In today's increasingly connected world, the Internet of Things (IoT) is transforming industries, from smart homes and cities to industrial automation and healthcare. However, connecting and managing a vast network of remote IoT devices presents unique challenges, particularly concerning security, scalability, and reliability. This is where the power of an AWS VPC network for remote IoT becomes not just beneficial, but absolutely essential for any serious deployment.
Navigating the complexities of IoT connectivity requires a robust and secure foundation. Amazon Web Services (AWS) Virtual Private Cloud (VPC) provides an isolated, highly customizable virtual network where you can deploy your AWS resources, including those critical for your IoT ecosystem. Understanding how to leverage AWS VPC effectively for your remote IoT initiatives is key to building a resilient, secure, and future-proof infrastructure that can handle the demands of millions of devices.
Table of Contents
- Understanding the Foundation: What is an AWS VPC?
- The Unique Challenges of Remote IoT Connectivity
- How AWS VPC Networks Address Remote IoT Needs
- Core Components for a Robust Remote IoT VPC Network
- Implementing Security in Your Remote IoT VPC Network
- Scaling Your Remote IoT Infrastructure with AWS VPC
- Best Practices for Managing Your Remote IoT VPC Network
- Real-World Applications and Future Trends
Understanding the Foundation: What is an AWS VPC?
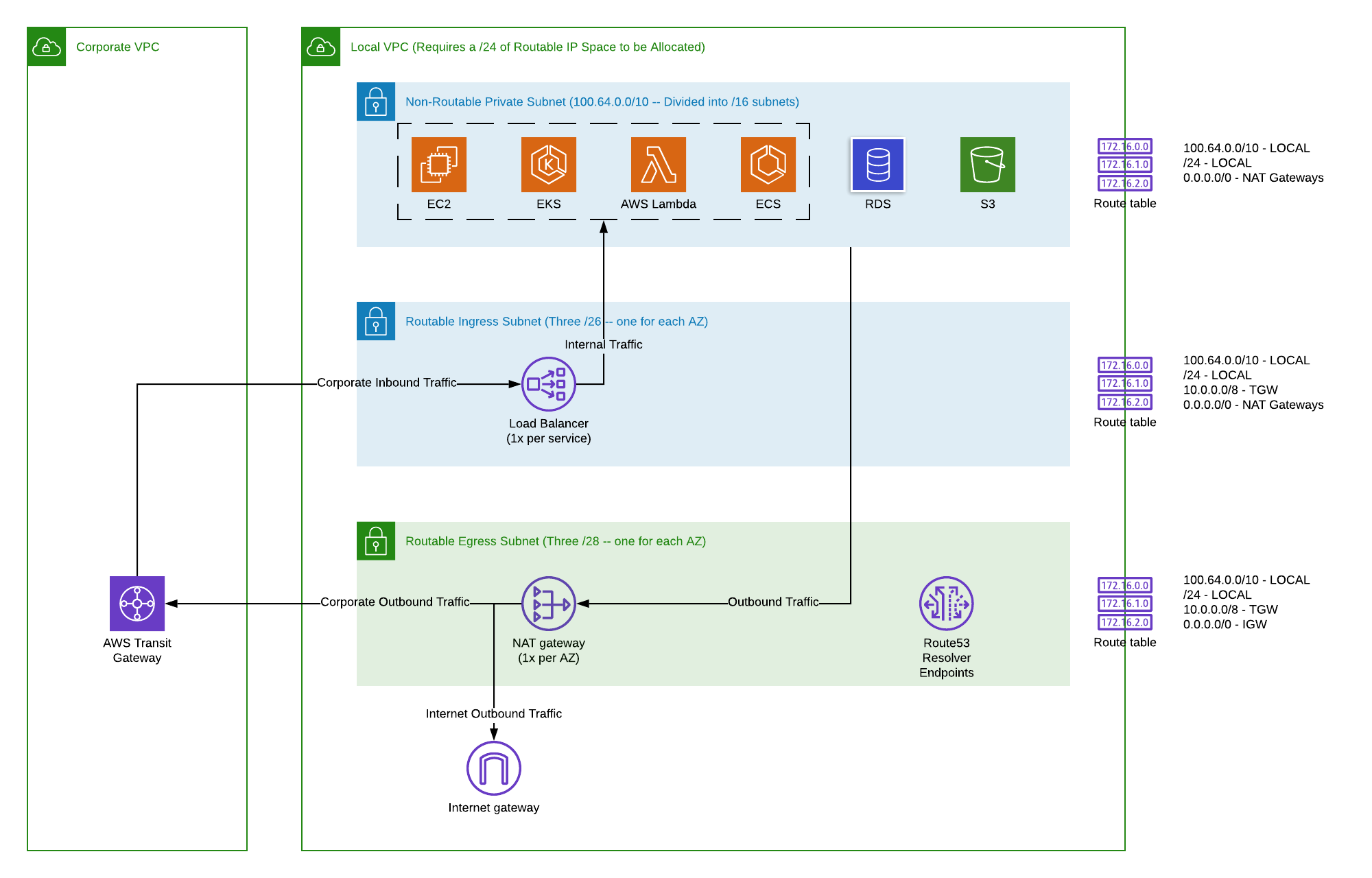
At its heart, an AWS VPC is a logically isolated section of the AWS cloud where you can launch AWS resources in a virtual network that you define. Think of it as your own private data center within AWS. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables, network gateways, and security settings. This level of control is paramount when dealing with sensitive IoT data and a distributed fleet of devices. Within a VPC, you can define one or more subnets. These subnets can be public (with internet access via an Internet Gateway) or private (without direct internet access, often routed through a NAT Gateway for outbound connectivity). For IoT, this distinction is crucial for security. You can place your backend processing and database resources in private subnets, ensuring they are not directly exposed to the internet, while allowing controlled access for your IoT devices through secure channels. Security Groups act as virtual firewalls at the instance level, controlling inbound and outbound traffic, while Network Access Control Lists (NACLs) provide stateless packet filtering at the subnet level. This multi-layered approach to network security forms the bedrock of a secure remote IoT VPC network AWS.The Unique Challenges of Remote IoT Connectivity
Connecting remote IoT devices isn't as simple as plugging in a server. These devices often operate in diverse and challenging environments, bringing forth a unique set of hurdles: * **Distributed Devices and Varied Network Conditions:** IoT devices are everywhere – on factory floors, in remote agricultural fields, within smart city infrastructure, or even on moving vehicles. They rely on a myriad of connectivity options, from cellular (2G, 3G, 4G, 5G), Wi-Fi, LoRaWAN, to satellite. Each comes with its own latency, bandwidth, and reliability characteristics. * **Security Vulnerabilities:** Edge devices can be physically exposed, making them targets for tampering. Data transmitted from these devices, often over public networks, is susceptible to interception. Ensuring the authenticity of devices and the integrity of data throughout its journey from edge to cloud is a monumental task. A single compromised device could become a gateway into your entire network. * **Scalability Issues:** IoT deployments can start small but grow exponentially, potentially involving millions or even billions of devices. The network infrastructure must be able to scale seamlessly without compromising performance or security. Traditional network architectures often struggle with this sheer volume of connections and data. * **Latency and Reliability Concerns:** For critical applications, such as industrial control or autonomous vehicles, low latency is non-negotiable. Data must travel quickly and reliably from the device to the cloud and back. Network interruptions or high latency can lead to operational failures or even dangerous situations. * **Device Management and Updates:** Remotely managing firmware updates, configuration changes, and troubleshooting for a large fleet of devices is complex. A robust network foundation is needed to facilitate these operations efficiently and securely. These challenges underscore the necessity for a well-architected cloud networking solution, and this is precisely where an AWS VPC network for remote IoT shines.How AWS VPC Networks Address Remote IoT Needs
