**In today's interconnected world, the Internet of Things (IoT) has permeated nearly every industry, from smart homes and healthcare to industrial automation and smart cities. Managing these vast networks of devices, often dispersed across wide geographical areas, presents unique challenges. This is where the power of remote access, particularly through solutions involving a **remoteiot web ssh download**, becomes not just convenient but absolutely essential for efficient and secure operations.** The ability to securely interact with devices from anywhere, troubleshoot issues, deploy updates, and monitor performance without physical presence is a game-changer, fundamentally transforming how we approach IoT infrastructure. The journey into effective remote IoT management often begins with understanding the robust capabilities of Web SSH. It offers a browser-based gateway to the secure shell protocol, eliminating the need for dedicated client software on every workstation. For businesses and individuals alike, this means unparalleled flexibility and accessibility, making the "remoteiot web ssh download" a critical first step in establishing a resilient and responsive IoT ecosystem. This article will delve deep into the intricacies of Web SSH for IoT, guiding you through its benefits, security considerations, and practical implementation, ensuring you're equipped to harness its full potential. 22` or `nc -vz 22`)? This confirms network path and port openness. 2. **Check SSH Server Status on Device:** Ensure the SSH server (e.g., `sshd`) is running on your IoT device. Use commands like `sudo systemctl status sshd` or `sudo service ssh status` if you can access the device locally or via another method. 3. **Review SSH Server Logs:** On the IoT device, examine the SSH server logs (e.g., `/var/log/auth.log` or `/var/log/secure` on Linux) for error messages related to connection attempts or authentication failures. These logs are invaluable for pinpointing the exact issue. 4. **Test with a Standard SSH Client:** If possible, try connecting to the IoT device using a traditional SSH client (like OpenSSH from your local machine) from the same network as your Web SSH gateway. If this works, the problem likely lies with your Web SSH gateway configuration; if it doesn't, the issue is probably with the IoT device's SSH server or network setup. 5. **Examine Web SSH Gateway Logs:** Your Web SSH solution will have its own logs. Check these for errors related to proxying SSH connections, user authentication, or internal service issues. By following these steps, you can methodically isolate and resolve most issues preventing a successful "remoteiot web ssh download" connection to your IoT devices.
Table of Contents
- The Dawn of Remote IoT Management: Why Web SSH Matters
- Understanding Web SSH: More Than Just a Terminal in Your Browser
- Navigating the "RemoteIoT Web SSH Download" Landscape
- Step-by-Step: Getting Started with Your Remote IoT Web SSH Download
- Security First: Protecting Your Remote IoT Infrastructure
- Practical Applications and Use Cases for Remote IoT Web SSH
- Overcoming Challenges: Common Issues and Solutions
- The Future of Remote IoT Management: Trends and Innovations
The Dawn of Remote IoT Management: Why Web SSH Matters
