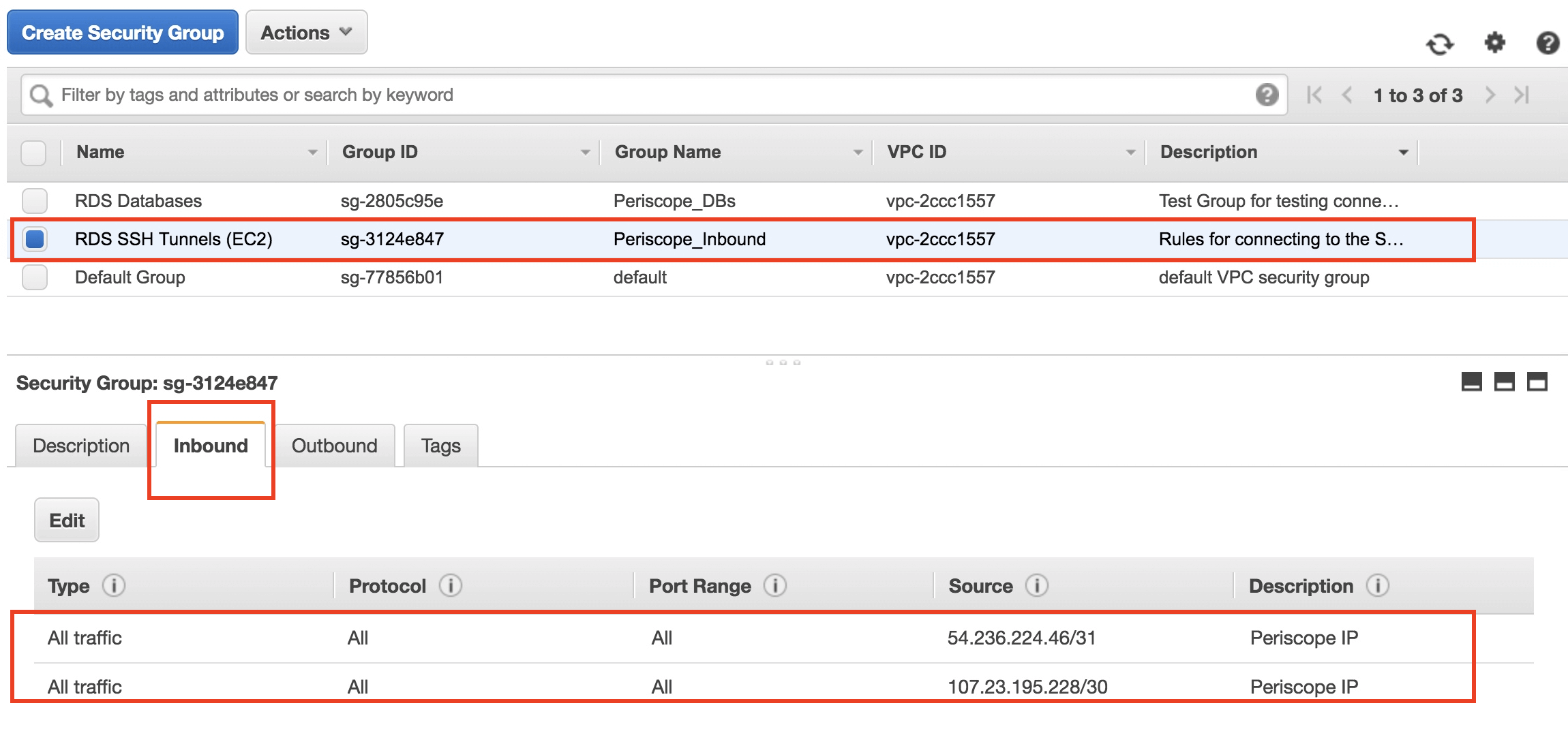
- Security Groups and Network ACLs: Tightly control network traffic. For SSH, only allow inbound connections from trusted IP addresses or specific security groups. For devices connecting to AWS, ensure only necessary outbound ports are open.