AWS VPC provides the foundational network infrastructure that effectively addresses the inherent complexities of remote IoT. By creating a dedicated, isolated network environment, organizations gain unparalleled control and flexibility. * **Centralized Control for Decentralized Devices:** Despite devices being geographically dispersed, their communication and data processing can be routed through a centralized, secure VPC. This allows for unified management, monitoring, and security policy enforcement, simplifying operations significantly. * **Enhancing Security Posture:** The isolation provided by a VPC means your IoT backend services are not directly exposed to the public internet. Coupled with granular security controls like Security Groups and Network ACLs, you can define precise rules for who and what can communicate with your IoT resources. This significantly reduces the attack surface and helps protect sensitive data flowing through your remote IoT VPC network AWS. * **Scalability for Growth:** AWS VPC is designed for massive scale. As your IoT fleet grows from hundreds to millions of devices, your VPC can expand to accommodate the increased traffic and processing demands. AWS services within the VPC, such as EC2 instances, Lambda functions, and databases, can be scaled automatically or manually to handle fluctuating loads. * **Reliability and Performance:** By deploying resources across multiple Availability Zones within your VPC, you ensure high availability and fault tolerance. Should one zone experience an issue, your IoT services can seamlessly failover to another. Furthermore, the global reach of AWS allows you to deploy VPCs closer to your device locations, minimizing latency and improving the responsiveness of your IoT applications.Core Components for a Robust Remote IoT VPC Network
Building an effective remote IoT VPC network AWS involves careful consideration of several core components and design principles.VPC Design Principles for IoT
The initial design of your VPC is critical. A well-planned VPC ensures security, scalability, and manageability from the outset. * **Multi-Availability Zone (Multi-AZ) Deployment:** Always design your VPC to span multiple Availability Zones. This provides high availability and fault tolerance for your IoT backend services. If one AZ experiences an outage, your services can continue to operate in another. * **Private and Public Subnets:** A standard practice is to create both public and private subnets. Public subnets host resources that need direct internet access, such as load balancers or internet gateways. Private subnets are for your core IoT application components, databases, and message brokers, which should not be directly accessible from the internet. Outbound internet access from private subnets can be routed through a NAT Gateway in a public subnet. * **IP Addressing Strategy:** Plan your IP address ranges carefully. Use private IP address ranges (e.g., 10.0.0.0/16, 172.16.0.0/12, 192.168.0.0/16) to avoid conflicts with your on-premises networks if you plan hybrid connectivity. Ensure you have enough IP addresses for future growth, considering both current and projected device counts and backend services. * **Dedicated VPCs for Different Environments:** For larger or more complex IoT deployments, consider using separate VPCs for different environments (e.g., development, testing, production). This provides stronger isolation and prevents changes in one environment from impacting others. VPC Peering or AWS Transit Gateway can be used to connect these VPCs securely when necessary.Connectivity Options: Bridging the Edge to the Cloud