The proliferation of IoT devices has introduced unprecedented complexity into network management. From smart sensors monitoring environmental conditions in remote agricultural fields to industrial machinery in sprawling factories, these devices often operate in locations that are difficult, expensive, or even dangerous to access physically. Traditional methods of device management, which might involve on-site visits or proprietary software installations, simply don't scale. This is where the concept of remote management steps in as a critical enabler, allowing administrators and developers to interact with devices as if they were physically present, but from the comfort of their office or even a mobile device. Web SSH emerges as a pivotal technology in this landscape. It bridges the gap between the ubiquitous web browser and the powerful, secure command-line interface provided by SSH (Secure Shell). For IoT, this means that instead of requiring specific SSH client software on every device used for management, a simple web browser becomes the universal portal. This significantly lowers the barrier to entry for remote access, making it easier for teams to collaborate and for individuals to manage their personal IoT projects. The ability to initiate a "remoteiot web ssh download" of a client or access a web-based service means that secure, command-line control over IoT devices is just a few clicks away, empowering users to troubleshoot, configure, and update devices with unprecedented flexibility. This accessibility, combined with SSH's inherent security, makes Web SSH an indispensable tool for modern IoT deployments, ensuring operational continuity and responsiveness in an increasingly distributed environment.Understanding Web SSH: More Than Just a Terminal in Your Browser
At its core, Web SSH is an implementation that allows users to access the Secure Shell (SSH) protocol directly through a web browser. SSH itself is a cryptographic network protocol for operating network services securely over an unsecured network. It provides a secure channel over an unsecured network by using a client-server architecture, connecting an SSH client application with an SSH server. This secure connection is vital for remote command-line execution, file transfers, and secure network services. Web SSH takes this established security and extends it to the web. Instead of installing a dedicated SSH client like PuTTY or OpenSSH on your local machine, a Web SSH solution typically involves a server-side component that acts as a proxy, translating browser-based requests into SSH commands and relaying the SSH server's responses back to your browser. This means you get a fully functional terminal experience, complete with command history, text editing, and real-time output, all within a standard web page. The primary benefit for IoT is clear: manage devices from any internet-connected device with a browser, without the overhead of client software installation. This streamlined access doesn't compromise security; rather, it leverages the same robust encryption and authentication mechanisms that make traditional SSH so reliable, ensuring that your remote IoT interactions remain private and protected from eavesdropping or tampering.The Secure Handshake: SSH Protocol Fundamentals
The security of SSH, and by extension Web SSH, hinges on a sophisticated "handshake" process. When an SSH client (or a Web SSH proxy) attempts to connect to an SSH server on an IoT device, they first establish a secure channel. This involves several steps: 1. **Negotiation of Encryption Algorithms:** Client and server agree on a set of cryptographic algorithms (e.g., AES, ChaCha20-Poly1305) for encryption and decryption of data. 2. **Host Key Verification:** The server presents its unique host key. The client verifies this key against known keys to ensure it's connecting to the legitimate server and not an imposter (a "man-in-the-middle" attack). This is often the first warning you see when connecting to a new server. 