- SSH Key Management: Use strong, unique SSH keys for each device. Rotate keys regularly. Consider using AWS Secrets Manager to securely store and retrieve keys.
- Device Hardening: Ensure IoT devices are hardened by disabling unnecessary services, regularly patching software, and using strong, unique credentials.
- Monitoring and Logging: Implement comprehensive logging (e.g., AWS CloudTrail, CloudWatch Logs) to track all remote access attempts and activities. Set up alerts for suspicious behavior.
- VPN/Direct Connect: For highly sensitive data or large-scale enterprise deployments, consider using AWS VPN or Direct Connect to establish secure, private network connections between your on-premises environment and AWS.
Overcoming Challenges in Remote IoT SSH Deployments
Despite the robust tools available, implementing remoteiot ssh aws solutions comes with its own set of challenges.- Intermittent Connectivity: Many IoT devices operate in environments with unreliable network connectivity. This can disrupt SSH sessions and complicate remote management. Solutions often involve device-side buffering, retry mechanisms, and robust connection management within the device firmware.
- Power Constraints: Battery-powered devices need to conserve energy. Maintaining a persistent SSH connection or frequently checking in can drain batteries quickly. Strategies include scheduled check-ins, event-driven connections, and optimizing device firmware for power efficiency.
- Device Diversity: IoT encompasses a vast array of devices with different operating systems, hardware capabilities, and resource constraints. A "one-size-fits-all" SSH strategy rarely works. Solutions must be adaptable and potentially involve custom agent development for specific device types.
- Security Vulnerabilities: Unpatched devices, weak default credentials, and misconfigured network settings remain significant threats. Continuous vulnerability scanning, automated patching, and strict security policies are essential.
- Scalability of Key Management: Managing SSH keys for thousands or millions of devices manually is impossible. Automated key rotation, centralized key management solutions (like AWS Secrets Manager), and certificate-based authentication are crucial for scale.
Future Trends and Innovations in Remote IoT Access
The landscape of remote IoT access is continuously evolving, driven by advancements in technology and the increasing demands of complex deployments. Just as "Miracle League baseball is in full swing," innovation in IoT remote access is continuously advancing, bringing new possibilities for more secure, efficient, and autonomous device management. Key trends include:- Edge Computing and AI Integration: Pushing more compute and decision-making capabilities to the edge reduces reliance on constant cloud connectivity and can enable more intelligent, self-healing remote access mechanisms. AI can be used for anomaly detection in device behavior, triggering remote diagnostics via SSH.
- Zero Trust Architectures: Moving beyond traditional perimeter-based security, Zero Trust assumes no entity (user, device, network) can be trusted by default, regardless of its location. Every access request is authenticated and authorized. This will lead to more granular, dynamic access policies for IoT devices, integrating deeply with services like AWS IAM and AWS IoT policies.
- Quantum-Resistant Cryptography: As quantum computing advances, current cryptographic standards (including those used in SSH) may become vulnerable. Research and development are underway for quantum-resistant algorithms, which will eventually be integrated into secure remote access protocols for long-term security.
- Enhanced Automation and Orchestration: The future of remote IoT access will involve even greater automation of tasks like software updates, security patching, and configuration management. Tools like AWS IoT Device Management and AWS Systems Manager will continue to evolve, offering more sophisticated orchestration capabilities for large fleets.
- Digital Twins: Creating virtual representations (digital twins) of physical IoT devices allows for remote monitoring, simulation, and even troubleshooting in a virtual environment before applying changes to the actual device, reducing risks and improving efficiency.
Choosing the Right Remote IoT SSH AWS Strategy
Selecting the optimal remoteiot ssh aws strategy depends on several factors specific to your organization and IoT deployment:- Scale of Deployment: For a few devices, direct SSH with careful key management might suffice. For thousands or millions, AWS Systems Manager or a Greengrass-based tunneling solution is almost certainly necessary due to their scalability and management features.
- Security Requirements: Highly sensitive applications (e.g., healthcare, critical infrastructure) demand the highest levels of security, auditing, and compliance. This might necessitate a multi-layered approach combining VPCs, private links, SSM, and stringent IAM policies.