Connecting your remote IoT devices securely and efficiently to your AWS VPC is paramount. AWS offers a variety of services to facilitate this: * **AWS IoT Core:** This is the primary service for connecting IoT devices to the AWS cloud. It acts as a managed cloud platform that lets connected devices easily and securely interact with cloud applications and other devices. IoT Core supports standard protocols like MQTT, HTTPS, and LoRaWAN, and integrates seamlessly with other AWS services. Devices typically connect to IoT Core endpoints, which then route messages to your backend services within the VPC. * **VPN (Virtual Private Network):** * **Site-to-Site VPN:** For devices or gateways located in a fixed remote location with an existing network, a Site-to-Site VPN connection can establish a secure, encrypted tunnel between your on-premises network and your AWS VPC. This is ideal for industrial IoT scenarios where a local gateway aggregates data from many devices before sending it to the cloud. * **Client VPN:** For individual remote devices or mobile users needing secure access to your VPC, Client VPN provides a fully managed VPN service that enables secure access from anywhere. * **AWS Direct Connect:** For high-bandwidth, low-latency, and consistent network performance, Direct Connect establishes a dedicated network connection from your premises to AWS. While often overkill for individual devices, it's invaluable for large-scale industrial IoT deployments, data centers aggregating vast amounts of IoT data, or edge locations requiring robust, private connectivity to the cloud. * **AWS Transit Gateway:** As your network architecture grows more complex, involving multiple VPCs, on-premises networks, and perhaps even other AWS accounts, Transit Gateway becomes indispensable. It acts as a central hub that connects your VPCs and on-premises networks, simplifying routing and management. For IoT, this means you can connect various regional IoT deployments or different business units' VPCs to a central IoT processing VPC, creating a scalable hub-and-spoke model. Each of these connectivity options plays a vital role in building a comprehensive and secure remote IoT VPC network AWS.Implementing Security in Your Remote IoT VPC Network
Security is not an afterthought in IoT; it must be designed in from the ground up. Within your AWS VPC, several layers of security can be implemented to protect your IoT ecosystem. * **Security Groups and Network ACLs:** These are your primary tools for controlling network traffic. Security Groups operate at the instance level, allowing you to specify what inbound and outbound traffic is permitted for your EC2 instances, databases, or other services. Network ACLs, on the other hand, operate at the subnet level and provide a stateless firewall for all traffic entering or leaving a subnet. Using a combination of both provides robust, granular control over your network flow. For example, you might configure a Security Group to only allow MQTT traffic from AWS IoT Core endpoints to your message broker instances. * **IAM Policies (Identity and Access Management):** AWS IAM is fundamental for managing access to your AWS resources. For IoT, this extends to defining precise permissions for your devices (via X.509 certificates and IoT Policies) and the AWS services that interact with them. Apply the principle of least privilege: grant only the permissions necessary for a device or service to perform its intended function. * **AWS WAF and Shield:** For IoT solutions that expose APIs or web interfaces to the internet (e.g., for device management dashboards), AWS Web Application Firewall (WAF) and AWS Shield provide protection against common web exploits and Distributed Denial of Service (DDoS) attacks. WAF helps protect your web applications or APIs from common web exploits that could affect availability, compromise security, or consume excessive resources. * **Encryption:** Data security relies heavily on encryption. * **Data in Transit:** Ensure all communication between your IoT devices and AWS IoT Core, and between services within your VPC, uses Transport Layer Security (TLS). AWS IoT Core automatically enforces TLS 1.2 for device connections. * **Data at Rest:** Encrypt data stored in databases (e.g., Amazon RDS, DynamoDB), S3 buckets, and other storage services using AWS Key Management Service (KMS) or other encryption mechanisms. * **Monitoring and Logging:** Comprehensive monitoring and logging are crucial for detecting anomalies and potential security threats. * **Amazon CloudWatch:** Collects and tracks metrics, collects and monitors log files, and sets alarms for your AWS resources and applications. * **AWS CloudTrail:** Records API calls made within your AWS account, providing an audit trail of actions taken. * **VPC Flow Logs:** Capture information about the IP traffic going to and from network interfaces in your VPC. This data can be published to CloudWatch Logs or Amazon S3, allowing you to analyze traffic patterns, troubleshoot connectivity issues, and detect unauthorized access attempts within your remote IoT VPC network AWS.Scaling Your Remote IoT Infrastructure with AWS VPC