3. **User Authentication:** Once the secure channel is established, the user authenticates themselves to the server. Common methods include: * **Password Authentication:** The user provides a username and password. * **Public Key Authentication:** This is the more secure and recommended method. The user generates a pair of cryptographic keys: a private key (kept secret on the client) and a public key (placed on the server). During authentication, the server challenges the client, which uses its private key to prove its identity without ever sending the private key over the network. This multi-layered approach ensures that data transmitted between your browser (via the Web SSH proxy) and your IoT device is encrypted and that only authorized users can gain access. This fundamental security is why SSH is the go-to protocol for remote administration, and why a secure "remoteiot web ssh download" solution is so critical for managing sensitive IoT infrastructure.Navigating the "RemoteIoT Web SSH Download" Landscape
When considering a "remoteiot web ssh download" solution, you'll find a diverse landscape of options, each with its own advantages and ideal use cases. Broadly, these solutions can be categorized into self-hosted and cloud-based offerings. Self-hosted solutions, such as Apache Guacamole or Shell In A Box, require you to set up and maintain your own server to act as the Web SSH gateway. This provides maximum control over your data and security configurations, making it a preferred choice for organizations with strict compliance requirements or those who prefer to keep all infrastructure in-house. However, it demands technical expertise for setup, maintenance, and ongoing security patching. Cloud-based Web SSH services, on the other hand, offer convenience and scalability. Providers like Termius, SecureCRT, or even specialized IoT platforms that embed Web SSH functionality, handle the infrastructure and security for you. These are often subscription-based and provide a ready-to-use interface, reducing the operational burden. They are ideal for smaller teams, individuals, or businesses that prioritize ease of deployment and don't want to manage server infrastructure. The choice between self-hosted and cloud-based depends heavily on your specific needs, technical capabilities, and security policies. Regardless of the type, the core functionality remains the same: providing secure, browser-based access to your remote IoT devices.Key Features to Look for in a Web SSH Solution
When evaluating a "remoteiot web ssh download" solution, several features stand out as crucial for effective and secure IoT management: * **Strong Authentication Methods:** Beyond basic password support, look for solutions that support public key authentication, multi-factor authentication (MFA/2FA), and integration with enterprise identity providers (e.g., LDAP, SAML). This is paramount for YMYL compliance and overall trustworthiness. * **Session Management and Logging:** The ability to monitor active sessions, disconnect rogue connections, and log all commands executed is vital for auditing, compliance, and incident response. * **File Transfer Capabilities:** While SSH itself supports SCP/SFTP for file transfers, a good Web SSH solution should offer an intuitive drag-and-drop interface or similar mechanism for uploading and downloading files directly through the browser. * **Customization and Theming:** For better user experience and branding, the ability to customize the terminal appearance, fonts, and colors can be a nice-to-have. * **Scalability:** For large IoT deployments, the solution should be able to handle numerous concurrent sessions and integrate with load balancing solutions. * **API Access:** An API allows for programmatic interaction, enabling automation of tasks or integration with other management tools. * **Security Audits and Compliance:** For enterprise use, look for solutions that undergo regular security audits and comply with relevant industry standards (e.g., ISO 27001, SOC 2). These features collectively contribute to a robust, secure, and user-friendly Web SSH experience, essential for the demanding environment of remote IoT device management.Step-by-Step: Getting Started with Your Remote IoT Web SSH Download