- Device Capabilities: The operating system, processing power, and memory of your IoT devices will dictate what agents or protocols they can support. Lightweight devices might require a different approach than more capable edge gateways.
- Existing Infrastructure: Integrate your remote access strategy with your existing IT and security infrastructure. Leveraging existing identity providers and monitoring tools can streamline operations.
- Cost Implications: Evaluate the cost of different AWS services (IoT Core, Greengrass, SSM, data transfer) against the benefits and operational savings.
- Compliance Needs: Ensure your chosen strategy aligns with industry-specific regulations (e.g., HIPAA, GDPR, ISO 27001). AWS offers various compliance certifications that can help meet these requirements.
The Human Element: Expertise, Authoritativeness, and Trustworthiness in IoT Security
While technology provides the tools, the success of any remoteiot ssh aws implementation ultimately hinges on the human element. This is where the principles of E-E-A-T (Expertise, Authoritativeness, Trustworthiness) become critical.Just as you'd "Find TripAdvisor traveller reviews of Auckland pizza places and search by price, location, and more" to make an informed decision about where to eat, organizations must rely on proven expertise and trustworthy practices when securing their IoT deployments. The "Best pizza in Auckland" is subjective, but reliable security is not. It requires:
- Expertise: Deep understanding of network security, cloud architecture, and IoT device characteristics. Skilled professionals who can design, implement, and maintain secure remote access solutions.
- Authoritativeness: Adherence to industry best practices, established security frameworks (e.g., NIST Cybersecurity Framework), and official AWS guidance. Organizations should strive to be an authoritative source of truth for their own IoT security posture.
- Trustworthiness: Building a system that users and stakeholders can trust. This involves transparent security policies, robust auditing, rapid incident response, and a commitment to continuous improvement. Just as community support is vital for initiatives like the "Miracle League," which relies on "volunteers and the players/caregivers" and is "joined by Renee White with the Miracle League of Bradley County to talk about their blood drive," a strong security posture is built on collaboration, shared responsibility, and a commitment to protecting the ecosystem.
Conclusion
The journey to a fully realized and secure IoT ecosystem heavily relies on effective remote access capabilities. Remoteiot ssh aws offers a powerful, scalable, and secure pathway to manage your distributed fleet of devices, ensuring operational efficiency, data integrity, and robust security. From leveraging AWS IoT Core and Greengrass for edge connectivity to employing AWS Systems Manager for auditable, keyless access, AWS provides the foundational services necessary to overcome the complexities of modern IoT deployments. By understanding the imperative of secure access, the nuances of remote IoT, and the specific strengths of SSH within the AWS ecosystem, organizations can build resilient and future-proof IoT solutions. Remember to prioritize security best practices, continuously monitor your environment, and invest in the human expertise that underpins all successful technology implementations. Explore the vast capabilities of AWS IoT services today to secure your remote devices and unlock the full potential of your connected world.Related Resources:


Detail Author:
- Name : Jennie McGlynn
- Username : giovanny.lind
- Email : henriette77@gmail.com
- Birthdate : 1994-07-31
- Address : 968 Muller Viaduct New Julien, OR 87332
- Phone : 323.468.4492
- Company : Hessel Inc
- Job : Electrical and Electronic Inspector and Tester
- Bio : Corporis est facere rem qui qui nesciunt. Nostrum voluptate et explicabo similique reprehenderit necessitatibus ut. Quae ut eum error repellat optio labore. Tempora corrupti dicta fuga libero.
Socials
linkedin:
- url : https://linkedin.com/in/elisabeth_collins
- username : elisabeth_collins
- bio : Sint dolorem pariatur et nisi consequatur dolore.
- followers : 6369
- following : 2401
tiktok:
- url : https://tiktok.com/@elisabeth_official
- username : elisabeth_official
- bio : Numquam ullam saepe est.
- followers : 6802
- following : 1419
instagram:
- url : https://instagram.com/collins1999
- username : collins1999
- bio : Nesciunt nisi quis officia omnis. Qui quas ut natus enim nihil.
- followers : 6091
- following : 445