The true power of AWS lies in its ability to scale, and this is particularly vital for IoT, where device counts and data volumes can grow rapidly and unpredictably. Your VPC provides the canvas for this scalability. * **Auto Scaling Groups for Backend Services:** For your backend processing services (e.g., EC2 instances running custom applications, message queues, or data ingestion pipelines), Auto Scaling Groups automatically adjust the number of instances in response to demand. This ensures your application can handle spikes in device connections or data ingestion without manual intervention. * **Load Balancers (ALB, NLB):** AWS Elastic Load Balancing (ELB) distributes incoming application traffic across multiple targets, such as EC2 instances, in multiple Availability Zones. For IoT, Application Load Balancers (ALB) are excellent for routing HTTP/HTTPS traffic to your API gateways, while Network Load Balancers (NLB) are ideal for high-performance, low-latency TCP/UDP traffic, which might be relevant for certain IoT protocols. * **Leveraging Serverless (Lambda) for Event-Driven Processing:** AWS Lambda allows you to run code without provisioning or managing servers. This serverless approach is incredibly powerful for IoT, as it scales automatically with the number of events (e.g., device messages). You can trigger Lambda functions directly from AWS IoT Core rules, processing messages, storing data, or triggering downstream actions without worrying about server capacity. This is a highly cost-effective and scalable way to handle the unpredictable nature of IoT data streams within your remote IoT VPC network AWS. * **Horizontal Scaling of IoT Core Endpoints:** While AWS IoT Core itself is a managed service that scales automatically, understanding its regional endpoints and how your devices connect can inform your overall architecture. For extremely large deployments, distributing devices across multiple regions or leveraging AWS IoT Greengrass for edge processing can further enhance scalability and reduce latency.Best Practices for Managing Your Remote IoT VPC Network
Effective management of your IoT VPC network goes beyond initial setup; it involves continuous optimization and adherence to best practices. * **Network Segmentation:** Beyond public and private subnets, consider further segmenting your VPC using additional subnets and stricter Security Group rules. For example, isolate databases in their own subnet, separate from application servers. This limits the blast radius in case of a security breach. * **Regular Security Audits and Penetration Testing:** Periodically review your VPC configurations, Security Group rules, and IAM policies. Conduct penetration testing to identify vulnerabilities in your IoT solution, from the device level to the cloud backend. AWS provides services like Amazon Inspector to automate security assessments. * **Disaster Recovery Planning:** Have a clear plan for disaster recovery. This includes backing up critical data, defining Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO), and potentially setting up multi-region disaster recovery strategies for your most critical IoT applications. * **Cost Optimization Strategies:** Data transfer costs can quickly accumulate in IoT. Optimize by: * Minimizing unnecessary data transfer (e.g., send only essential data). * Leveraging edge processing (AWS IoT Greengrass) to process data closer to the source and send only aggregated or critical data to the cloud. * Using VPC Endpoints for private connections to AWS services (like S3, DynamoDB) to avoid traffic traversing the public internet, which can be more secure and potentially cheaper. * **Infrastructure as Code (IaC):** Use tools like AWS CloudFormation or Terraform to define your VPC, subnets, routing, security groups, and other network components as code. This ensures consistency, repeatability, and version control for your infrastructure, making it easier to manage, update, and replicate your remote IoT VPC network AWS across different environments or regions.Real-World Applications and Future Trends