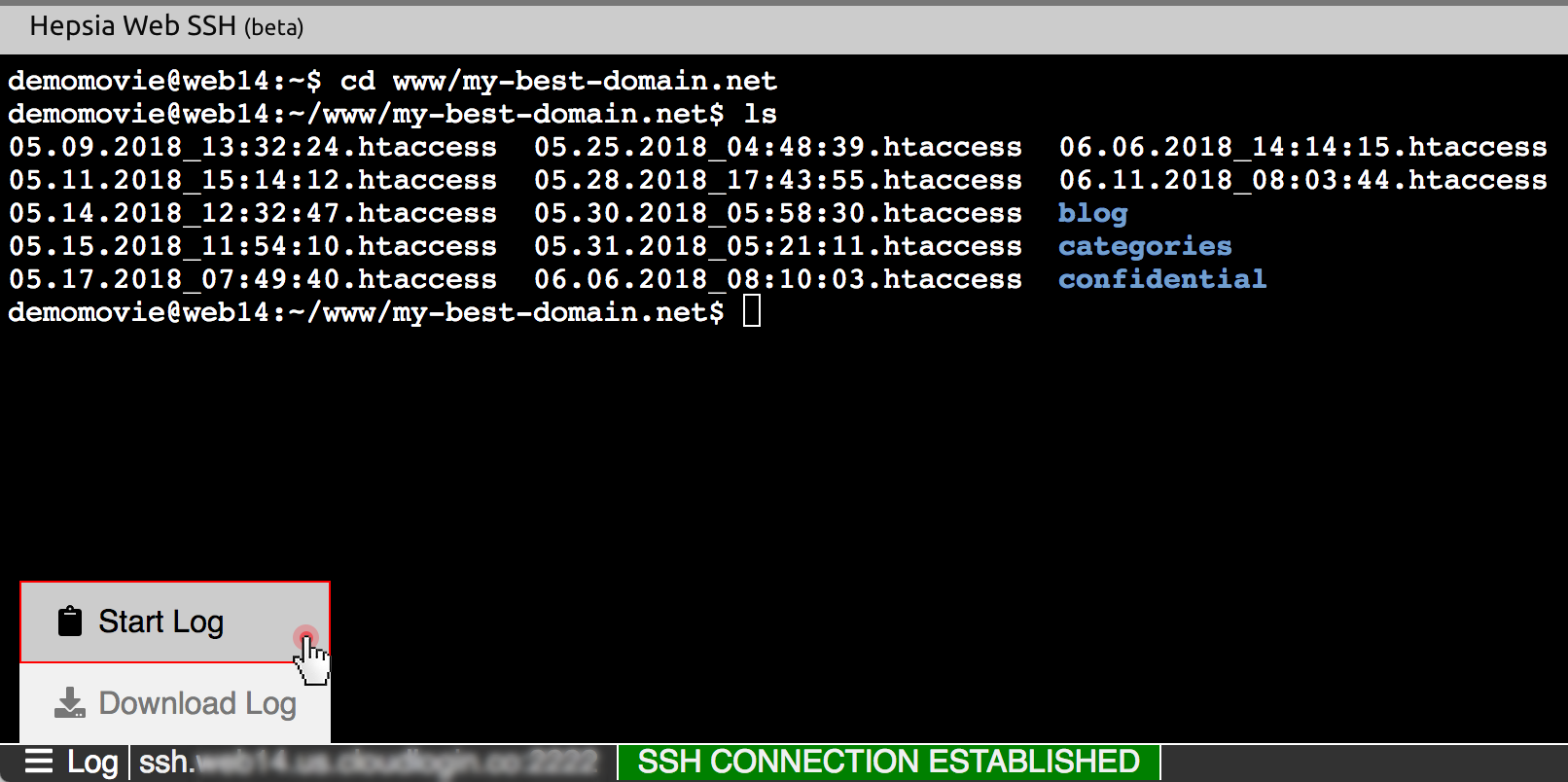
Embarking on your journey with a "remoteiot web ssh download" involves a few key steps, whether you choose a self-hosted or a cloud-based solution. For a self-hosted setup, the initial phase typically involves downloading the software package (e.g., a Docker image for Apache Guacamole, or source code for Shell In A Box) to your chosen server. This server will act as the gateway, so it needs to be accessible from your network and have appropriate firewall rules configured to allow incoming web traffic (usually on ports 80/443 for HTTP/HTTPS) and outgoing SSH traffic (port 22) to your IoT devices. Once downloaded, you'll proceed with installation, which often involves configuring a web server (like Nginx or Apache) to serve the Web SSH application and setting up a database for user authentication and session management. For cloud-based solutions, the process is generally simpler. You'll typically sign up for an account with the provider, which might involve a quick registration and potentially a "remoteiot web ssh download" of a small agent or client utility if the service requires it for specific network configurations. After account creation, you'll usually add your IoT devices to the platform, providing their IP addresses or hostnames and SSH credentials (usernames, passwords, or public keys). The platform then handles the secure connection to your devices, presenting you with a browser-based terminal ready for use. In both scenarios, the ultimate goal is to establish a secure, reliable connection that allows you to execute commands on your remote IoT devices as if you were directly connected.Best Practices for Initial Setup and Security
A secure initial setup is paramount when deploying any "remoteiot web ssh download" solution. Here are some critical best practices: * **Use Strong, Unique Passwords:** For all accounts, both on your Web SSH gateway and on your IoT devices, enforce complex passwords that are not reused elsewhere. * **Prioritize Public Key Authentication:** Whenever possible, disable password authentication on your IoT devices and rely solely on SSH public key authentication. This is significantly more secure and reduces the risk of brute-force attacks. Ensure your private keys are stored securely and never shared. * **Implement Multi-Factor Authentication (MFA):** If your Web SSH solution supports it, enable MFA for all user logins. This adds an extra layer of security, requiring a second verification step (e.g., a code from an authenticator app) in addition to the password or key. * **Least Privilege Principle:** Configure user accounts on your IoT devices with the minimum necessary permissions. Avoid using the 'root' user for daily operations; instead, create specific user accounts with limited sudo privileges. * **Regular Software Updates:** Keep your Web SSH gateway software, underlying operating system, and IoT device firmware updated to patch known vulnerabilities. This is a continuous process that is vital for maintaining security. * **Firewall Configuration:** Strictly configure firewalls on your Web SSH gateway and IoT devices to only allow necessary incoming and outgoing connections. For example, only allow SSH traffic from your Web SSH gateway's IP address to your IoT devices. * **Disable Unused Services:** On your IoT devices, disable any services or protocols that are not strictly necessary for their operation to reduce the attack surface. * **Change Default SSH Port:** While not a security silver bullet, changing the default SSH port (22) to a non-standard port can reduce the volume of automated scanning attempts. Adhering to these practices from the outset will significantly enhance the security posture of your remote IoT infrastructure and ensure the trustworthiness of your "remoteiot web ssh download" solution.Security First: Protecting Your Remote IoT Infrastructure
In the realm of IoT, where devices are often deployed in exposed environments and can become entry points for malicious actors, security cannot be an afterthought. When leveraging a "remoteiot web ssh download" solution, the emphasis on robust security measures becomes even more critical. The very convenience of browser-based access, if not properly secured, can become a vulnerability. Beyond the foundational SSH encryption, which protects data in transit, comprehensive security encompasses several layers. This includes implementing strong, unique passwords for all accounts – both on your Web SSH gateway and on individual IoT devices. Even better, moving beyond passwords to public key authentication for SSH connections dramatically reduces the risk of brute-force attacks and credential theft. Furthermore, enabling multi-factor authentication (MFA) for access to your Web SSH platform adds a crucial layer of defense, ensuring that even if a password is compromised, unauthorized access is still prevented. Regular security audits of your Web SSH server and IoT devices are essential to identify and remediate vulnerabilities before they can be exploited. This proactive approach, coupled with strict firewall rules that limit access to only necessary ports and IP addresses, forms a formidable defense. Remember, the goal is not just to establish a connection but to establish a *secure* connection that protects your valuable IoT data and prevents your devices from being weaponized in botnets or used as pivots for further network intrusions. The trustworthiness of your entire IoT ecosystem hinges on the integrity of your remote access methods.Practical Applications and Use Cases for Remote IoT Web SSH
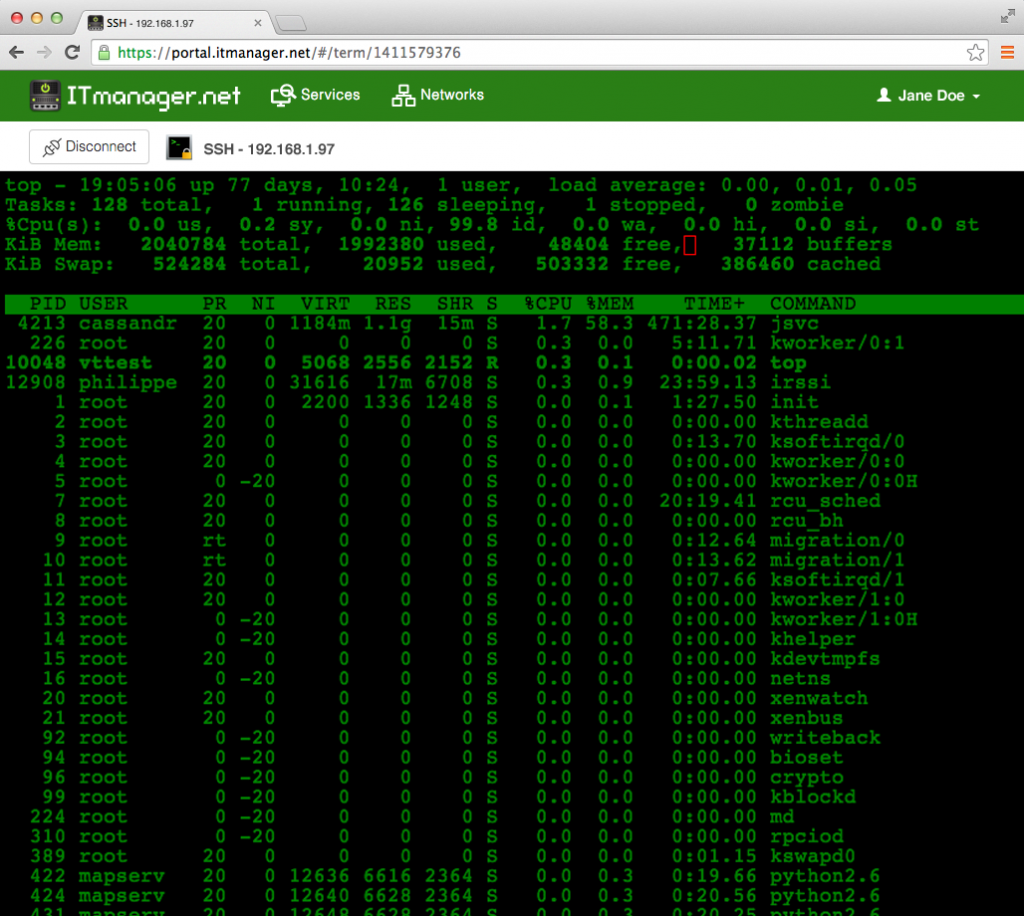
The utility of a "remoteiot web ssh download" extends far beyond simple connectivity, offering a versatile toolkit for a myriad of IoT management tasks. One of its most common and critical applications is **troubleshooting**. When an IoT device malfunctions or goes offline, a Web SSH connection allows engineers to log in remotely, inspect logs, check service statuses, and diagnose issues without dispatching personnel to a potentially distant or inaccessible location. This drastically reduces downtime and operational costs. Another vital use case is **software updates and patch management**. IoT devices, like any computing system, require regular updates to patch security vulnerabilities and introduce new features. Web SSH provides a secure channel to upload firmware updates, execute installation scripts, and reboot devices, ensuring the entire fleet remains secure and up-to-date. This is especially crucial for maintaining the trustworthiness and security of your devices over their lifecycle. Beyond maintenance, Web SSH facilitates **data retrieval and configuration management**. Developers can use it to pull sensor data logs for analysis, modify configuration files on the fly, or deploy new application code to edge devices. For example, adjusting a threshold for a temperature sensor or changing the frequency of data transmission can be done instantly from a web browser. Furthermore, **remote command execution** enables powerful