The principles of building a secure and scalable remote IoT VPC network AWS are applicable across a vast array of industries and use cases. * **Smart Cities:** Managing thousands of sensors for traffic monitoring, environmental sensing, and public safety requires a robust, scalable, and secure network to handle massive data ingestion and real-time analytics. * **Industrial IoT (IIoT):** Connecting machinery, sensors, and control systems in factories or remote industrial sites demands ultra-low latency, high reliability, and stringent security to ensure operational continuity and worker safety. * **Connected Health:** Wearable devices, remote patient monitoring systems, and smart medical equipment generate sensitive health data that requires the highest levels of security and compliance, making a private and controlled VPC environment indispensable. * **Automotive:** Connected cars, fleet management, and autonomous vehicles generate enormous volumes of telemetry data that must be securely transmitted and processed in real-time for navigation, diagnostics, and safety features. Looking ahead, several trends will further shape the evolution of remote IoT networks: * **Edge Computing Integration (AWS IoT Greengrass):** Pushing computation and data processing closer to the devices (the "edge") reduces latency, conserves bandwidth, and enhances security. AWS IoT Greengrass allows you to run Lambda functions, Docker containers, and even machine learning models directly on edge devices, integrating seamlessly with your cloud VPC for centralized management and aggregated data analysis. * **5G and its Impact on Remote IoT Connectivity:** The rollout of 5G networks promises unprecedented bandwidth and ultra-low latency, which will unlock new possibilities for real-time IoT applications, especially those requiring massive connectivity and critical response times. This will place even greater emphasis on robust and high-performance cloud backends within VPCs to handle the increased data throughput. * **Serverless First Architectures:** The trend towards serverless computing will continue to grow for IoT backends, offering unmatched scalability and cost-efficiency for handling event-driven data streams. * **Enhanced AI/ML at the Edge and in the Cloud:** As IoT data volumes grow, the need for advanced analytics and machine learning to derive insights will become more critical, both at the edge and within the cloud VPC.Conclusion
Building a successful remote IoT solution hinges on a strong, secure, and scalable network foundation. The AWS VPC network for remote IoT provides exactly this, offering unparalleled control, flexibility, and a comprehensive suite of services to meet the diverse demands of modern IoT deployments. By carefully designing your VPC, implementing robust security measures, leveraging AWS's scalable services, and adhering to best practices, you can create an IoT infrastructure that is not only resilient and high-performing but also future-proof. The journey into remote IoT is complex, but with the right architectural choices and a deep understanding of AWS VPC capabilities, you can confidently connect, secure, and scale your device fleet, unlocking the full potential of your connected world. We encourage you to explore AWS IoT services and VPC documentation further to tailor these insights to your specific needs. What challenges have you faced in your IoT deployments, and how has a robust network architecture helped overcome them? Share your experiences in the comments below, or feel free to share this article with your network to spark further discussion on this critical topic.Related Resources:


Detail Author:
- Name : Maximillia Kulas
- Username : millie.raynor
- Email : lueilwitz.anais@yahoo.com
- Birthdate : 1991-03-11
- Address : 946 Aisha Ville Purdyburgh, NV 04461-1126
- Phone : +15412911297
- Company : Lesch, Upton and Osinski
- Job : Medical Scientists
- Bio : Ipsa sunt ea magnam id qui. Et ut ea quisquam magnam. Iste dicta sint velit quia ut qui.
Socials
facebook:
- url : https://facebook.com/darian5025
- username : darian5025
- bio : Inventore ut porro dolorum autem omnis minus.
- followers : 3100
- following : 838
instagram:
- url : https://instagram.com/darian_dev
- username : darian_dev
- bio : Sit rerum mollitia omnis porro voluptatibus a numquam. Laudantium optio voluptatem repellat sed.
- followers : 2939
- following : 277
linkedin:
- url : https://linkedin.com/in/darianhintz
- username : darianhintz
- bio : Aliquid assumenda assumenda autem corrupti illum.
- followers : 6959
- following : 1773