automation. Scripts can be run to restart services, collect diagnostic information, or even reconfigure network settings across multiple devices simultaneously. In scenarios requiring real-time **monitoring**, Web SSH can be used to view live system metrics, process lists, and network activity, providing immediate insights into device performance and health. These practical applications underscore why a secure and accessible "remoteiot web ssh download" solution is an indispensable asset for any serious IoT deployment.Overcoming Challenges: Common Issues and Solutions
While the "remoteiot web ssh download" concept offers immense benefits, users may occasionally encounter challenges. Understanding common issues and their solutions is key to maintaining seamless remote access. One frequent problem is **connectivity issues**. This can stem from network problems (e.g., device offline, firewall blocking SSH port 22, incorrect IP address), or issues with the Web SSH gateway itself (e.g., gateway server is down, misconfigured proxy). Always start by verifying the device's network connectivity and ensuring the correct port is open. Another common hurdle is **authentication failures**. This typically occurs due to incorrect credentials (wrong username or password), or issues with SSH keys (e.g., private key not correctly loaded, public key not authorized on the IoT device, incorrect permissions on key files). Double-check usernames, ensure private keys match the public keys on the device, and verify file permissions (e.g., `chmod 600 ~/.ssh/id_rsa`). **Performance considerations** can also arise, especially with high-latency connections or when dealing with large amounts of terminal output. A slow connection can make the terminal feel sluggish and unresponsive. While not always fixable, optimizing network routes or using a Web SSH solution with efficient data compression can help. Finally, **terminal display issues** (e.g., garbled characters, incorrect line wrapping) can happen if the terminal emulation settings in the Web SSH client don't match the remote device's environment. Adjusting character encoding or terminal type settings within the Web SSH interface can often resolve these.Troubleshooting Your Remote IoT Web SSH Connection
When your "remoteiot web ssh download" connection isn't behaving as expected, a systematic troubleshooting approach can save significant time. 1. **Verify Basic Connectivity:** Can you ping the IoT device from the Web SSH gateway server? Can the gateway server reach port 22 on the IoT device (e.g., using `telnetThe Future of Remote IoT Management: Trends and Innovations
The landscape of remote IoT management, empowered by solutions like "remoteiot web ssh download," is continuously evolving. Several key trends and innovations are shaping its future, promising even more sophisticated and secure ways to interact with distributed devices. One significant trend is the **deeper integration with cloud platforms and IoT ecosystems**. Expect Web SSH functionalities to become seamlessly embedded within broader IoT management dashboards, offering a unified control plane that combines device provisioning, data visualization, and remote command execution. This reduces context switching and streamlines workflows for developers and operators. Another area of innovation lies in **enhanced security features**. As cyber threats grow more sophisticated, future Web SSH solutions will likely incorporate advanced threat detection, anomaly behavior analysis, and even AI/ML-driven security insights to proactively identify and mitigate potential compromises. This could include real-time monitoring of command execution for suspicious patterns or automated blocking of unusual login attempts. The use of hardware security modules (HSMs) for key management and secure boot processes on IoT devices will also become more prevalent, further bolstering the integrity of remote connections. Furthermore, we'll see an increased focus on **edge computing integration**. As more processing moves closer to the data source, Web SSH will be crucial for managing these powerful edge devices, deploying containerized applications, and orchestrating complex workloads directly at the network edge. This will allow for more responsive and efficient data processing, reducing reliance on constant cloud connectivity. Finally, the development of **standardized APIs and open-source contributions** will foster greater interoperability and innovation within the Web SSH space, making it easier for organizations to customize and integrate these tools into their existing IT infrastructure, ensuring that the "remoteiot web ssh download" remains at the forefront of secure and efficient IoT device management.Conclusion
The journey through the world of "remoteiot web ssh download" reveals it as a cornerstone of modern IoT device management. We've explored how Web SSH provides a secure, flexible, and accessible gateway to your distributed devices, transforming the challenges of remote operations into manageable tasks. From understanding its fundamental security protocols to navigating the diverse landscape of available solutions, and from step-by-step setup guides to critical security best practices, it's clear that this technology is indispensable for maintaining the integrity, functionality, and trustworthiness of your IoT infrastructure. The ability to troubleshoot, update, and manage devices from any web browser, securely and efficiently, empowers organizations to scale their IoT deployments with confidence. As the IoT ecosystem continues its rapid expansion, the role of robust and accessible remote management tools like Web SSH will only grow in importance. By embracing these solutions and adhering to the highest security standards, you can unlock the full potential of your IoT devices, ensuring they operate reliably and securely. What are your experiences with remote IoT management? Have you used Web SSH solutions, and what challenges or successes have you encountered? Share your insights in the comments below, and don't hesitate to explore more of our articles on securing and optimizing your IoT deployments. Your journey towards a more connected and controlled future starts here.Related Resources:

Detail Author:
- Name : Roosevelt Witting
- Username : kilback.rashawn
- Email : wroob@towne.com
- Birthdate : 1975-02-13
- Address : 52790 Octavia Ports Apt. 588 Emilianoborough, CA 70133-3551
- Phone : 1-984-226-2267
- Company : Jast-Rowe
- Job : Manicurists
- Bio : Quaerat architecto soluta tempora animi sequi omnis. Perferendis mollitia totam a omnis quia neque. Nemo iste placeat et nam dicta nesciunt.
Socials
twitter:
- url : https://twitter.com/cristal.runolfsdottir
- username : cristal.runolfsdottir
- bio : Nisi cupiditate minus molestias laborum. Vel temporibus ullam maiores vel. Incidunt aut impedit sint eaque labore.
- followers : 3446
- following : 1355
instagram:
- url : https://instagram.com/cristal_runolfsdottir
- username : cristal_runolfsdottir
- bio : Commodi eos recusandae et est provident. Velit sit fuga saepe id ut.
- followers : 400
- following : 2064
facebook:
- url : https://facebook.com/cristal_runolfsdottir
- username : cristal_runolfsdottir
- bio : Qui eos rem corporis est quas.
- followers : 764
- following : 2755
tiktok:
- url : https://tiktok.com/@cristal_real
- username : cristal_real
- bio : Voluptas nobis rerum consequatur earum.
- followers : 5422
- following : 1349